Best Honeypots for Detecting Network Threats
June 8, 2025
10 min read
Typically, this blog focuses on tools designed for offensive security. Today, however, we’re shifting gears to explore the defensive side: the fascinating world of honeypots.
Tracking malicious actors can be an exhilarating and rewarding pursuit, and honeypots are one of the most effective tools for this purpose. These deceptive systems are designed to lure attackers and gather critical intelligence on their tactics and behavior.
In this article, we’ll break down what a honeypot is, how it operates, and provide you with a detailed list of the 20 best free and open source honeypots for capturing valuable threat intelligence when attackers engage with your decoy systems.
Honeypots and Their Types
Before diving into the specifics, let’s take a step back to explore the foundational concepts that make honeypots such a powerful defensive strategy.
- Honeypot
- is a deliberately deployed computer system, service, or application that simulates vulnerable behavior in order to attract, detect, and analyze unauthorized or malicious activity. It is isolated from production environments and monitored to collect data on attack techniques, tools, and intent.
When a cyber attacker engages with the honeypot, it captures essential data about the intruder’s methods, objectives, and sometimes even their identity. This intelligence is incredibly valuable for understanding the threat landscape.
How Does Honeypot Works?
A honeypot operates as a decoy system, strategically vulnerable and typically hosted on virtual machines or cloud servers that are part of a network yet remain isolated and under close surveillance by system and network teams. To attract malicious actors, honeypots exhibit deliberate vulnerabilities — flaws that attackers are meant to find and exploit.
These vulnerabilities might include security gaps within an application or system weaknesses such as open ports that aren’t needed, obsolete software versions, simple passwords, or outdated, unpatched operating systems.
Once an attacker finds these vulnerabilities, they often try to break into the system and gain more control — aiming to take over the device or application. Meanwhile, everything they do is quietly recorded by the honeypot — giving security teams valuable data to improve defenses and, in serious cases, report the incident to law enforcement.
Detecting Honeypots
Can attackers tell when they’re inside a honeypot? Absolutely.
Technically skilled users may notice subtle indicators that suggest they’ve entered a decoy environment. Tools like Shodan’s Honeyscore, which estimates the likelihood of an IP address being a honeypot, or Netlas with its rich software tagging capabilities, can aid in detection.
