Modern Cybercrime: Who’s Behind It and Who’s Stopping It
June 25, 2025
20 min read
Did you know that the famous founders of Apple, Steve Jobs and Steve Wozniak, were also among the earliest hackers?
Long before the first Apple computer was built, they were fascinated by the inner workings of telephone systems. In the early 1970s, Wozniak learned about a blue box — a device that could mimic the tones used by phone company switches to route calls. Playing the proper sound sequence could trick the system into giving you free long-distance calls, bypassing the billing entirely.
They built their own blue boxes and even sold a few devices to UC Berkeley students. The experience gave them the thrill of system control and showed them the power of combining curiosity with technology.
If it hadn’t been for the Blue Boxes, there would have been no Apple. I’m 100% sure of that.
– Steve Wozniak
The funny thing is that this blue-box story was also one of the first known acts of cybercrime. It didn’t involve computers yet, but it marked the beginning of a new era in which clever minds could bend digital systems to their will, sometimes legally, sometimes not.
What Is Cybercrime?
According to an overview of how INTERPOL defines and responds to cybercrime:
Cybercrime includes offenses against computer data and systems, as well as the use of such systems to commit other criminal acts.
Similarly, the Council of Europe’s Budapest Convention on Cybercrime defines it as:
A set of criminal offenses against the confidentiality, integrity, and availability of computer data and systems, along with content-related and copyright crimes.
While the core concept of cybercrime is widely understood, legal definitions vary across jurisdictions. Some countries emphasize offenses against information systems, while others focus on the means or intent behind the crime.
- Cybercrime
- any illegal activity involving a computer, networked device, or digital system — either as the tool, target, or environment of the crime. It includes a wide range of offenses, such as unauthorized access, data theft, online fraud, malware distribution, extortion (e.g., ransomware), and attacks on critical infrastructure.
In the early days of hacking, one common motivation was simply destruction for its own sake — a digital form of vandalism. Notable examples include the Michelangelo virus1 in the 1990s, which overwrote data on infected machines, and the CIH (Chernobyl) virus2, infamous for corrupting BIOS chips and rendering computers unusable. But while such acts once made headlines, purely destructive attacks with no purpose beyond chaos have become rare.
Today’s destructive incidents — like NotPetya3 or Shamoon4 — still cause massive damage, but they are typically driven by financial, political, or strategic objectives, not just mischief.
What Motivates Modern Cybercriminals:
- Financial Gain
The most widespread motivations include ransomware attacks, banking trojans, credit card theft, cryptojacking, phishing, and large-scale fraud schemes. Both individual attackers and organized crime groups operate in this space. - Hacktivism (Ideological or Political Causes)
Hacktivists attack systems to protest, expose, or disrupt. Examples include defacing government websites, leaking classified data, or launching DDoS attacks against corporations or political opponents. - Espionage
State-sponsored actors or competitors may seek confidential data, such as intellectual property, diplomatic cables, military documents, or proprietary business information, to gain a long-term strategic advantage. - Sabotage and Destruction
Attacks intended to disrupt or destroy critical systems are often linked to cyberwarfare or cyberterrorism. They aim to cripple infrastructure, power grids, or public services. - Personal Revenge or Harassment
Often seen in insider threats or doxing. These crimes are emotionally driven and typically target specific individuals or organizations. - Curiosity or Challenge (Thrill-Seeking)
Some attackers are motivated by curiosity, recognition, or the technical challenge, especially among younger or first-time offenders. While not always malicious, the impact can still be severe. - Coercion and Extortion
In cases like sextortion or data leaks, attackers use fear and pressure to manipulate victims into compliance, often overlapping with financial or personal motives.
The motives behind cybercrime have matured, even if the tools remain just as dangerous.
Types of Cybercrimes
Cybercrime is a global issue, but its legal definitions vary across countries and jurisdictions. While specific enforcement and terminology may vary by jurisdiction, there is a near-universal baseline for criminal liability in cyberspace. Let’s mark this baseline.
Cybercrime Taxonomies
Several classification systems have emerged to aid investigation, prosecution, and international cooperation. The most prominent is defined in the Convention on Cybercrime, adopted in 2001 by the Council of Europe. It offers a structured taxonomy adopted or inspired by legislative frameworks in many countries, including EU member states, the United States, Japan, Australia, and others.
According to the Convention, cybercrime offenses fall into four primary categories:
Offenses against the confidentiality, integrity, and availability (CIA) of computer data and systems These crimes are enabled explicitly by technology and include illegal access, illegal interception, data interference, and system interference.
Computer-related offenses These are traditional crimes (e.g., fraud and forgery) committed digitally. The computer or network serves as a tool for executing otherwise conventional criminal conduct.
Content-related offenses These include the distribution of child sexual abuse material (CSAM) and other forms of prohibited content, such as incitement to violence or extremist propaganda.
Offenses related to infringements of copyright and related rights This category addresses unauthorized reproduction, distribution, and access to protected digital works.
Some interpretations5 extend this taxonomy further by introducing tiers of cybercrime:
- Tier 1 – Crimes enabled by computers (e.g., online fraud, identity theft)
- Tier 2 – Crimes targeting computer systems (e.g., malware deployment, hacking)
- Tier 3 – Crimes involving content (e.g., CSAM, hate speech)
- Tier 4 – Cyber-dependent crimes with national security implications (e.g., APT operations, infrastructure sabotage)
Of course, there are many other models exists, but they are not as widely used and less prominent in the context of worldwide legislation.
Globally Recognized Cybercrime Offenses
The Budapest model provides a widely accepted baseline for drafting laws, structuring enforcement priorities, and framing international cooperation. The offenses described in the following section align with this structure and are recognized, in some form, across most national jurisdictions.
- Illegal Access to Computer Systems
Accessing the whole or any part of a computer system without right, whether by bypassing security or otherwise, constitutes an offense when done intentionally. This includes unauthorized intrusion into systems, regardless of the attacker’s purpose, and may cover systems connected to other networks.
- Illegal Interception of Communications
Intentionally intercepting non-public computer data transmissions without right — whether during transmission to, from, or within a computer system — is a criminal offense. This includes interception through technical means such as packet sniffing or electromagnetic capture.
