Netlas vs Fofa: Platforms Comparison
December 18, 2024
15 min read
Below is a detailed technical comparison of two popular IoT search engine platforms: Netlas and Fofa. We evaluate their performance across three critical parameters: capabilities, data volume and relevance, and enterprise features. Which platform excels where, and how can you choose the one that best suits your needs?
Capabilities
The first part of our research focuses on a brief overview of the capabilities offered by the two platforms.
It’s important to note that this article will not delve into query syntax or other technical specifics. For such details, we recommend consulting the official documentation for Netlas and Fofa. Instead, we will highlight the key differences between the two tools and discuss scenarios where each is better suited for use.
Search Engine
The core functionality of both platforms is their search engines, which are designed primarily to discover internet-connected devices. In Netlas, this capability is provided through the Responses Search Tool, whereas Fofa’s equivalent tool does not have a specific name. The images below illustrate the interfaces of both tools.
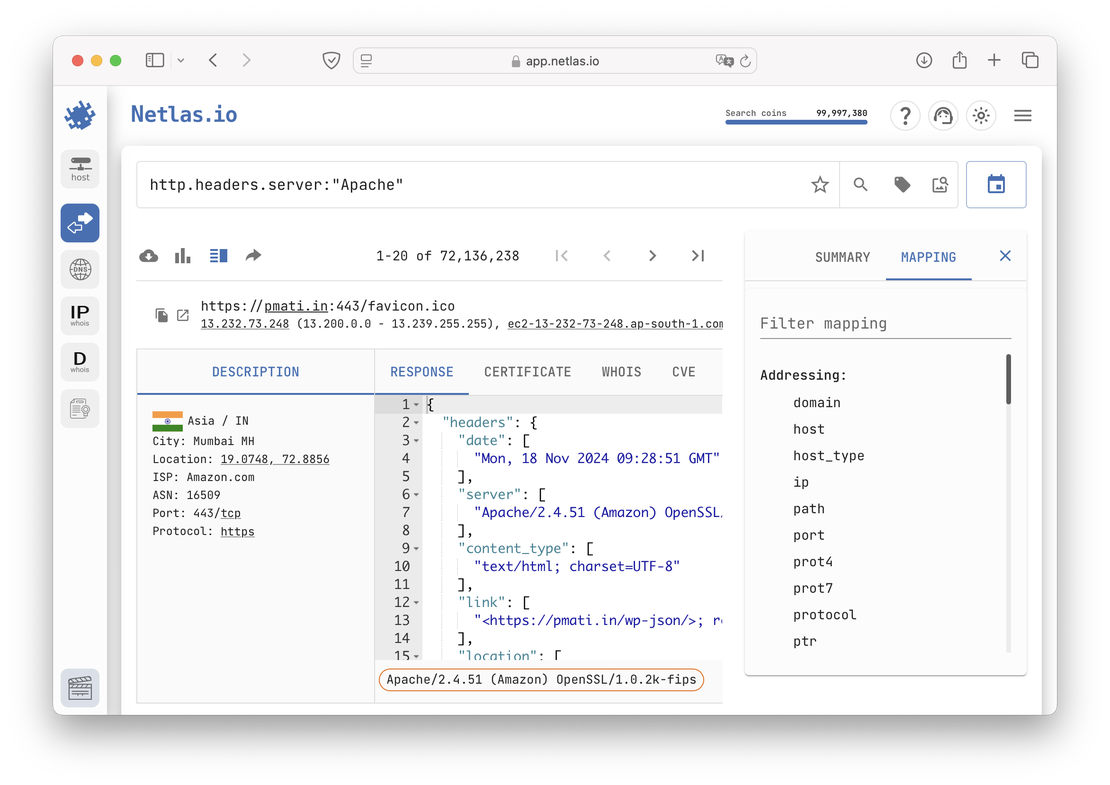
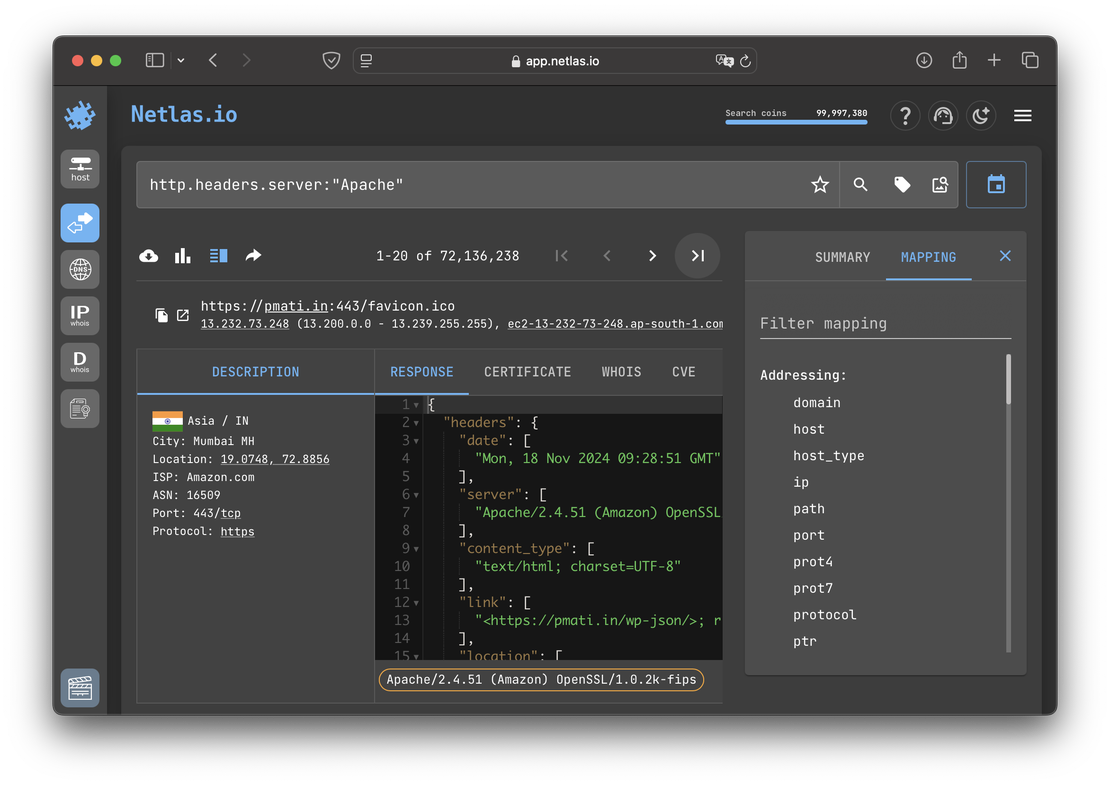
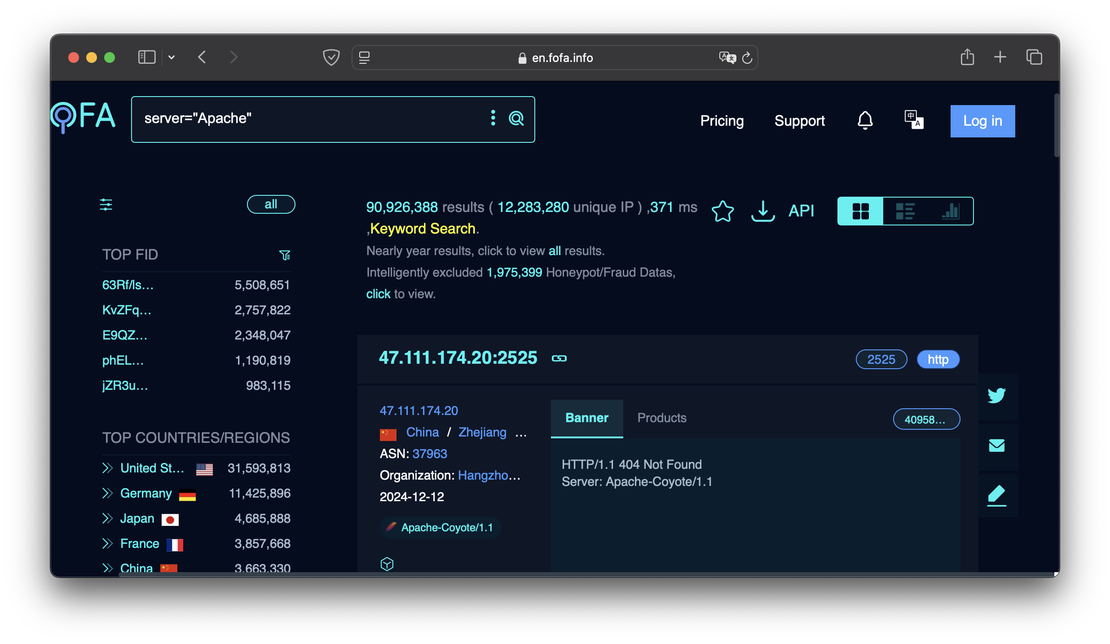
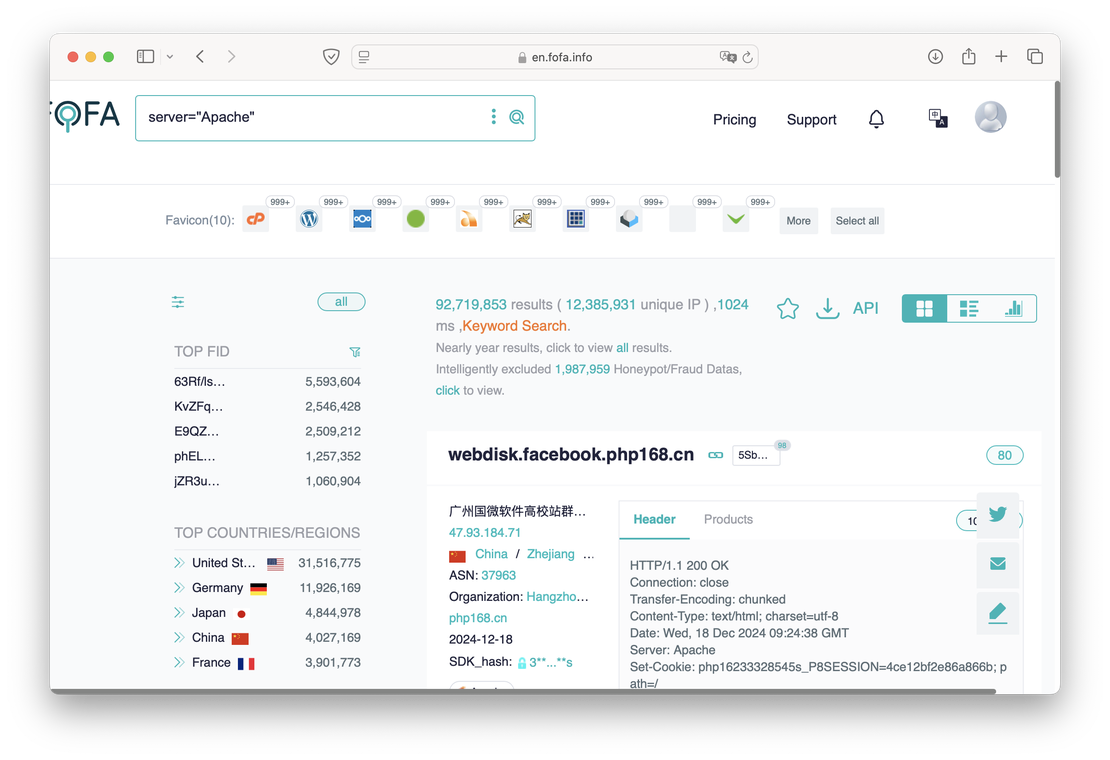
IoT search engines like Netlas and Fofa allow cybersecurity specialists to analyze vast amounts of server responses. These tools help quickly identify potential vulnerabilities, assess network configurations, and ensure the security of the systems they are responsible for protecting.
Both platforms offer powerful search capabilities that enable specialists to explore their data using a range of filters. Users can search by IP address, port, or protocol, allowing for precise targeting of specific network assets. Searches can also utilize technology names (e.g., Apache, Nginx, or OpenSSH) to identify systems running particular services or software versions. For more advanced needs, logical operators such as AND, OR, and NOT can be combined to craft complex queries, helping specialists pinpoint relevant results and uncover hidden vulnerabilities or misconfigurations within large-scale networks.
It’s also worth highlighting the fuzzy search feature. This mechanism allows users to replace specific characters in a query with wildcards (e.g., *), enabling searches for similar but not exact matches. Netlas offers this functionality for free, while in Fofa, fuzzy search is only available starting with the first paid subscription tier.
External Attack Surface Management
Another key feature of both search engines is their suitability for external attack surface management, with dedicated tools designed specifically for this purpose.
In Netlas, these tools include the Attack Surface Discovery Tool and the Private Scanner.
