Discover, scan and monitor any online assets
With Netlas, it takes just a few minutes to build a scope and investigate it.
Thousands of IT security experts use Netlas.io as a reliable source of information for their day‑to‑day operations






















Netlas has landed on something that’s specifically new and different, especially as a standalone offering, and has a multitude of use cases.
I’m building and running a security program at a startup and I can’t afford a lot of the larger tools/subscriptions that would give me access to the data Netlas offers.

Jeff Geiger
Senior Director of Security at Selfbook
Today I tested @Netlas_io (since I needed a replacement for @securitytrails).
Its worth the money — some of you know I am heavily into automation, data quality is important. When it comes to price/performance ratio — Netlas is currently the way to go.

Damian Strobel
Founder of dsecured.com
Netlas has been highly effective for our threat-hunting efforts. In particular, my team has found the response search invaluable. We use it for locating potential text strings, keywords, or filenames related to malicious domains. Another use case is to identify possible subdomains associated with malicious domains.

Hieu (Hieupc) Ngo
Threat Hunter at NCSC Viet Nam
🙌 @netlas_io A valuable tool and a fantastic product that’s making life easier for pentesters and bug hunters!
🐞🔍 With its advanced reconnaissance and automation features, Netlas is a game-changer for identifying security threats and vulnerabilities.

Begin n Bounty
Practical bug bounty tips channel
Netlas has led me to discover numerous new assets, facilitating successful subdomain takeovers. Additionally, I’ve been using Netlas for identifying vulnerable services using keywords, titles, or favicon hashes, a strategy that has yielded significant success. I’ve found Netlas to be the most cost-effective and reliable option.

Jayesh Madnani
CEO and Hacker in charge @ EIS
I tested Fofa, Hunter, Shodan, but Netlas gives absolutely accurate results. Suppose if I search for swagger-ui then I will get proper results regarding my query and the best thing is, that those urls are working. If I do the exact same thing in other IoT search engines, only 70-80% of their results work, and here I see 95%!

Chirag Artani
Penetration tester, bug bounty hunter
Essential Netlas Tools
Apps for reconnaissance, non-intrusive security assessment, and security‑related research

Powerful Search Tools
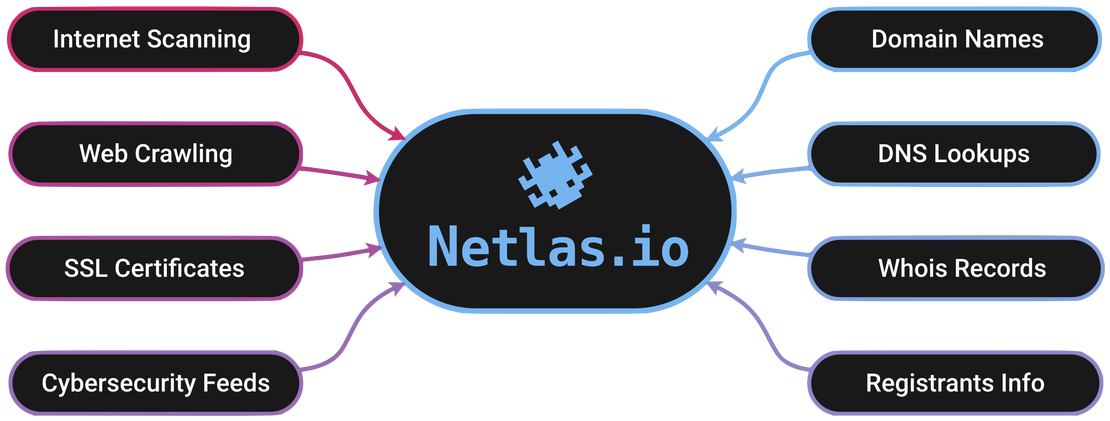
Search Tools enable you to explore Netlas data with advanced search capabilities, leveraging flexible conditions and operators. Cross-mapping between collections adds context and depth to your queries, enabling you to search effortlessly by WHOIS fields, GeoIP data, DNS registry information, protocol attributes, technology and product identifiers, and even known vulnerabilities.