- Data Interference
Damaging, deleting, deteriorating, altering, or suppressing computer data without the right is an offense when committed intentionally. This protects the integrity and availability of data within computer systems from unauthorized tampering or sabotage.
- System Interference
Intentionally hindering the lawful functioning of a computer system without permission — by inputting, transmitting, deleting, or damaging data — is a punishable offense. This includes denial-of-service attacks and other acts intended to disrupt operations.
- Misuse of Devices
Producing, distributing, or possessing devices, including software or passwords, primarily intended to commit offenses such as illegal access, interception, or interference, constitutes a criminal act. The offense requires intent to use or enable the use of such tools unlawfully.
- Computer-Related Forgery
Inputting, altering, deleting, or suppressing computer data to create inauthentic data that appears legally valid is considered computer-related forgery. The offense applies regardless of whether the falsified data is directly readable.
- Computer-Related Fraud
Causing a loss of property to another by interfering with computer data or systems — through acts such as manipulation or suppression — to gain an unlawful economic benefit is considered fraud when committed intentionally and without right.
- Offenses Related to Child Sexual Abuse Material (CSAM)
Producing, distributing, transmitting, offering, procuring, or possessing child sexual abuse material in digital form is criminalized. The offense includes content that visually depicts minors or persons appearing to be minors engaged in sexually explicit conduct, or realistic representations thereof.
- Offenses Related to Copyright and Related Rights
Infringing copyright or related rights on a commercial scale and through computer systems is a criminal offense. This includes the unauthorized distribution or reproduction of protected works or performances through digital networks.
To create a complete picture, in 2003, the Budapest Convention was expanded with the First Additional Protocol (2003), requiring the criminalization of acts involving the dissemination of racist and xenophobic material through computer systems. The protocol is not as widely adopted as the original Convention, mainly because of differing national views on regulating speech online.
Nowadays Cybercrime Trends
Deepfakes and Synthetic Media in Cybercrime
Initially viewed as a novelty or entertainment tool, deepfakes are now increasingly weaponized in social engineering campaigns. Fraudsters can impersonate executives, public figures, or relatives in voice or video to enhance phishing messages, manipulate conversations, or demand urgent actions. Deepfake-based phishing (also called “vishing 2.0”) has successfully deceived employees into transferring funds or disclosing sensitive credentials, bypassing traditional warning signs.
Many countries are rapidly introducing laws to regulate deepfakes and synthetic media. In the United States, federal laws like the 2025 Take It Down Act and the proposed No Fakes Act criminalize non-consensual and deceptive use of AI-generated content, with over 40 states enacting similar measures. The UK’s Online Safety Act and the EU’s AI Act introduce strict obligations on platforms and classify high-risk synthetic media for tighter scrutiny. Countries like Canada and Australia are advancing broader online harms legislation, while specific laws such as Tennessee’s ELVIS Act protect against unauthorized AI-based impersonation. This growing regulatory patchwork reflects global concern over the misuse of deepfake technologies.
One of the most widely reported and alarming deepfake incidents occurred in March 2024, when a deepfake video of Ukrainian President Volodymyr Zelenskyy appeared on hacked Ukrainian news websites and social media. In the video, Zelenskyy seemingly urged Ukrainian troops to lay down their arms and surrender to Russia. The video was quickly identified as fake due to poor facial synchronization and unusual body language. This event highlighted the potential of deepfakes to be used in information warfare, mainly to spread disinformation and undermine public trust during conflicts.
A deepfake of Ukrainian President Volodymyr Zelensky calling on his soldiers to lay down their weapons was reportedly uploaded to a hacked Ukrainian news website today, per @Shayan86 pic.twitter.com/tXLrYECGY4
— Mikael Thalen (@MikaelThalen) March 16, 2022
Hacktivism in the Context of Geopolitical Conflicts
Cyberactivism — or hacktivism — has become a prominent feature of modern geopolitical conflict. State-aligned or ideologically motivated hacker groups target rival governments, institutions, or companies with defacements, data leaks, and denial-of-service attacks. The Russia–Ukraine war, for example, has seen widespread use of cyber operations by both sides and their supporters, often blurring the lines between state and civilian participation.
Hacktivism is not limited to sabotage. Campaigns often aim to disrupt narratives, leak internal documents, or retaliate against perceived injustices. These attacks may technically fall under cybercrime statutes, but enforcement is difficult when the perpetrators operate across borders and under political protection. Hacktivist groups are sometimes openly celebrated or even coordinated by states, complicating international legal responses.
Election Sabotage and Information Warfare
Modern elections are increasingly vulnerable to cyber-enabled manipulation. Threat actors may deploy coordinated disinformation campaigns, bot networks, or malicious leaks to influence public perception, sow distrust, or promote specific candidates.
One of the most recent cases took place in December 2024. Romania’s Constitutional Court annulled the result of the first round of the presidential election — initially won by far-right candidate Călin Georgescu — citing evidence of foreign interference via digital platforms, including social media manipulation. The court’s ruling mandated a complete election redo in spring 2025, resulting in a new vote held in May, won by pro‑EU candidate Nicușor Dan. This case prompts broader discussion on the influence of AI, social platforms, and cyber operations in democratic processes.
Several countries have introduced laws to counter election-specific AI manipulation, automated disinformation, deepfakes, and bot-based manipulation. In the U.S., over two dozen states have passed or proposed laws restricting deceptive synthetic media in political campaigns. The U.K.’s Online Safety Act 2023 holds platforms accountable for disinformation but lacks AI-specific election rules.