The Attack Surface Discovery Tool simplifies and visualizes attack surface mapping. It allows researchers to construct a graph by adding objects of various types and automatically establishing connections between them. To add a new node, the researcher simply clicks on an existing one, selects the desired search operation (e.g., retrieving all subdomains of a domain), and the relevant results are automatically added to the graph. This process can be repeated iteratively until the graph meets the research objectives.
The Attack Surface Discovery Tool also includes mechanisms for grouping and excluding nodes, offering greater flexibility during research. Objects of the same type can be grouped into a single node, which can then serve as the starting point for group searches. Researchers can manually delete specific results from the group if needed. Unnecessary nodes can be excluded as well. Excluded nodes remain visible on the graph but lose all functionality. If the user decides to export the attack surface as a file, these nodes will be omitted. To simplify the view, excluded nodes can also be hidden with a single click.
The following image demonstrates an example of a graph created using the Attack Surface Discovery Tool.
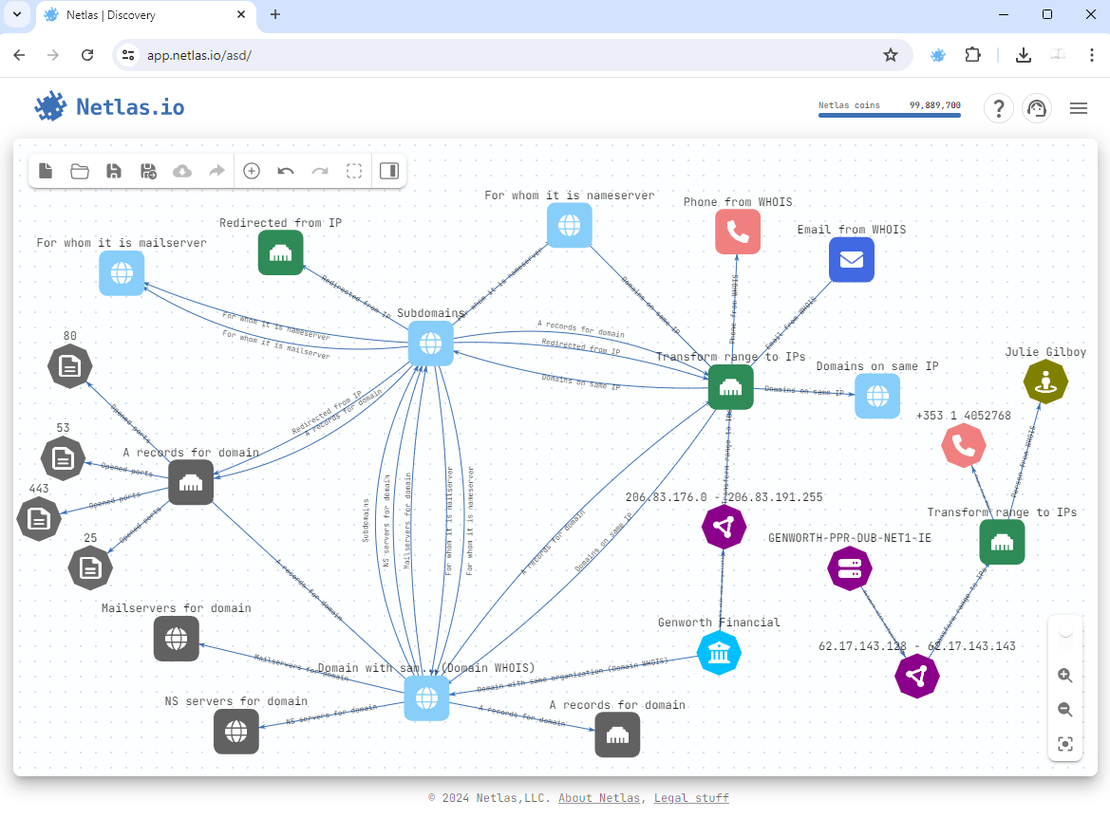
The Private Scanner complements the Attack Surface Discovery Tool by providing up-to-date data on a user’s attack surface through Netlas’s scanners. Researchers simply need to input a list of targets, which are then scanned across more than 1,200 ports. The collected data is stored in a private index, where relevant tags — such as CVEs or product information — are automatically applied. Searching within this private data is as straightforward as searching Public Data using the Responses Search Tool.
A key convenience of the Private Scanner is its seamless integration with the Attack Surface Discovery Tool. With just one click, users can initiate a scan directly from their constructed graph, significantly simplifying the attack surface analysis process and reducing it to two steps.