Search for: Internet Scan Data, DNS Records, IP WHOIS, Domain WHOIS, and SSL Certificates.
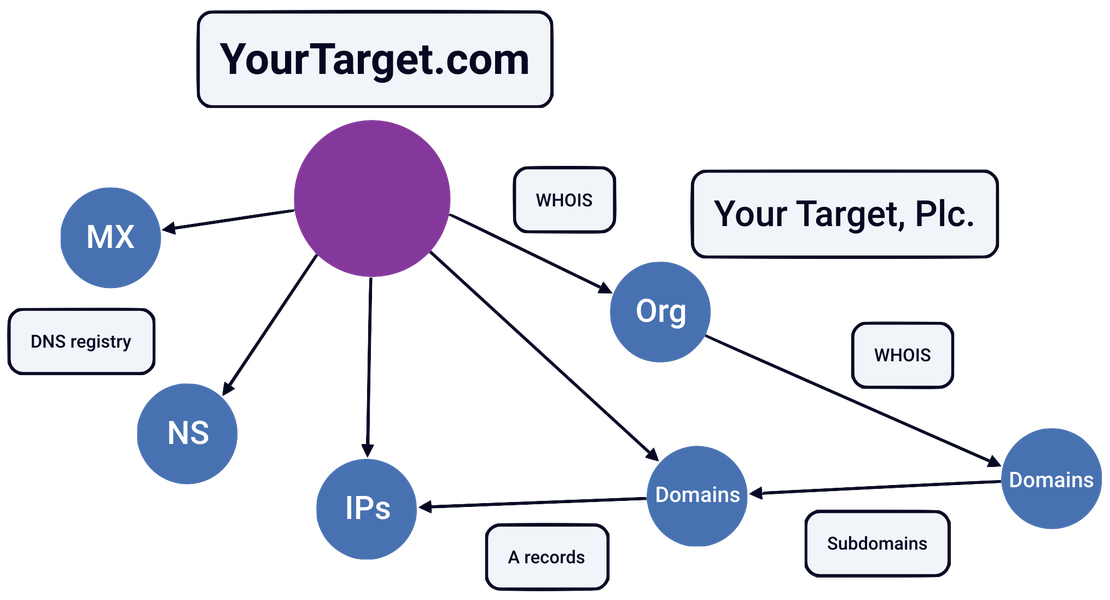
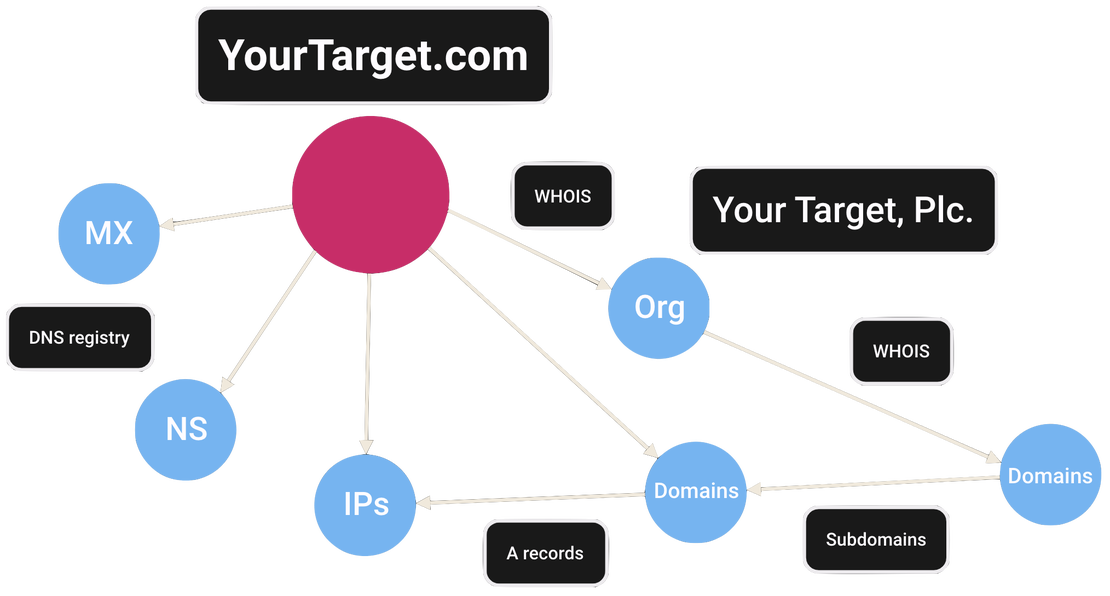
Attack Surface Discovery Tool
This intuitive solution enables you to explore relationships between various entities such as domains, IPs, services, SSL certificates, and more. Simply click and add objects to your attack surface map, dynamically building a comprehensive view of your digital footprint. Perfect for identifying shadow IT, mapping infrastructure, and exposing hidden risks, all with an easy-to-use, interactive interface.