Let’s take a closer look at how to identify honeypots using Netlas.
Honeypots often emulate multiple services on a single port to attract a wide variety of malicious activity. While this approach may fool automated scanners, it’s typically easy for humans to spot. Consider the following response:
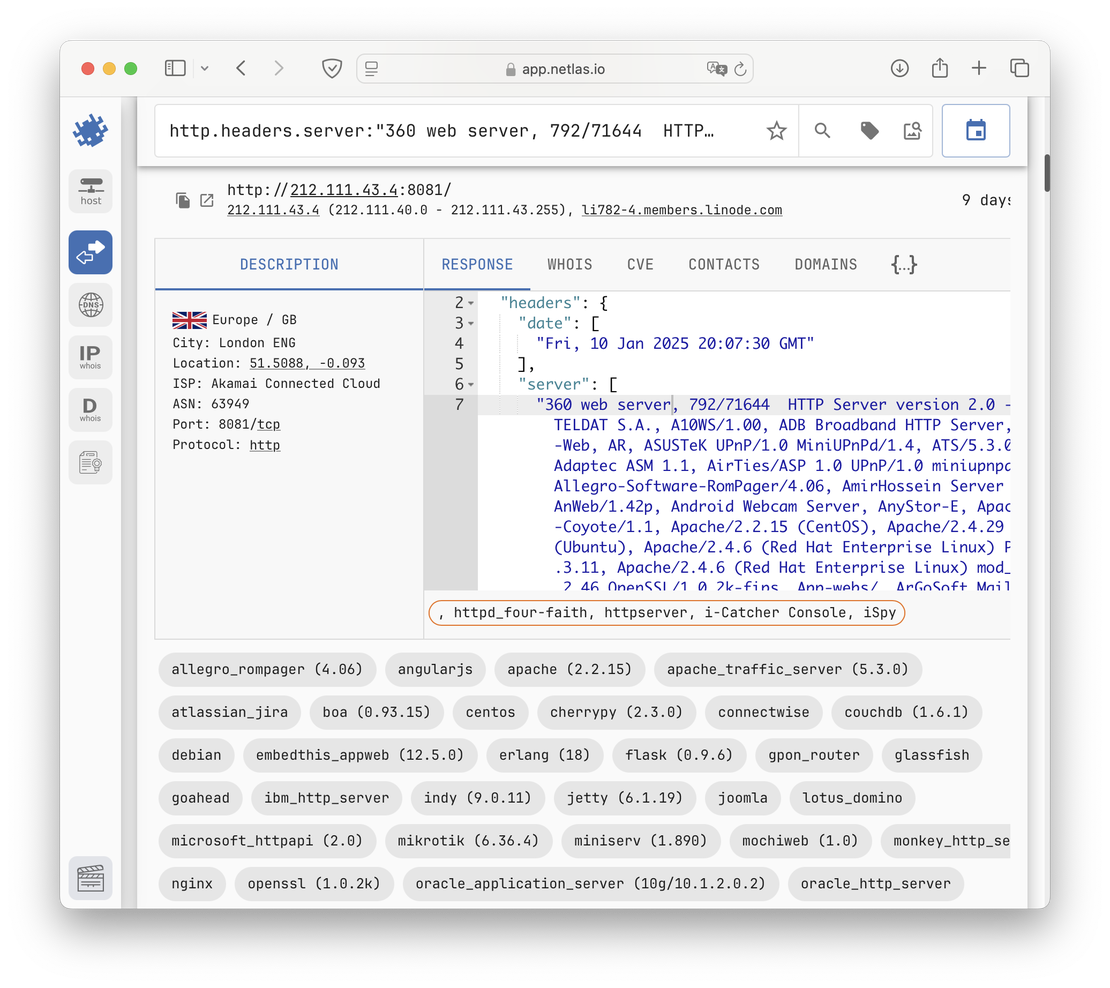
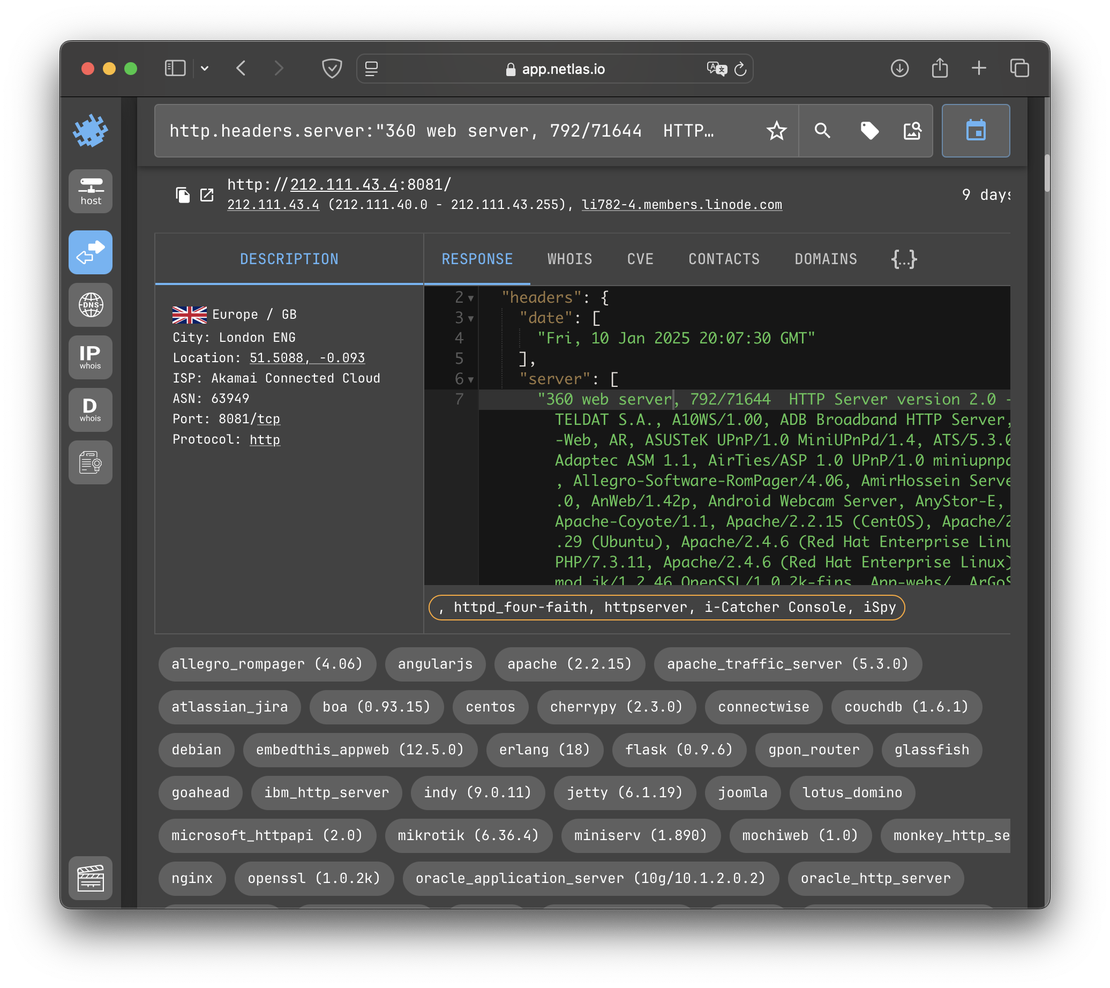
The server header lists an unrealistic combination of technologies. The chance that all of this software is genuinely running on a single service is effectively zero — strongly suggesting it’s a honeypot configured to lure attackers.
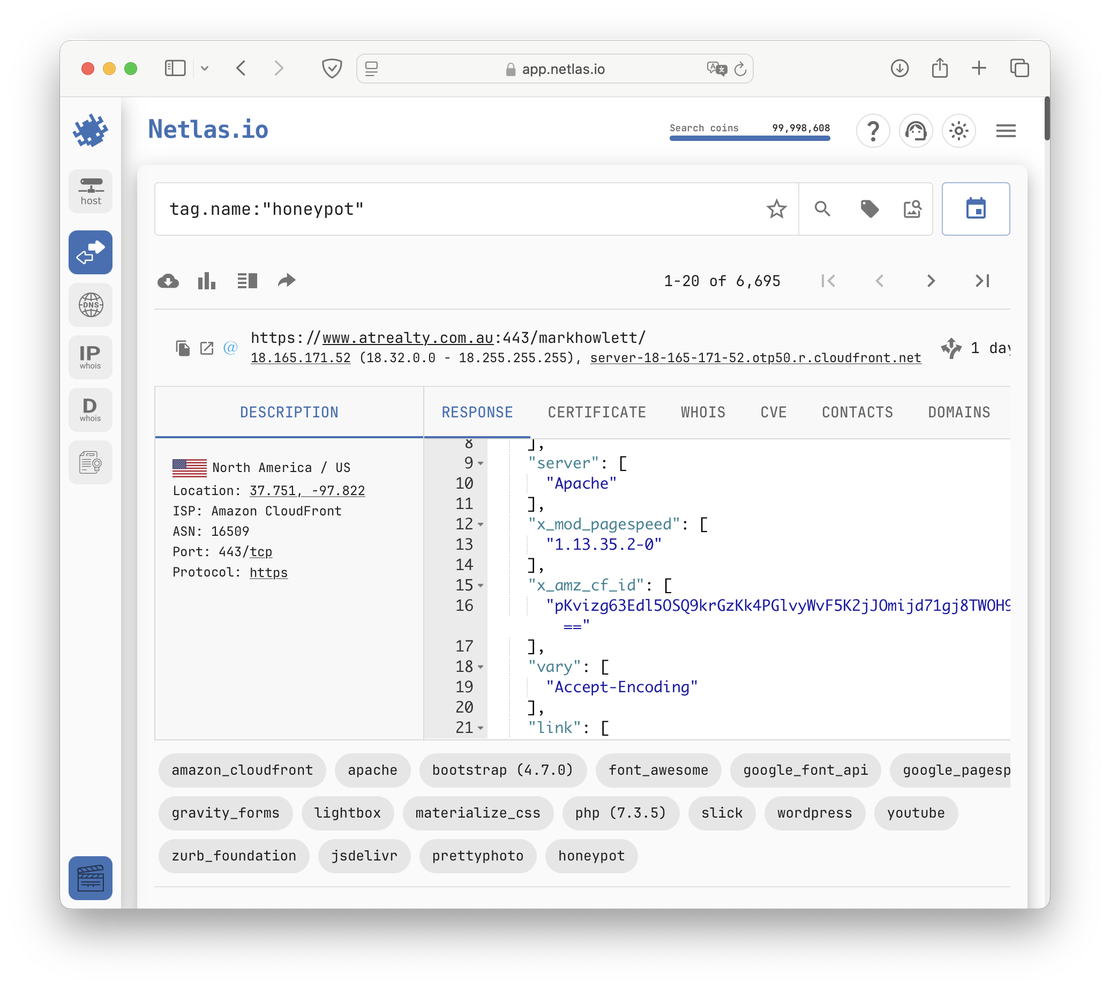
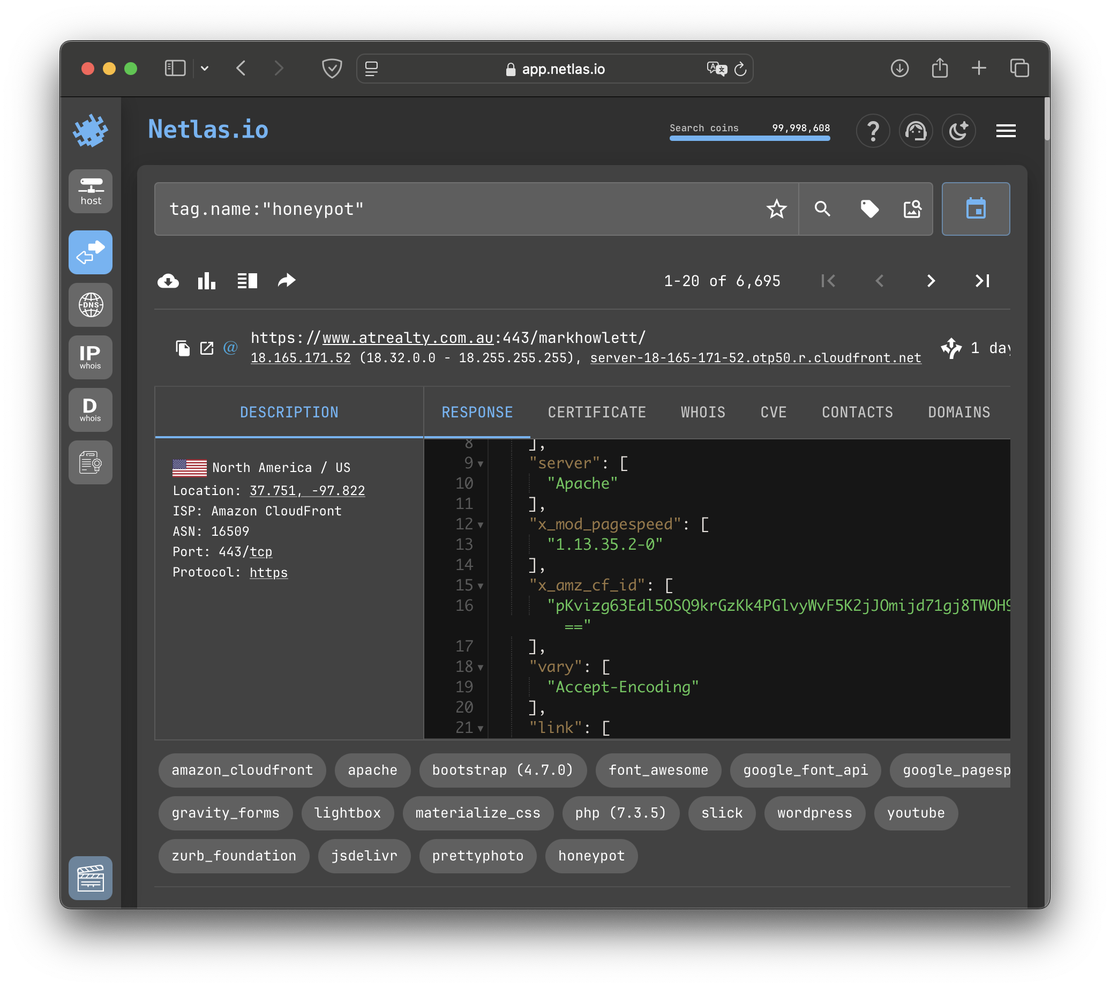
Another method is to use the honeypot tag. This tag highlights systems identified as honeypots by Netlas’s automated classification.
Simply run the following query in the Responses Search:
tag.name:honeypotTo get a list of all honeypots detected by the search engine. Something like the following image.
Honeypot Types by Purpose
The primary purpose of using honeypots is to detect emerging attack techniques, collect detailed incident data, and use that intelligence to improve overall network defenses.
Request Your Free 14-Day Trial
Submit a request to try Netlas free for 14 days with full access to all features.
Honeypots are generally categorized by their intended purpose into two main types:
- Research Honeypot: Typically deployed by researchers, cybersecurity teams, or academic institutions, these honeypots are used to study attacker behavior, tools, and methodologies in depth. The insights gained are often used for threat intelligence, security research, or academic analysis.
- Production Honeypot: Integrated into active organizational networks, production honeypots aim to detect and analyze real-time attacks against live infrastructure. They serve as an early warning system, helping to identify intrusions and improve local defenses.
Importantly, the same honeypot software can function as either a research or production system, depending on how it is configured and the context in which it is deployed.
Honeypot Types by Interaction Level
By interaction level, honeypots are classified based on how much functionality they offer to attackers:
- Low-Interaction Honeypots simulate only specific services (e.g., a fake SSH banner or limited HTTP response). They are lightweight, safe, and easy to deploy, but offer limited insight into attacker behavior.
- Medium-Interaction Honeypots emulate more realistic environments — such as partial shell access or protocol responses — without exposing a full operating system. They strike a balance between realism and operational safety.
- High-Interaction Honeypots provide attackers with full access to a real or virtualized system, capturing detailed behavior and post-compromise activity. They require strict isolation and careful monitoring due to the increased risk.
Common Honeypot Applications in Cybersecurity
Although there are numerous types of honeypots, here are a few of the most widely recognized:
- Spam Honeypot: Often referred to as a spam trap, this type of honeypot is designed to capture spammers before they reach legitimate email inboxes. Typically, they feature open relays to attract attacks and are integrated with Real-time Blackhole Lists (RBLs) to prevent malicious traffic.
- Malware Honeypot: Set up to emulate vulnerable applications, APIs, and systems, malware honeypots attract malware attacks. The intelligence gathered from these interactions is crucial for recognizing malware patterns and developing effective malware detection tools.
- Database Honeypot: With databases frequently targeted by cybercriminals, deploying a database honeypot allows observers to study various attack methodologies, including SQL injection, privilege escalation, and exploitation of SQL services.
- Spider Honeypot: This variety of honeypot constructs deceptive web pages and links that are navigable only by web crawlers and not humans. When a crawler engages with the honeypot, its activities, including its headers, are logged for further analysis. This data is invaluable for identifying and blocking malicious bots and advertising network crawlers.