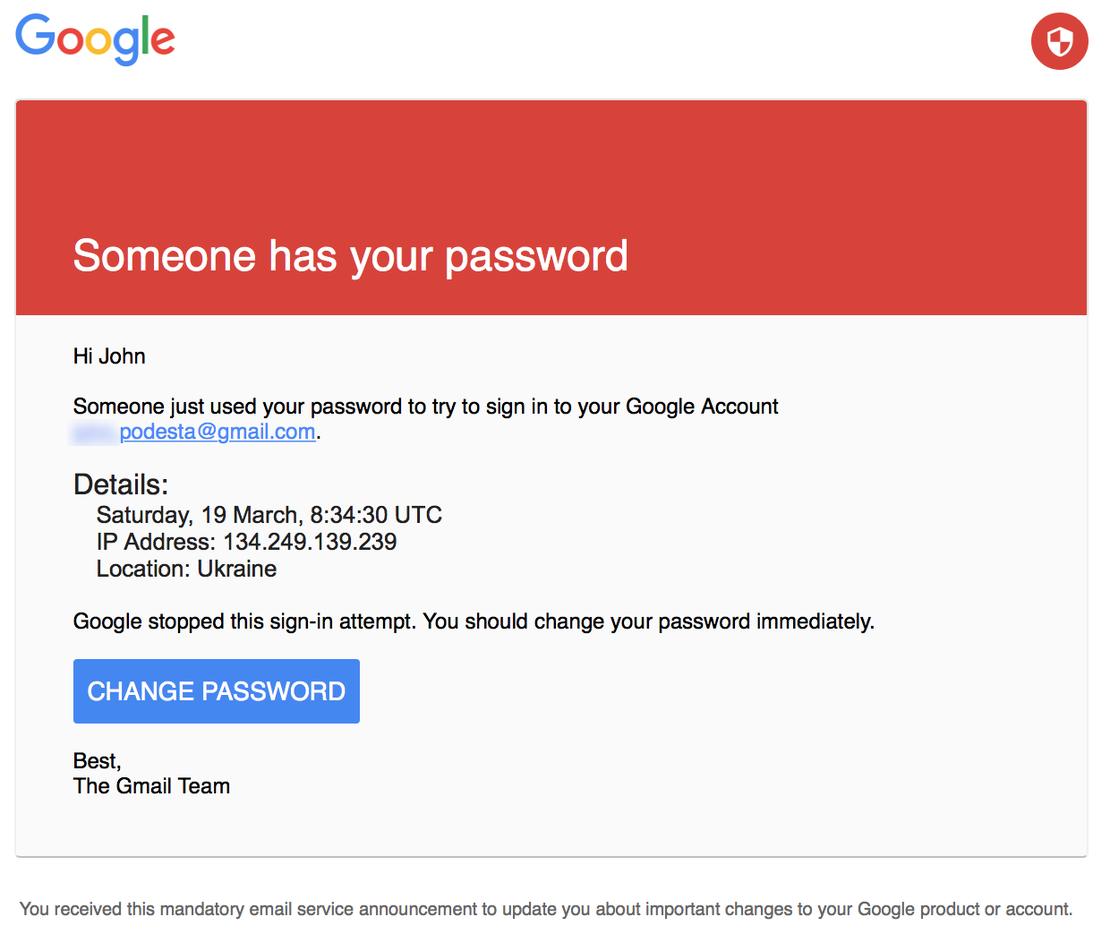
In March 2016, a coordinated phishing campaign targeted the Hillary Clinton presidential campaign and the Democratic National Committee (DNC). Attackers used spoofed emails—designed to look like Google security alerts—to trick recipients into revealing login credentials. One high-profile victim was campaign chair John Podesta. After gaining access, attackers exfiltrated thousands of internal emails and documents.
These materials were later published via platforms like DCLeaks, Guccifer 2.0, and WikiLeaks, with timed releases around key moments in the election cycle. The leaks generated widespread media coverage, disrupted the Democratic National Convention, and negatively impacted Clinton’s public image. U.S. investigations concluded the campaign was part of a broader effort to influence the 2016 U.S. election, marking one of the most prominent examples of cyber-enabled election sabotage.
Anti-Anonymity Laws and Digital Identification Mandates
Governments concerned about national security, social control, or cybercrime often introduce regulations to reduce anonymity online. These may include mandatory SIM registration, VPN usage tracking, and identity verification for social media accounts or domain ownership. While justified as tools for crime prevention, such laws often have broader implications for civil liberties and freedom of expression. In countries like China, Iran, and Russia, control over encryption, VPNs, and anonymous communication has been tightened.
Forcing International Tech Companies to Comply with Local Laws
Many states are enacting legislation that requires foreign technology firms to store data locally, establish legal representation within the country, and comply with content takedown orders. These “digital sovereignty” laws are framed to protect national interests and user privacy. Still, they often serve to assert control over platforms that facilitate free expression or host dissenting content. Major platforms like Google, Meta, and Apple have faced mounting pressure to follow these rules or risk fines, service restrictions, or outright bans.
Global Cybercrime Impacts
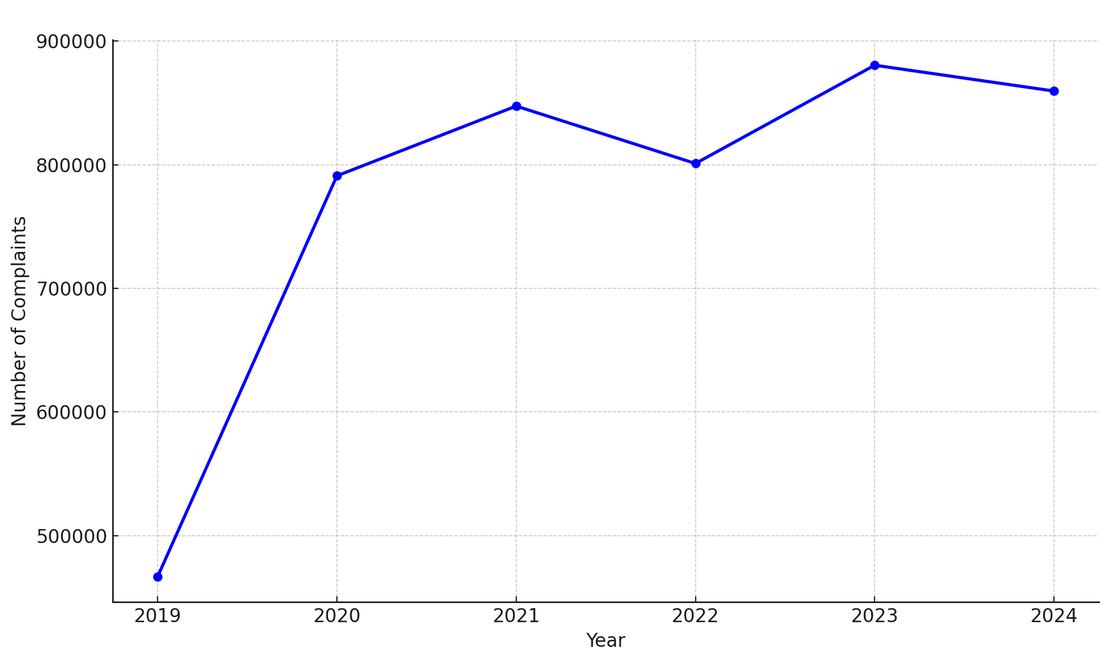
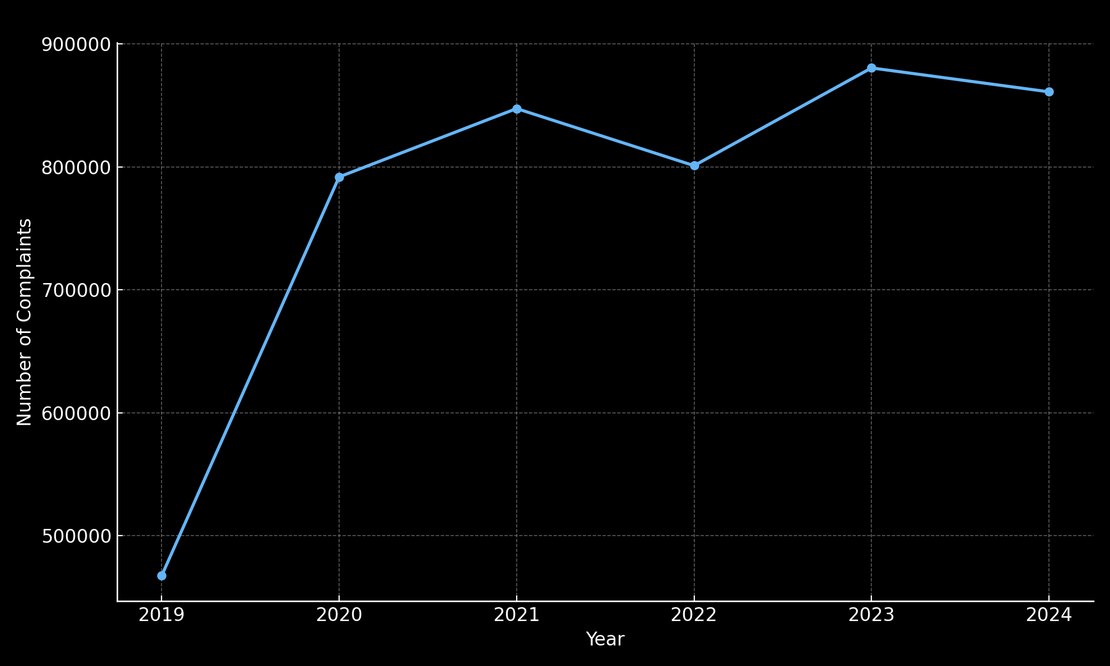
Cybercrime has surged globally from 2019 through 2024, with a sharp spike observed during the COVID-19 pandemic. As businesses and individuals moved online in 2020, threat actors pounced — one analysis noted that malware and ransomware attacks soared by over 350% and 430%, respectively. Law enforcement data echo this rise.