Recommended Reading
Complete Guide on Attack Surface Discovery
The following image showcases the Private Scanner interface.
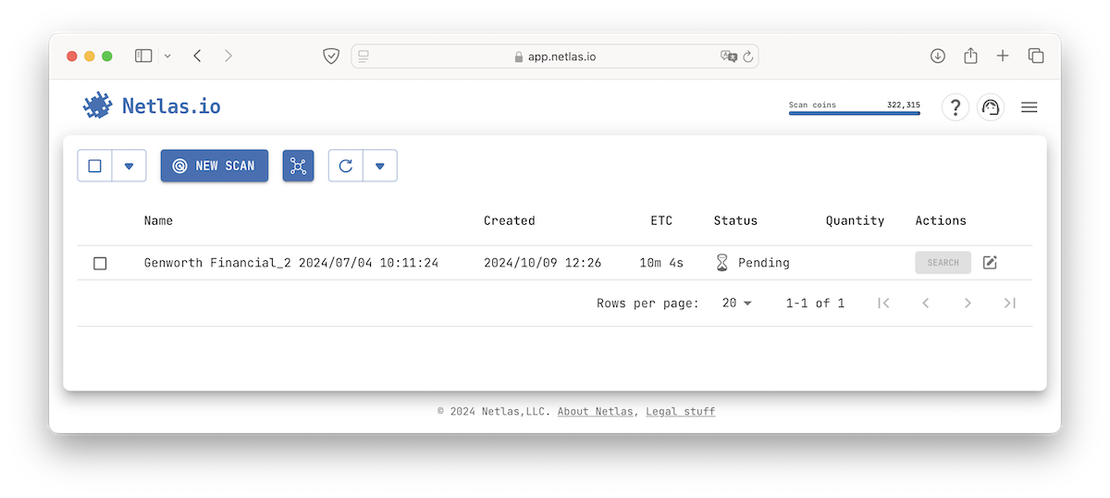
Fofa, on the other hand, offers a tool for External Attack Surface Management called Attack Surface Inventory, which is located in the user’s Personal Center.
This tool is designed to quickly extract key attack surface elements based on Fofa’s previous scans. To initiate a search, users simply enter a root domain, and the Attack Surface Inventory will provide basic information such as subdomains, issuing organizations for the servers, associated favicons, and more.