Discovery Tool →
Super-Fast On-Demand Scanner
This easy-to-use network scanner enables you to quickly gather detailed insights about any attack surface while maintaining complete discretion. Collect data on internet-facing assets without interacting with the target, ensuring privacy and compliance. Results are securely stored and accessible only to you, providing a rapid, clear view of services, technologies, and configurations to support informed decision-making.
Private Scanner →

Datastore & Streaming API
Netlas Datastore provides structured datasets, including DNS Records, IP WHOIS, Domain WHOIS, and more. For those needing bulk access to Internet Scan Data, daily scan volumes can be downloaded as JSON files, or real-time data can be accessed through the Streaming API, enabling seamless and reliable integration into your data-driven operations.
Datastore →What makes Netlas a great choise?
Superior scanning technology and powerful search tools
Looking for more reasons?
Netlas IoT Search Engine
Explore comprehensive internet scan data
The most in-demand tool for cybersecurity and OSINT professionals, Netlas IoT Search Engine provides data on the majority of publicly available services. Enriched with WHOIS, DNS, and other contextual information, it allows users to search across thousands of fields, delivering unmatched depth and accuracy for your investigations.
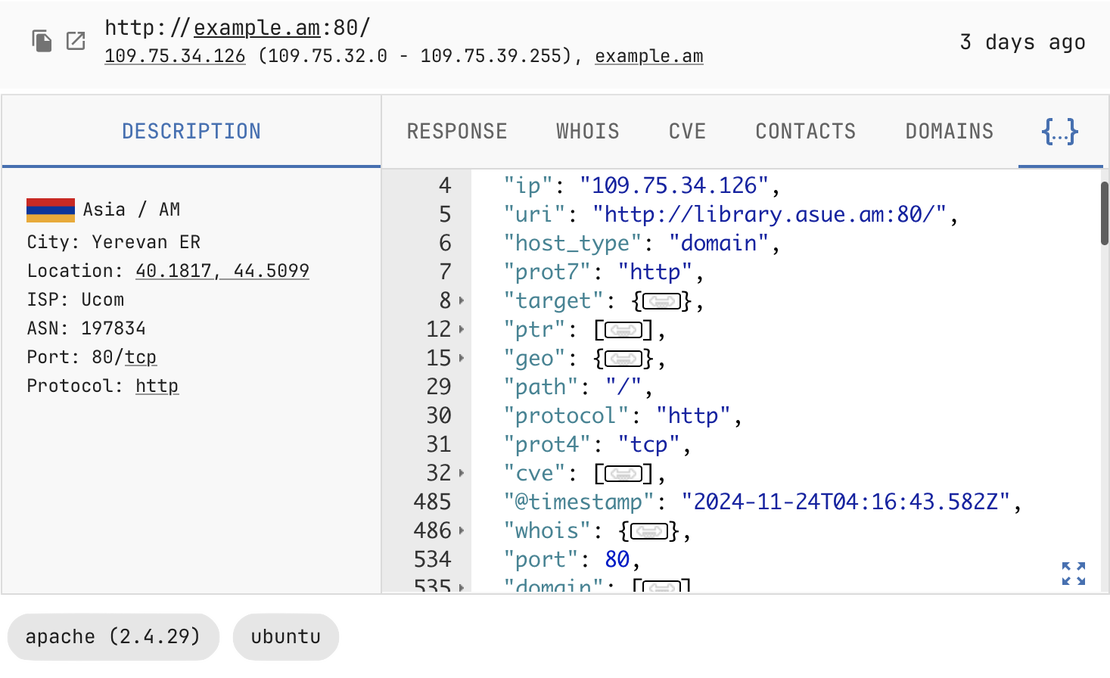
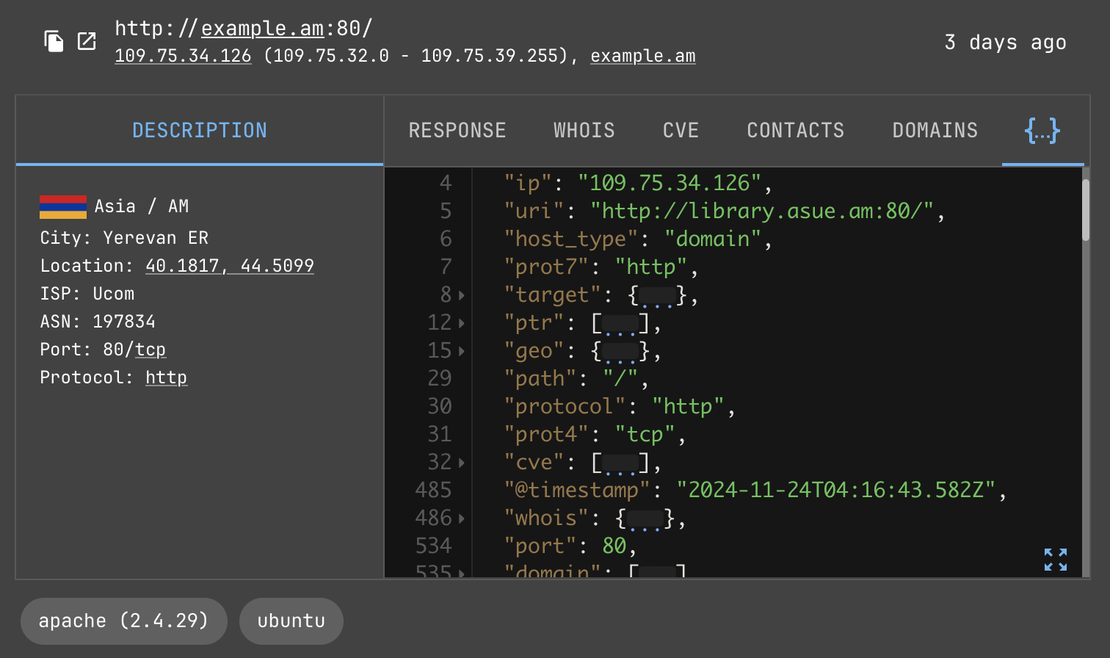
WHOIS, Geo, and other Metadata
Understand the who, where, and what of online assets
Netlas’s platform provides access to comprehensive metadata, delivering valuable context for analyzing internet-connected assets. With geolocation details, provider information, WHOIS data, and more, users can enrich their investigations, uncover asset origins, understand ownership, and identify relationships across the online ecosystem.