For example, the FBI’s Internet Crime Complaint Center (IC3) saw6 reported cybercrime complaints jump from about 467,000 in 2019 to 791,000 in 2020, an unprecedented year-over-year leap.
Escalating Financial Costs
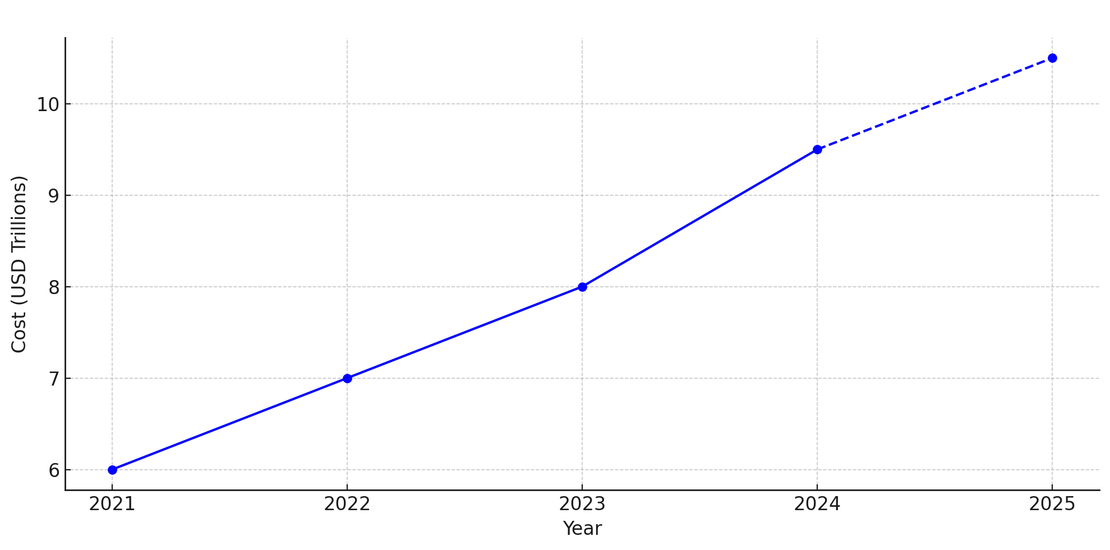
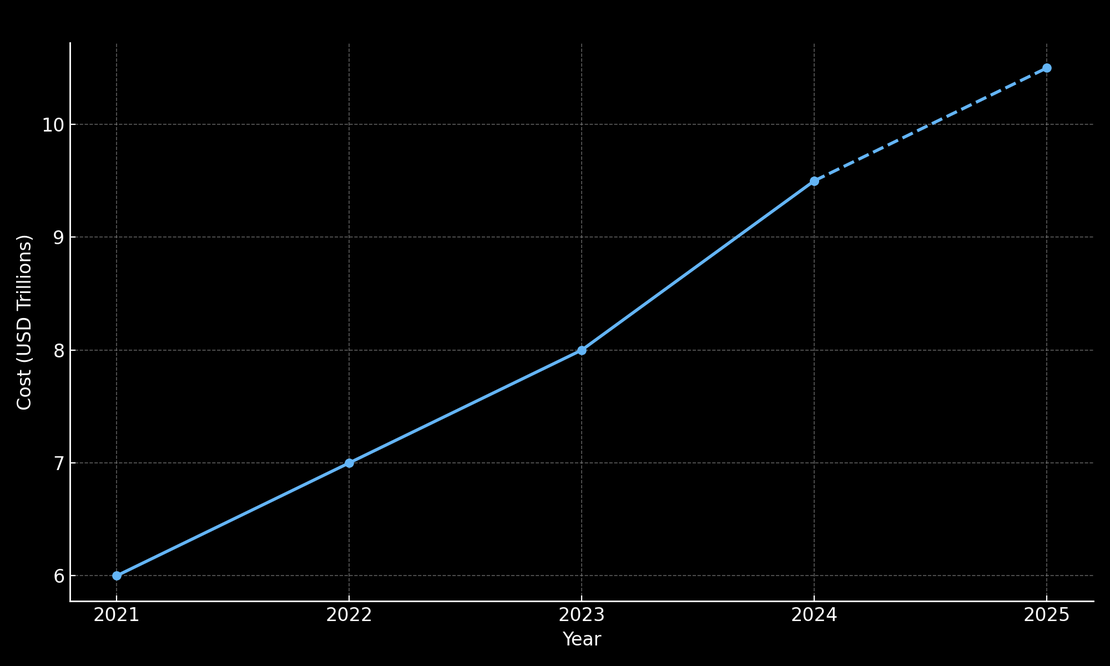
The financial impact of cybercrime has exploded alongside the rise in incidents. INTERPOL notes7 that the annual losses from cybercrime are now comparable to the GDP of major economies. Industry analyses estimate global cybercrime costs at around $6 trillion in 2021, roughly double the figure from just a few years prior, and project costs to reach $10.5 trillion annually by 2025.
| Category | 2022 | 2023 |
|---|---|---|
| Reported ransomware attacks | 1,300+ | 2,200+ |
| Value of global cyber fraud loss | $2.7 billion | $3.5 billion+ |
| National cybercrime operations | 40+ countries | 60+ countries |
| Arrests during cyber operations | ~1,200 suspects | 1,500+ suspects |
| Seized infrastructure/services | N/A | 70 servers, 1,300+ domains |
According to Cybersecurity Ventures’ annual reports and partner publications8, the global economic impact of cybercrime inflicted $6 trillion in damages in 2021, with costs rising to $9.5 trillion by 2024. The projection for 2025 reaches $10.5 trillion, reflecting a compound annual growth rate of approximately 15% from a 2020 baseline.
Dominant Cybercrime Types
The European Union Agency for Cybersecurity (ENISA) regularly monitors cyber threats targeting critical infrastructure sectors. According to their 2024 Threat Landscape report9, DoS, DDoS, and RDoS attacks accounted for the largest share of cyber incidents, making up 41.1% of all reported cases. Ransomware remained the second most common threat, responsible for 25.79% of incidents — a trend driven by increasingly aggressive tactics like double extortion. Data breaches, including leaks of sensitive or personal information, comprised 19.01%. Meanwhile, phishing and social engineering attacks comprised 6.06%, and malware-based compromises accounted for 5.19%.
pie
title Incidents by Threat Type
"DoS/DDoS/RDoS Attacks" : 41.1
"Ransomware" : 25.79
"Data Breaches" : 19.01
"Phishing / Social Engineering" : 6.06
"Malware" : 5.19
"Other" : 2.85
These numbers reflect only incidents reported to national or EU-level cybersecurity bodies, where the effect was considered disruptive or economically significant.
Primary Targets