The following image demonstrates an example of the Attack Surface Inventory in action.
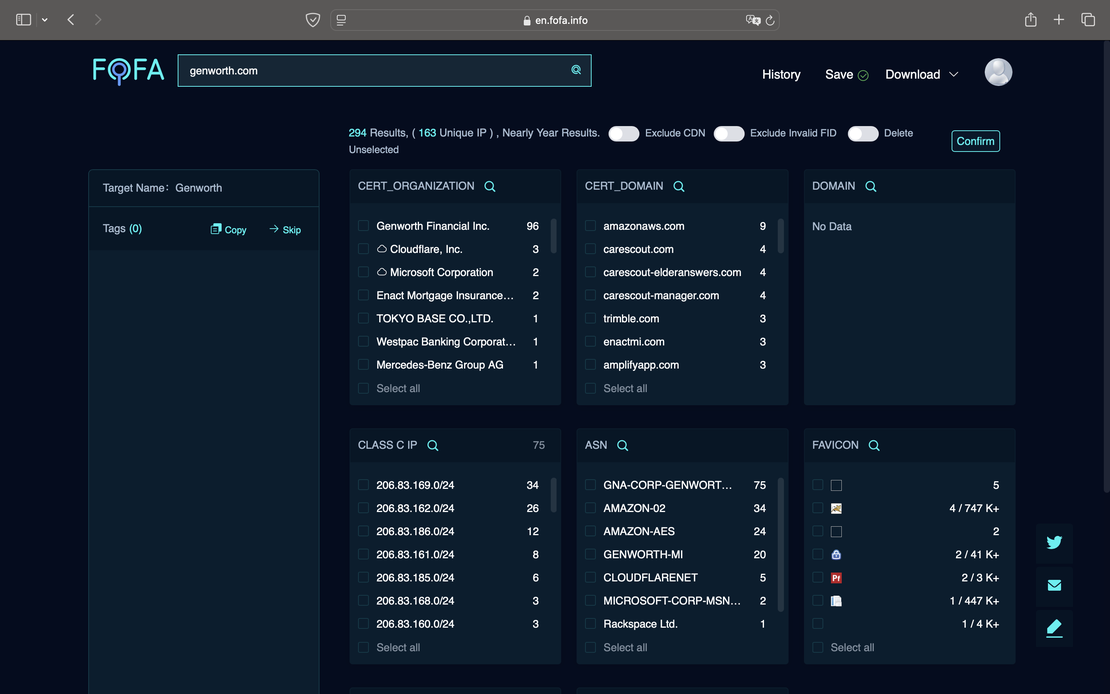
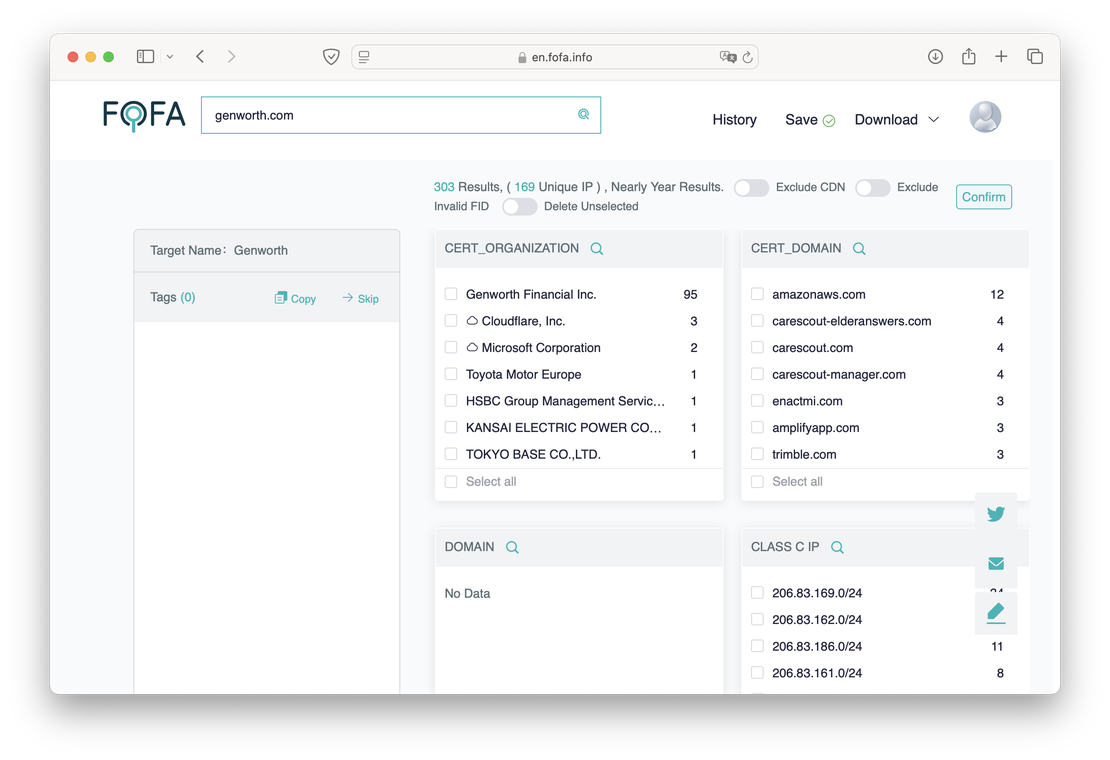
You can read more about using this tool in the corresponding guide.
Seeing is Believing
See how Netlas can elevate your threat analysis. Book a quick demo with our team.
CLI and API
Both search engines support automation via API, Netlas also supports command line usage. To install it, enter the following command:
pip install netlasAn example of usage is shown in the following image.