- Honeypots are decoy systems designed to attract and study malicious behavior.
- Interaction levels vary from low (simple emulation) to high (full OS access).
- Purpose can be research (study attacker tactics) or production (detect real threats).
- Detection is possible — attackers may recognize honeypots via inconsistencies or tools like Netlas and Shodan.
- Proper isolation is critical to avoid introducing new risks into your network.
20+ Best Open Source Honeypots for Modern Cyber Defense
Choosing the right honeypot can be challenging with so many options available. Below is a curated collection of free and open source tools — spanning a wide range of services, protocols, and interaction levels to suit various cybersecurity needs.
Multi-Protocol Honeypots
Multi-protocol honeypots are designed to emulate multiple network services simultaneously. This allows them to detect a broader range of malicious activity — from brute-force login attempts to service enumeration and lateral movement scans — all from a single deployment.
OpenCanary
https://github.com/thinkst/opencanary
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Python | BSD‑3‑Clause | May 2025 |
OpenCanary emulates multiple common services — including SSH, HTTP, FTP, MySQL, and SMB — and provides flexible alerting via syslog, email, and integration with SIEM tools. Lightweight and easy to configure, it is widely used for network-wide threat detection.
Glutton
https://github.com/mushorg/glutton
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Go | GPL‑3.0 | May 2025 |
Glutton accepts and logs any TCP connection through modular handlers. It captures metadata from incoming probes and supports protocol fingerprinting — ideal for detecting scanning, reconnaissance, and unknown service enumeration.
Chameleon
https://github.com/qeeqbox/chameleon
| Interaction Type | Language | License | Stars | Last Activity |
|---|---|---|---|---|
| Low | Python / Docker | AGPL‑3.0 | 689 | August 2023 |
Chameleon is a multi-service, low‑interaction honeypot framework written in Python (with Docker support), offering emulators for over a dozen protocols. Modular deployment through Docker or scripts. Visual live monitoring via Grafana dashboards. Structured logging (PostgreSQL, syslog) of credentials, traffic, and protocol interactions.
Although the last significant code update was in January 2022, it remains a popular and versatile option for multi-protocol honeynet setups, offering broad coverage in a single-pane solution.
Dionaea
https://github.com/DinoTools/dionaea
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | C / Python | GPL‑2.0 | February 2021 |
Dionaea is a low-interaction honeypot supporting multiple protocols — including SMB, FTP, HTTP, and MySQL. It emulates vulnerable services to capture malware and shellcode, using the Libemu library. Integrated with hpfeeds and SQLite logging, it is still used for malware collection and early-stage network reconnaissance detection.
honeypots
https://pypi.org/project/honeypots
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Python | AGPL‑3.0 | September 2024 |
The honeypots package provides a configurable collection of network service traps, including modules for HTTP, SSH, FTP, DNS, and more. It logs attacker interactions and integrates with common data sinks such as syslog, PostgreSQL, and Elasticsearch, making it a flexible option for both research and production honeynets.
HTTP Honeypots
HTTP honeypots simulate vulnerable web servers to attract and analyze attacks like scanning, exploitation, and web-based malware delivery — making them key tools in honeypot cyber security.
HoneyHTTPD
https://github.com/bocajspear1/honeyhttpd
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Python | MPL‑2.0 | May 2025 |
HoneyHTTPD is a lightweight Python framework for creating customizable fake web servers. You can script precise HTTP/HTTPS responses and log each request, with options to export data to files, Elasticsearch, or AWS S3.
HASH
https://github.com/DataDog/HASH
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Node.js | Apache‑2.0 | May 2024 |
HASH is a YAML-driven honeypot framework that serves randomized HTTP/HTTPS responses to emulate a wide range of web services. It’s highly effective at deceiving bots and integrates easily with monitoring pipelines.