Everyone from private citizens to multinational organizations and governments has been victimized. From personal bank accounts emptied by scams to national hospitals paralyzed by ransomware, no one is spared.
1. Individuals
Every year, hundreds of millions of individuals fall victim to cybercrime. In the United States alone, the FBI received over 880,000 individual cybercrime reports in 20236. The actual global number is far higher.
Victims often suffer:
- Identity theft, bank fraud, or account takeovers
- Ransomware or wiper malware on personal devices
- Phishing, vishing, and smishing scams
- Online harassment and blackmail, including with stolen data or private images
2. Businesses
Businesses are prime targets for ransomware groups, email fraud, and supply chain attacks. In 2023, IBM X-Force ranked10 manufacturing, finance, professional services, and healthcare among the most attacked sectors worldwide. Meanwhile, Mandiant found11 that 17.4% of all incidents globally in 2024 affected financial services, the top targeted industry.
Notable consequences include:
- CNA Financial (2021): Paid $40 million in ransom after a large-scale data breach.
- HSE Ireland – Data Fallout (2023): Though the original attack occurred in 2021, by 2023 over 32,000 individuals were notified of leaked personal data. Critical treatments were paused, and trust in digital health systems collapsed. The total recovery cost exceeded €53M.
- McLaren Health Care (2023): A ransomware attack that disrupted health care operations and led to a lawsuit over the exposure of approximately 2.1 million patient records.
3. Critical Infrastructure
Critical infrastructure has become a frontline in the cyberwarfare era, with hospitals shut down, trains halted, and power grids manipulated. Attackers target essential systems for extortion, disruption, or geopolitical influence.
- Colonial Pipeline (2021): Fuel supplies were disrupted across the U.S. East Coast after a ransomware attack forced operations to halt.
- Ardent Health Ransomware Attack (2023): A ransomware attack forced Ardent Health Services to shut down IT systems across 30 hospitals in six U.S. states. Emergency rooms diverted patients, surgeries were delayed, and manual processes were reintroduced.
- Kyivstar Telecom Disruption (2023): Ukraine’s largest telecom operator, Kyivstar, was knocked offline in December 2023. Mobile service, internet, and emergency air-raid alerts were disrupted. The attack, attributed to Sandworm, led to a $90M infrastructure recovery program.
ICS/SCADA systems, medical devices, and legacy networks remain uniquely vulnerable and expensive to secure.