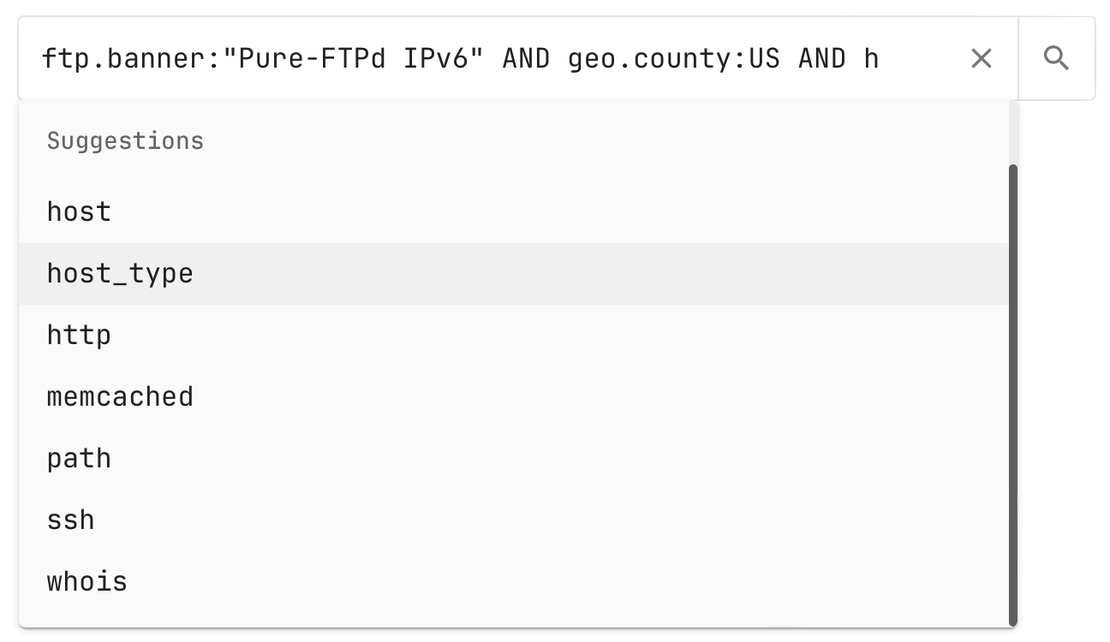
Advanced Query Language
Use logical operators, wildcards, regexp, fuzzy & proximity searches
Netlas provides a versatile query language that’s available across all its search tools, enabling users to refine searches and extract the most relevant results. With logical operators, wildcard matching, regular expressions, and advanced features like fuzzy and proximity searches, you can precisely target the data you need. Whether you’re analyzing WHOIS records, SSL certificates, or internet scan data, these powerful capabilities make it easy to navigate complex datasets and uncover actionable insights.
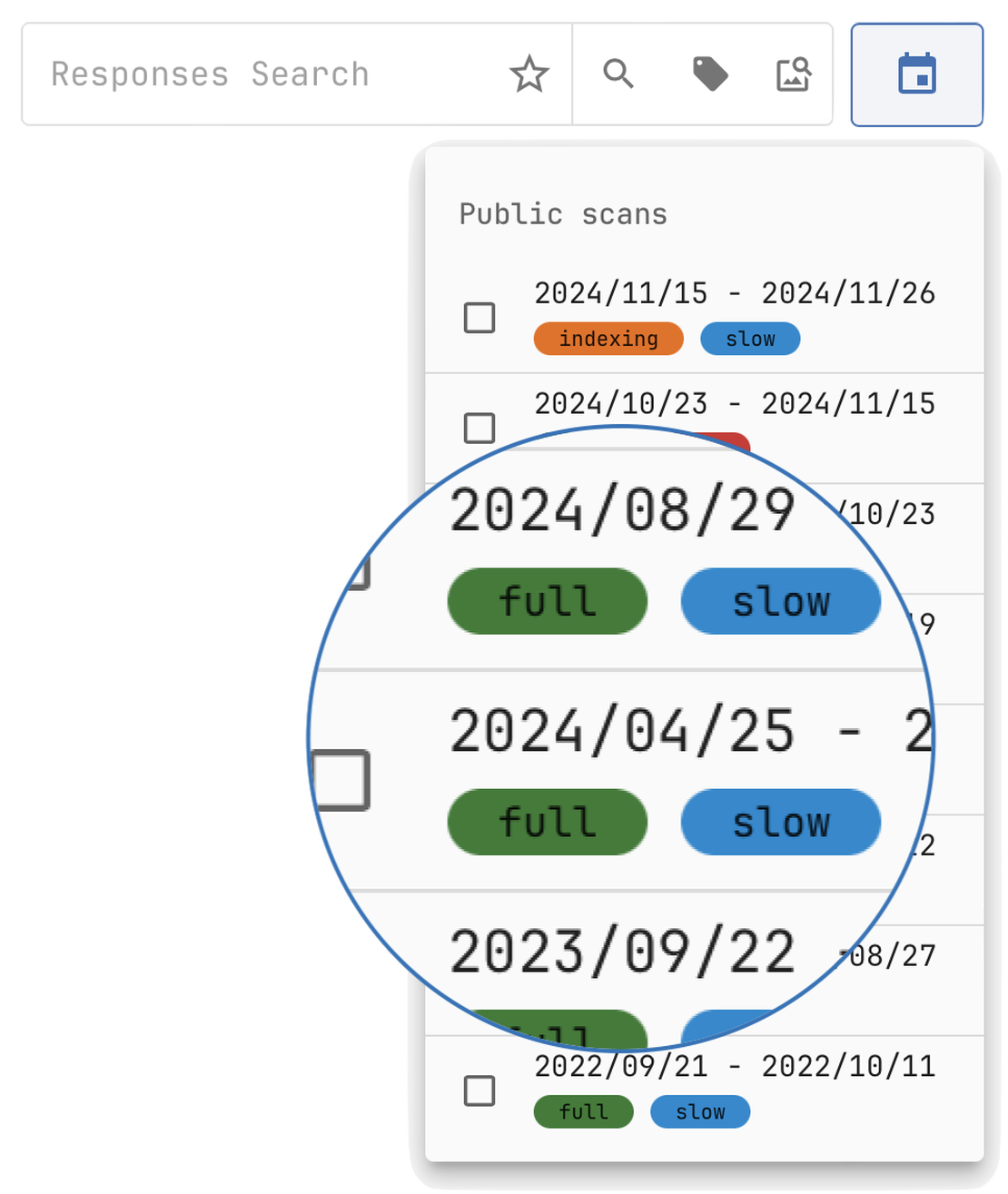
Historical Data Access
Track Changes and Trends Over Time
Netlas provides access to historical records for all data collections, except SSL certificates, enabling users to analyze how assets, configurations, and services have evolved. This historical perspective is invaluable for tracking changes in an