Express‑honeypot
https://github.com/christophe77/express-honeypot
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low to Medium | Node.js | MIT | February 2025 |
Express‑honeypot uses Express middleware to detect LFI and RFI attacks. It dynamically serves hundreds of fake URLs and logs malicious access attempts, including any downloaded payloads.
Simple HTTP Honeypot Server
https://github.com/0xNslabs/http-honeypot
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Python | MIT | July 2023 |
This Twisted-based honeypot clones a target site and logs all HTTP interactions (headers, IP, request paths). It inlines resources for realism, making it suitable for educational or light deployment scenarios.
Blackhole for Bad Bots
https://wordpress.org/plugins/blackhole-bad-bots/
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | PHP | GPL‑2.0 | March 2025 |
Blackhole for Bad Bots is a WordPress plugin that embeds a hidden trap link into site footers — invisible to human visitors but detectable by bots that ignore robots.txt. When triggered, the plugin blocks those bots from accessing the site. It’s lightweight, effective, and actively maintained, with over 30,000 installs.
SSH Honeypots
SSH honeypots emulate terminal‑based remote access to capture brute-force attempts, command execution, and attacker behavior.
Cowrie
https://github.com/cowrie/cowrie
| Interaction Type | Language | License | Last Release |
|---|---|---|---|
| Medium to High | Python | ISC‑0.0 | Nov 2024 |
Cowrie simulates a Debian‑style shell with a configurable fake filesystem and supports SSH, Telnet, and file transfers. It securely logs sessions, SFTP/SCP activity, and enables optional proxying to live backend systems.
sshesame
https://github.com/jaksi/sshesame
| Interaction Type | Language | License | Last Release |
|---|---|---|---|
| Low to Medium | Go | Apache‑2.0 | Aug 2024 |
sshesame is a lightweight SSH honeypot written in Go. It accepts any credentials and logs connection attempts, channel requests, and session activity without executing commands. It supports YAML configuration, structured (JSON) logging, and has prebuilt binaries and Docker deployment options.
Database Honeypots
Database honeypots simulate vulnerable database services like MySQL, MongoDB, or Elasticsearch to attract, monitor, and analyze attacks targeting critical data systems.
mysql‑honeypotd
https://github.com/sjinks/mysql-honeypotd
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | C | MIT | May 2025 |
mysql‑honeypotd is a lightweight C-based MySQL server honeypot that logs login attempts, authentication failures, and basic client metadata. With active development and real-world use, it’s ideal for monitoring brute-force and reconnaissance activity.
Simple PostgreSQL Honeypot Server
https://github.com/0xNslabs/postgresql-honeypot
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Python | MIT | May 2025 |
This compact Python/Twisted script mimics a PostgreSQL server and logs all connection attempts, including usernames, database names, and client metadata. It serves well for identifying brute‑force and reconnaissance probing against Postgres instances.
Beehive Redis (redis-honeypot)
https://github.com/0n1shi/redis-honeypot
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Go | MIT | November 2022 |
Beehive Redis simulates a Redis server, supporting basic commands like PING, GET, and KEYS. It logs all client interactions to help detect scanning, brute‑force attempts, or unauthorized data access.
Email Honeypots
Email honeypots emulate SMTP servers to trap spam, phishing, and malicious bots — helping to strengthen email security defenses.
Mailoney
https://github.com/phin3has/mailoney
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Python | MIT | May 2025 |
Mailoney is a modern, actively maintained SMTP honeypot written in Python. It logs connection attempts, credentials, and full message content. It supports various operating modes (including open relay and credential capture), stores data in a database, and offers Docker-friendly deployment options.
SMTPLLMPot
https://github.com/referefref/SMTPLLMPot
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low | Python & Shell | GPL‑3.0 | May 2025 |
SMTPLLMPot is a novel proof-of-concept SMTP honeypot that integrates GPT‑3.5 to respond interactively to SMTP clients. It logs all incoming messages and leverages AI to emulate realistic SMTP server behavior, making it effective against modern malicious bots.