4. Governments
Government agencies, election systems, military infrastructure, and diplomatic networks are frequent targets of nation-state actors and APT groups. In recent years:
- SolarWinds Supply-Chain Attack (2020–2024): Although first uncovered in 2020, a resurgence of exploitation was reported in 2023, when Russian-linked APTs regained access to the platform. Multiple U.S. federal agencies — including Treasury and Homeland Security — confirmed ongoing infiltration, highlighting the enduring global impact of supply-chain compromise.
- Attack on Northwestern Polytechnical University (2022): The China National Computer Virus Emergency Response Center (CVERC) and Qihoo 360 attributed cyberattacks on Northwestern Polytechnical University to the NSA’s TAO unit, labeled APT-C-40, possibly linked to the Equation Group. They allege a U.S. espionage campaign stole over 140GB of sensitive aerospace and defense research data from the university.
- EU Parliament Cyberattack (November 2023): In November 2023, the European Parliament experienced a coordinated DDoS and website defacement attack, disrupting parliamentary sessions and public access to EU information portals. While no APT has claimed responsibility, EU digital resilience strategies were immediately accelerated to counter similar future threats.
According to a 2023 INTERPOL report7, state-sponsored cyber operations were responsible for at least 25% of all high-complexity global incidents. Meanwhile, bot-driven misinformation and election interference tactics are now considered standard practice during major democratic events.
An Advanced Persistent Threat (APT) group is a highly skilled, well-resourced cyber adversary — often linked to a nation-state or organized cybercrime syndicate — that conducts long-term, targeted attacks to gain unauthorized access to systems, exfiltrate data, or disrupt operations. Unlike opportunistic attackers, APT groups use custom tooling, stealthy techniques, and multi-stage campaigns to infiltrate networks and maintain persistence over time. Strategic objectives, such as espionage, sabotage, or geopolitical influence, drive their operations.
Notable examples include APT29 (Cozy Bear), linked to Russian intelligence, APT41, associated with Chinese state-sponsored espionage and financially motivated activity, and Equation Group, widely believed to be related to the NSA, and offensive toolkits revealed in the Vault 7 CIA leaks.
Year-over-Year Trends
Each year from 2019 through 2024 has seen greater scale and new tactics in cybercrime. Cybercriminal activity exploded significantly with the mass shift to remote work and digital services. On the other hand, defensive improvements and law enforcement pressure may have tempered a few threats: security firms noted a slight decline in observed ransomware cases from 2021 to 2022, and Mandiant reported11 that the median “dwell time” (the time an attacker lurks in a network before detection) dropped from over 20 days in 2020 to around 11 days in 2024, down, with the lowes value of 10 days in 2023.
Despite a few hopeful signs, the overall trend remains upward: more attacks, higher losses, and increasingly crafty adversaries each year. Cybercriminal techniques continue to evolve – from the rise of “as-a-service” criminal tools that make hacking easier, to the exploitation of global events (like the pandemic or geopolitical conflicts) to fuel new attacks.
Meanwhile, the commercialization of cybercrime has lowered barriers for entry: would-be criminals can buy stolen data, malware kits, or even access to hacked networks (backdoors) on illicit marketplaces10. All signs indicate that cybercrime will keep growing in scale and sophistication year over year without a coordinated global response, posing ever-greater economic and security challenges worldwide.
Fighting Cybercrime
It’s clear that today’s threats require coordinated responses across sectors, borders, and disciplines. Organizations aim to cooperate to combat these threats. To understand this cooperation, let’s categorize actors and institutions by their functions and spheres of operation.
This leads us to a two-dimensional framework, defined by three Levels of Cybercrime Response — International Level, National Level, and Corporate Level — and three Functional Areas of Action — Legal and Policy Frameworks, Investigation and Threat Intelligence, and Technical Collaboration and Incident Response.
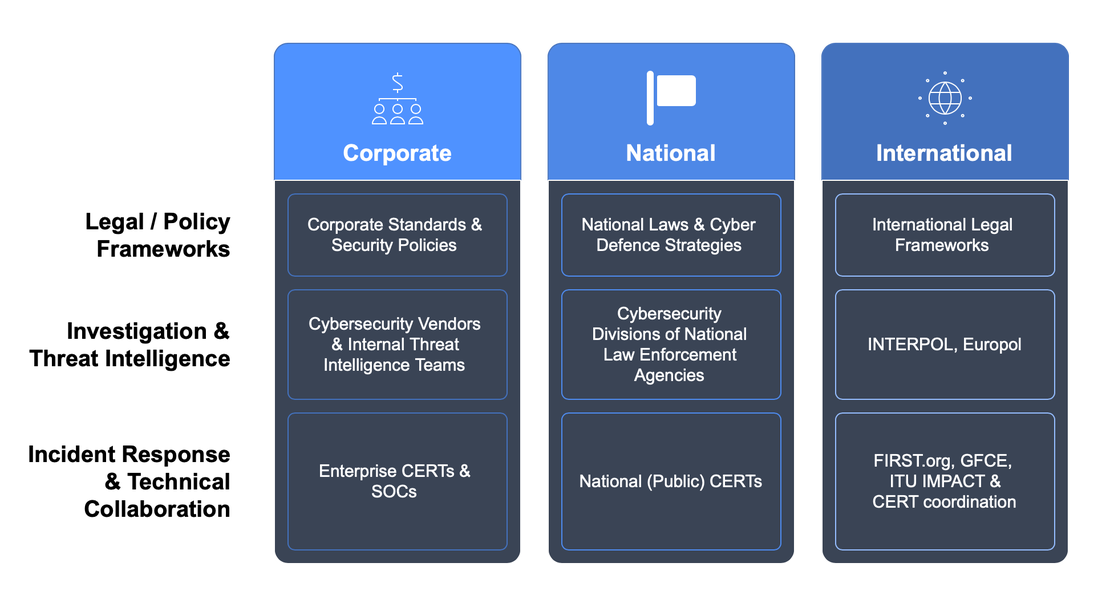
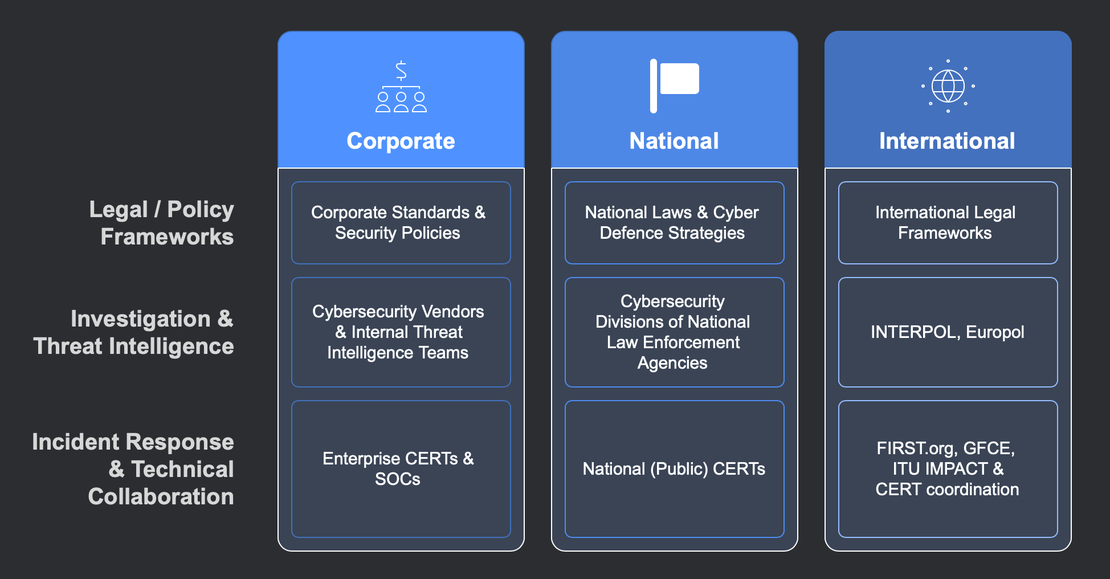
Let’s take a closer look at this structure by exploring how cybercrime is tackled at the corporate, national, and international stages.
International Level
The international level focuses on making cross-border cooperation possible: aligning laws, connecting investigators, and supporting technical response teams. Without this international collaboration layer, many cybercrimes would go unpunished simply because no single nation has full jurisdiction over the attack chain.