organization’s digital footprint, spotting potential vulnerabilities, and conducting comprehensive assessments of evolving risks. SSL certificates, however, inherently contain validity periods and expiration details, making additional historical data unnecessary.
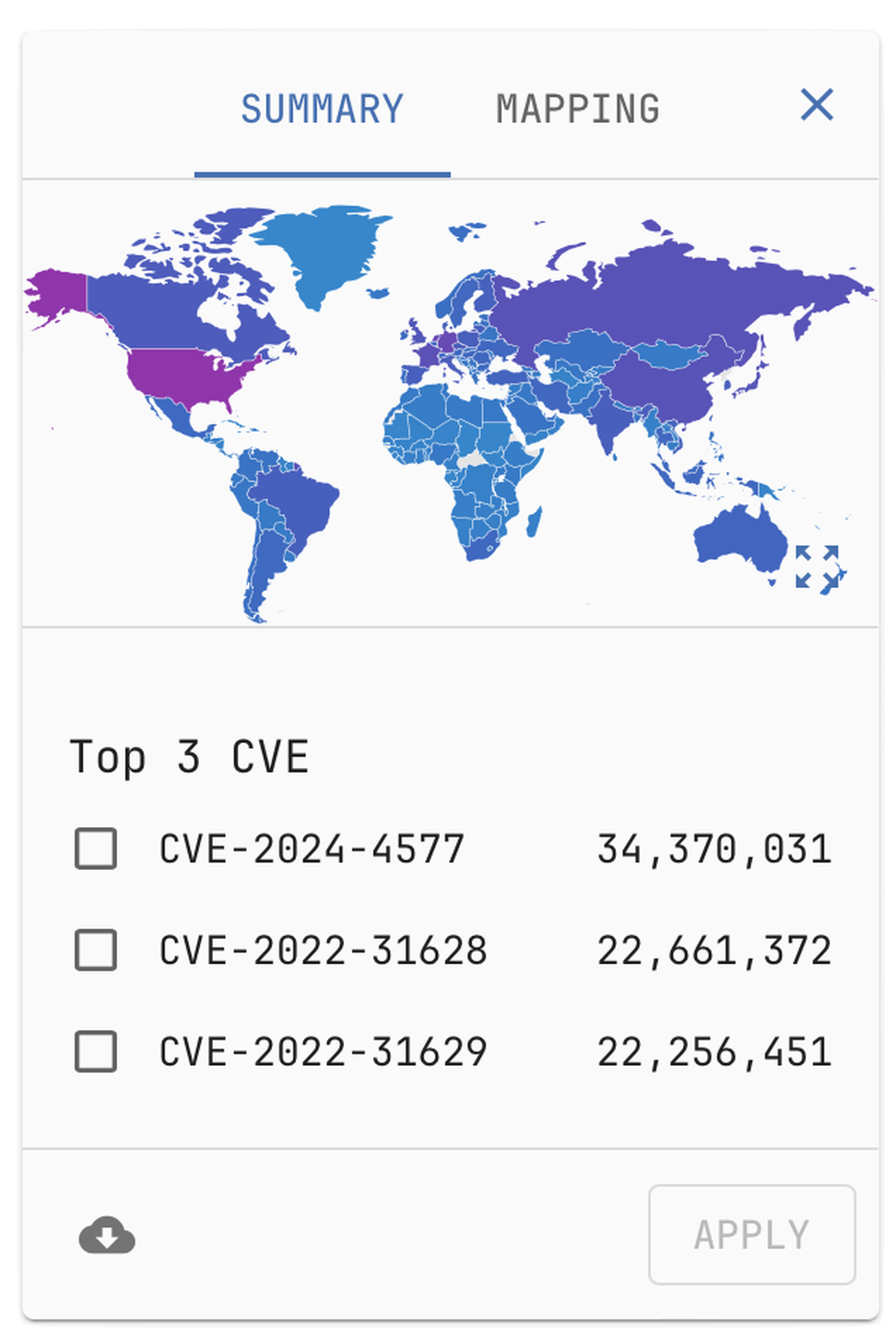
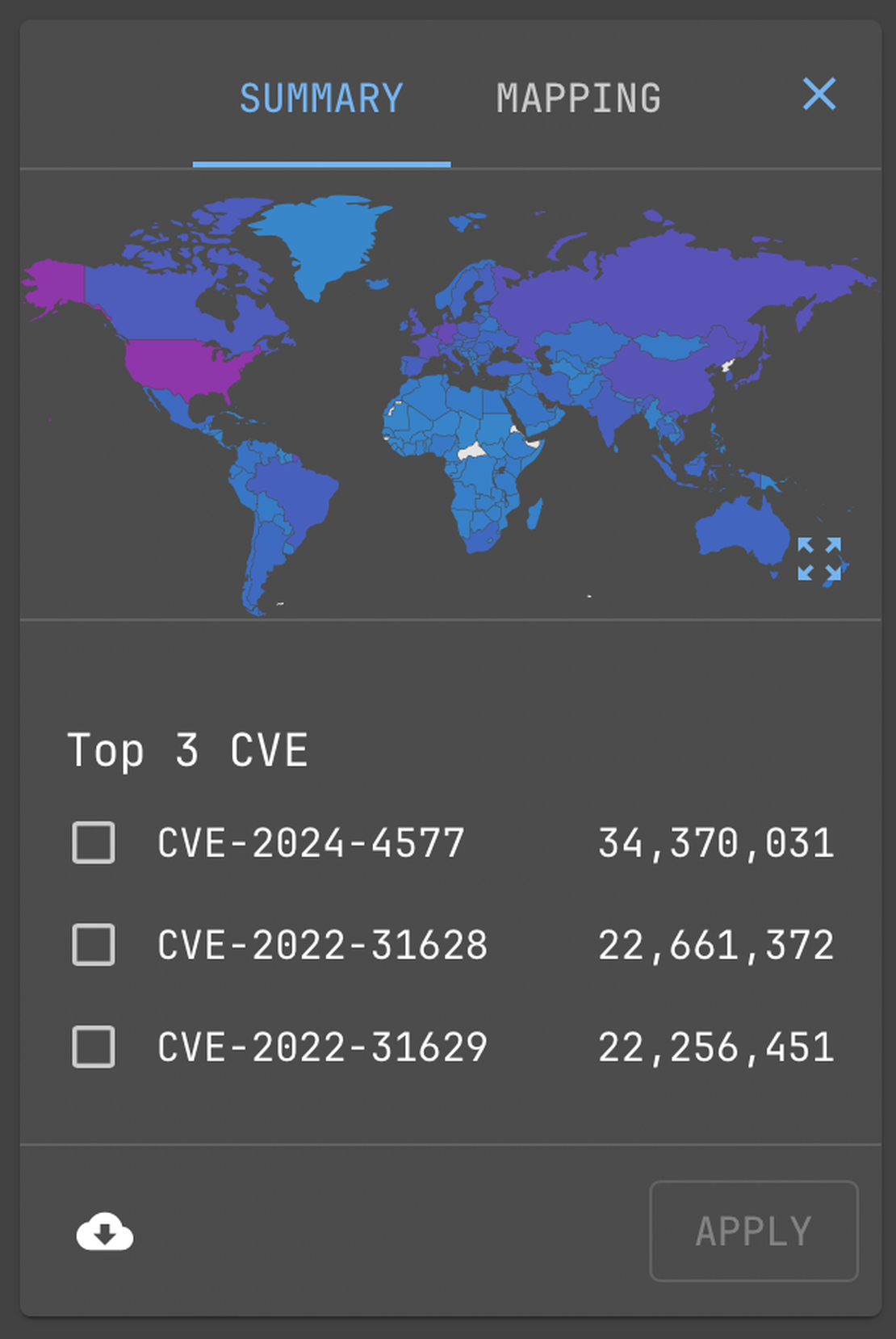
Global Security Data
Cybersecurity research goes global with Netlas.io
The passive scan method used by Netlas.io identifies products and technologies from about 3 out of 4 host responses. In about a third of cases, the product version is also recognized. Vulnerabilities are identified based on product versions according to the U.S. Government National Vulnerability Database and updated with each new scan. Netlas.io also provides information about exploits availability.
Netlas Integrations
Fetch Netlas data from apps you already use
Made for Automation
You can easily integrate Netlas in your own app
Full-REST API