IoT Honeypots
IoT honeypots emulate vulnerable or exposed device services — like Telnet, MQTT, Modbus, and CoAP — to attract, log, and analyze attacks against smart devices and embedded systems. These honeypots are vital for tracking IoT-targeted malware, botnet propagation, and unauthorized access attempts.
RIoTPot
https://github.com/honeynet/riotpot
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low‑Hybrid | Go | MIT | January 2024 |
RIoTPot is a Go-based, plugin‑driven honeypot for IoT protocols such as Telnet, SSH, HTTP, MQTT, Modbus, and CoAP. It acts as a proxy, capturing inbound requests and optionally forwarding them to real backend services for deeper deception. It includes a web dashboard, supports custom routes, and is actively developed under the Honeynet Project — making it one of the most complete IoT honeypots currently available.
IoT Honeypot Framework
https://github.com/m1k1o/iot-honeypot-framework
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low‑Hybrid | Go / TypeScript / Python | Apache‑2.0 | April 2022 |
The IoT Honeypot Framework provides a scalable infrastructure for deploying honeypots for MQTT, CoAP, HTTP, Modbus, and Telnet using Docker Swarm. It integrates seamlessly with Elasticsearch for logging and analysis, and comes prepackaged with services and dashboards. Ideal for large-scale IoT security research or operational threat intelligence environments.
Miniprint
https://github.com/sa7mon/miniprint
| Interaction Type | Language | License | Last Activity |
|---|---|---|---|
| Low-Medium | Python | GPL‑3.0 | July 2023 |
Miniprint is a medium-interaction printer honeypot that emulates a networked printer exposed to the public internet. It supports Printer Job Language (PJL) over raw TCP, offers a fully virtualized file system for attackers to interact with, and logs all PostScript and plaintext print jobs to a dedicated uploads directory. Designed for deep inspection, it captures extensive interaction data without writing to the host system.
Honeynet Management Platforms
Managing multiple honeypots across a network can be complex without centralized control. Below are two modern platforms intended to solve this task.
T-Pot is a full-featured honeypot platform maintained by Deutsche Telekom Security. It integrates more than 20 honeypot daemons — including Cowrie, Dionaea, and Mailoney — into a containerized system with automated dashboards powered by the ELK stack (Elasticsearch, Logstash, Kibana). T-Pot runs entirely on Docker, offering modular deployment and real-time threat visualization, making it ideal for SOCs, researchers, and defenders looking for a polished, scalable solution.
CommunityHoneyNetwork (CHN) is a modern management platform built with microservices, Docker, RabbitMQ, and Elasticsearch. It retains support for core honeypots like Cowrie and Dionaea while providing distributed logging and a centralized interface for managing sensors. Though less actively maintained than T-Pot, CHN remains a viable option for academic use and labs experimenting with honeynet architecture.
Choosing the Best Honeypot for Cybersecurity Defense
Are you prepared to fortify your network against emerging threats? Start by assessing your attack surface to understand what potentially exploitable information might be visible to attackers.
Whether you’re monitoring web applications, SSH services, industrial protocols, or IoT devices, there’s a honeypot tailored to your use case:
- Low-interaction honeypots are easy to deploy and effective at detecting automated threats.
- Medium- and high-interaction systems, though more complex, offer deep insight into attacker behavior and techniques.
- For advanced setups, multi-protocol honeypots and centralized management platforms like T-Pot or CHN can help scale your honeynet and reduce operational overhead.

I can show you how deep the Internet really goes
Discover exposed assets, infrastructure links, and threat surfaces across the global Internet.
Related Posts

December 18, 2024
Netlas vs Fofa: Platforms Comparison

November 21, 2024
Netlas vs Shodan: Platforms Comparison

July 13, 2024
Best Attack Surface Visualization Tools

January 20, 2025
Using Maltego with Netlas Module

December 27, 2024
Using theHarvester with Netlas

December 23, 2024
Using TLDFinder with Netlas

