Legal and Policy Frameworks
One of the most important steps in international cooperation is aligning the legal definitions and tools used to prosecute cybercrime. The cornerstone of this effort is the Budapest Convention on Cybercrime, adopted by the Council of Europe and open to countries worldwide. It provides a framework for defining cyber offenses and simplifying cross-border access to digital evidence. For countries that have ratified it, the convention serves as a foundation for legislative reform and international legal cooperation.
The United Nations Office on Drugs and Crime (UNODC) also plays a central role through its Cybercrime Programme, which helps member states — especially developing nations — build legislative capacity, train investigators and prosecutors, and establish mechanisms for cross-border cooperation.
Investigation and Intelligence Coordination
INTERPOL and Europol facilitate operational coordination between national law enforcement bodies.
- INTERPOL’s Cybercrime Unit coordinates global operations, provides digital forensic support, and operates intelligence sharing and alerts platforms.
- Europol, through its European Cybercrime Centre (EC3), supports EU member states in handling complex cases such as ransomware groups, child exploitation networks, and dark web marketplaces.
- Hosted within Europol, the Joint Cybercrime Action Taskforce (J-CAT) brings together cyber liaison officers from multiple countries for real-time coordination on active investigations.
These institutions do not prosecute cases, but enable national agencies to work together more effectively.
Technical Collaboration and Incident Response
Beyond legal and investigative cooperation, effective cyber defense relies on technical coordination and trust-based information sharing. Organizations such as:
- FIRST.org — a global forum of trusted Computer Security Incident Response Teams (CSIRTs),
- The Global Forum on Cyber Expertise (GFCE) — focused on capacity building and best practice sharing,
While these organizations don’t chase cybercriminals directly, they enable faster detection, shared knowledge, and coordinated containment.
National Level
Individual nations have the core responsibility for fighting cybercrime. National governments are uniquely positioned to enforce laws, protect critical infrastructure, and provide incident response at scale. They act as the operational backbone of cyber defense, combining legal authority, investigative power, and public-sector cybersecurity expertise.
Legal and Policy Frameworks
At the national level, laws define which cyber activities are criminal, how evidence can be collected, and what penalties apply. These laws sometimes draw from international agreements (such as the Budapest Convention) but are implemented locally through national legislation.
Many countries have also adopted national cybersecurity strategies — high-level documents outlining priorities for protecting infrastructure, managing incidents, developing talent, and engaging international partners. These strategies typically designate roles for different agencies and define the mechanisms for public-private coordination.
Investigation and Threat Intelligence
Investigating cybercrime falls primarily to law enforcement agencies with specialized cyber units. These units handle a wide spectrum of cases: from business email compromise and ransomware to large-scale breaches and online fraud.
Examples include:
- 🇨🇦 RCMP National Cybercrime Coordination Unit (NC3)
- 🇨🇳 Ministry of Public Security (MPS) – Cybersecurity Administration
- 🇩🇪 Bundeskriminalamt (BKA) – Cybercrime Unit
- 🇬🇧 National Crime Agency (NCA) – NCCU
- 🇺🇸 FBI Cyber Division
Alongside law enforcement, intelligence and national security services play a critical role, especially when attacks are suspected to be the work of foreign states or pose a risk to national security. Agencies like the 🇺🇸 NSA, 🇬🇧 GCHQ / NCSC, and 🇩🇪 ZITiS collect and analyze threat intelligence, monitor adversarial cyber activity, and sometimes engage in offensive or defensive cyber operations.
In China, cybercrime prevention is closely integrated with broader state control over the internet. The Ministry of Public Security plays a central role in investigating cybercrime and monitoring online activity, restricting access to certain websites, and enforcing content regulations.
This centralized approach, combined with strict enforcement and infrastructure-level controls — often referred to collectively as the Great Firewall — significantly limits access to harmful content and foreign threat infrastructure. As a result, China’s model prioritizes risk reduction through control, minimizing many external cyber threats, albeit at the cost of internet openness.