The Netlas API is available to all registered users. Download the OpenAPI specification and use it with your favorite client to interact with the API.
DocumentationNetlas SDK & Examples
Explore the Netlas GitHub repository for usage examples and an SDK for Python. Support for other programming languages will be added in the future.
Github RepositoryDevelopers Are Welcome!
The Netlas team encourages independent development of Netlas-based tools—ranging from simple scripts to complex automation solutions.
Apply for Free LicenseCommand-Line Friendly
Use Netlas to orchestrate your needs. Utilize it in your automation scripts for data search and enrichment
The Netlas Python SDK includes a command-line interface. If you have Python installed, just use the Python package installer to setup the SDK. Once you have completed that step, you can interact with Netlas.io using the command-line.
user@host ~ % netlas
Usage: netlas [OPTIONS] COMMAND [ARGS]...
Options:
-h, --help Show this message and exit.
Commands:
count Calculate count of query results.
download Download data.
host Host (ip or domain) information.
indices Get available data indices.
profile Get user profile data.
savekey Save API key to the local system.
search (query) Search query.
stat Get statistics for query.

Top 10 Critical Threat Actors to Watch in 2026: Ransomware, APTs & Defensive Strategies
2026 threat landscape: 10 top ransomware, APT and extortion groups. TTPs, resilience after takedowns, and defenses: patching, identity, backups, detection.
January 23, 2026
→
Bug Bounty 101 - A Complete Bug Bounty Roadmap for Beginners (2026)
Practical 2026 bug bounty roadmap for beginners: choosing targets, recon, web/API bugs, manual testing and writing reports that get paid
January 16, 2026
→
Supply Chain Attack - How Attackers Weaponize Software Supply Chains
Explains how software supply chain attacks subvert trust in open source, CI/CD and registries, and how SBOM, provenance and signed builds mitigate risk.
December 26, 2025
→