Technical Collaboration and Incident Response
Many governments operate or sponsor national-level CERTs to support detection and containment. These teams issue vulnerability alerts, coordinate incident response for public infrastructure, and serve as national points of contact in global CERT networks.
Examples include:
These public CERTs often work hand-in-hand with industry, offering technical guidance during incidents and helping disseminate threat intelligence across sectors.
- CERT stands for Computer Emergency Response Team
- It is a group of cybersecurity professionals responsible for detecting, analyzing, and responding to security incidents.
CERTs can operate at various levels — within private companies, national governments, or international alliances — and often serve as trusted points of contact for sharing threat intelligence, issuing vulnerability alerts, and coordinating incident response efforts across organizations or borders.
Corporate Level
At the corporate level, organizations are not only frequent targets of cybercrime but also essential actors in the global cyber defense ecosystem. Enterprises, service providers, and security vendors often detect threats first, respond in real time, and generate valuable intelligence that feeds into national and international response systems.
Legal and Policy Frameworks
Most large organizations implement internal security policies, governance frameworks, and compliance programs aligned with standards such as ISO 27001, NIST, or GDPR. These frameworks define how the company secures assets, manages risk, and responds to incidents.
Companies must also meet national cybersecurity compliance obligations in heavily regulated industries like finance, healthcare, and critical infrastructure.
Investigation and Threat Intelligence
Corporate cybersecurity teams play a critical role in detecting, analyzing, and responding to cyber threats that target their infrastructure, employees, and customers. While internal teams often focus on protecting the organization itself, a broader ecosystem of security vendors and large service providers contributes to global threat intelligence.
Beyond the corporate perimeter, security vendors and large technology providers such as Mandiant, CrowdStrike, Kaspersky, and others actively track global threat actors, including APTs, criminal networks, and state-sponsored operations. These companies:
- Analyze malware and infrastructure used in attacks
- Publish technical reports and threat actor profiles
- Share indicators of compromise (IOCs)
- Provide real-time intelligence feeds to clients and partners
Some providers also maintain public-facing platforms (e.g., threat blogs, dashboards, feed APIs) and regularly collaborate with law enforcement and governments during takedowns or investigations of high-impact operations.
- IOC stands for Indicator of Compromise
- It refers to a piece of forensic data that suggests a system may have been breached. Common IoCs include malicious IP addresses, domain names, file hashes, URLs, or specific patterns found in log files.
Security teams use IoCs to detect and respond to threats, often integrating them into intrusion detection systems, firewalls, or threat intelligence feeds.
Technical Collaboration and Incident Response
Many medium and large enterprises operate Security Operations Centers (SOCs) and CERTs to monitor systems, respond to threats, and support recovery.
Corporate CERTs also participate in industry-specific information-sharing alliances. These platforms enable companies to share IOCs, response strategies, and situational awareness, increasing collective defense without requiring central control.
- SOC stands for Security Operations Center
- It is a dedicated team or facility within an organization responsible for continuously monitoring, detecting, analyzing, and responding to cybersecurity incidents. A SOC typically operates 24/7 and uses specialized tools to track threats, investigate alerts, and coordinate incident response to protect the organization’s digital assets.
In summary, the corporate level represents the front line of cyber defense, where threats are detected first, damage is felt most directly, and agility is critical. While companies don’t have the authority to prosecute or legislate, they play a vital role in shaping the threat landscape through technology, intelligence, and active participation in broader cybersecurity ecosystems.
Conclusion
Cybercrime is no longer a niche concern — it is a global, persistent, and rapidly evolving threat that affects individuals, organizations, and nations alike. From blue-box phone phreaking in the 1970s to billion-dollar ransomware campaigns and nation-state cyber operations today, the scale and sophistication of malicious activity have grown exponentially.
Cybercrime cannot be eliminated entirely, but its impact can be managed — and in many cases, prevented — through a combination of vigilance, cooperation, and shared intelligence. As the threat landscape evolves, so must the organizations that defend against it. Strengthening connections between these layers is not just a best practice — it’s a necessity.
Book Your Netlas Demo
Chat with our team to explore how the Netlas platform can support your security research and threat analysis.
Michelangelo virus – A DOS-based boot sector virus discovered in 1991, programmed to activate on March 6 (Michelangelo’s birthday) and overwrite parts of the hard drive, potentially destroying user data. ↩︎
CIH (Chernobyl) virus – A highly destructive Windows 9x virus discovered in 1998. It could overwrite the hard drive and corrupt the computer’s BIOS, making the system unbootable without hardware repair. ↩︎
NotPetya – A 2017 wiper malware initially disguised as ransomware. It targeted Ukrainian organizations but quickly spread globally, causing billions in damage. Widely attributed to Russian state-sponsored actors. ↩︎
Shamoon – A disk-wiping malware first seen in 2012 targeting Saudi Aramco and later in other attacks. It overwrites files and the master boot record, rendering infected systems inoperable. Associated with politically motivated cyberattacks. ↩︎
The tiered model of cybercrime is not formally defined in the Budapest Convention but has been proposed in academic and policy literature (McGuire, M. R., 2018, Into the Web of Profit). It helps distinguish between crimes that merely use computers, those that directly target them, and those with broader geopolitical or ideological objectives. ↩︎
INTERPOL Global Crime Trend Report 2022, INTERPOL Global Crime Trend Report 2023. ↩︎ ↩︎
Cybercrime Damages $6 Trillion by 2021, Global Cybercrime Cost $8 Trillion in 2023, Cybercrime to Cost the World $9.5 Trillion in 2024, Cybercrime To Cost The World $10.5 Trillion by 2025, Boardroom Cybersecurity 2022 Report. ↩︎
IBM Security X-Force Threat Intelligence Index 2023, 2024, 2025. ↩︎ ↩︎
Related Posts

June 8, 2025
ASN Lookup Explained: Tools, Methods & Insights

June 11, 2025
FAQ: Understanding Root DNS Servers and the Root Zone

July 20, 2025
An Expert’s View on DNSSEC: Pros, Cons, and When to Implement

June 16, 2025
Google Dorking in Cybersecurity: Techniques for OSINT & Pentesting

July 18, 2025
Hannibal Stealer vs. Browser Security

December 27, 2024
Using theHarvester with Netlas

