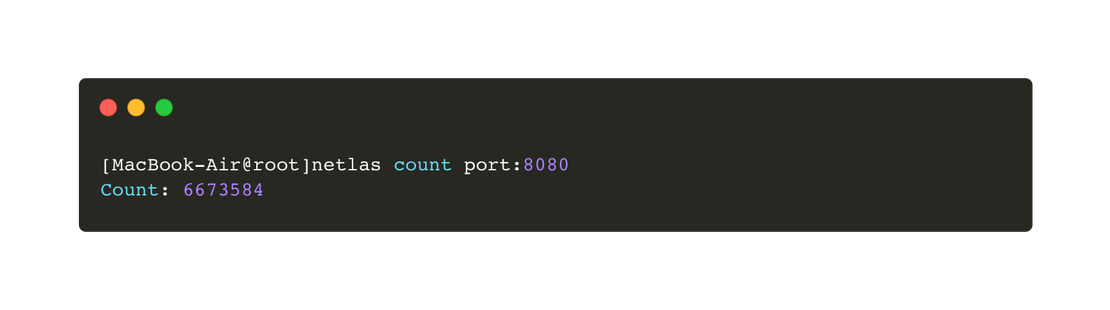
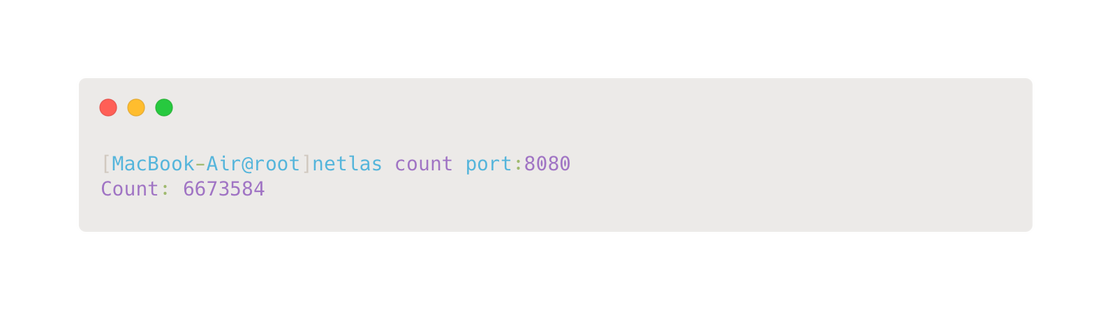
Additionally, when working with Python, users can import the netlas module to access all search engine features directly from their scripts. Detailed instructions and examples are available in the official documentation.
Fofa, on the other hand, does not provide a dedicated command-line tool or wrapper modules. Instead, developers are encouraged to interact with Fofa’s API endpoints directly. For example, this can be accomplished using the cURL utility as shown below:
curl -X GET https://fofa.info/api/v1/search/all?&key=your_key&qbase64=dGl0bGU9ImJpbmciQueries can also be integrated into scripts written in languages such as Java, Go, and Python. For more details, you can refer to the API documentation for this platform.
It’s important to note that access to the Fofa API is only available with a paid subscription. In contrast, the Netlas API can be used starting from the free Community tier. We will discuss subscription options in more detail later.
Other Ways to Use
In addition to the web version and API, both search engines can be used through various third-party applications. In this subsection, I will provide a brief summary of such features.
- Browser Plugins: Both Netlas and Fofa offer the ability to perform searches through browser plugins. For Google Chrome, you can install them here: Netlas, Fofa. For Mozilla Firefox, the plugins are available here: Netlas, Fofa. It is important to note that the Fofa plugins are unofficial and developed by independent enthusiasts. As a result, Fofa does not take responsibility for their functionality or performance.
- Modules for Maltego: Maltego is one of the leading tools for reconnaissance, automation, and visualization of results. Both search engines discussed here can be integrated into Maltego using dedicated modules. You can find more details about Netlas integration in the corresponding article, and about Fofa integration in this manual. However, it is important to note that, similar to browser plugins, the Fofa integration is unofficial and created by independent developers, meaning it is not supported by Fofa itself.
- Data Files and Streaming API: For users who prioritize anonymity and prefer processing data on their own servers, Netlas offers two solutions: Datastore and Streaming API. The Datastore allows users to purchase datasets containing specific types of data, such as scanned records and database responses. The Streaming API provides continuous access to data directly from Netlas scanners for real-time processing and analysis. These features are available as part of paid plans, with additional benefits for Corporate and Enterprise-level users.
This concludes the overview of the most significant features of both search engines. As demonstrated, they are largely similar in their core capabilities; however, Fofa lacks certain functionalities, such as a convenient CLI and the ability to access data anonymously.
Let’s now examine some of the smaller, yet noteworthy, features.
Minor Capabilities
In this short section, we will look at additional features that make working with search engines easier or provide new opportunities.
Netlas Tools
Let’s begin with the additional tools provided by Netlas. Beyond the previously mentioned Responses Tool, Attack Surface Discovery Tool, and Private Scanner, Netlas also offers the following:
- IP/Domain Info. This tool enables users to quickly retrieve summary information about a domain name or IP address. The data includes open ports, reputation details, and key fields from the WHOIS protocol.
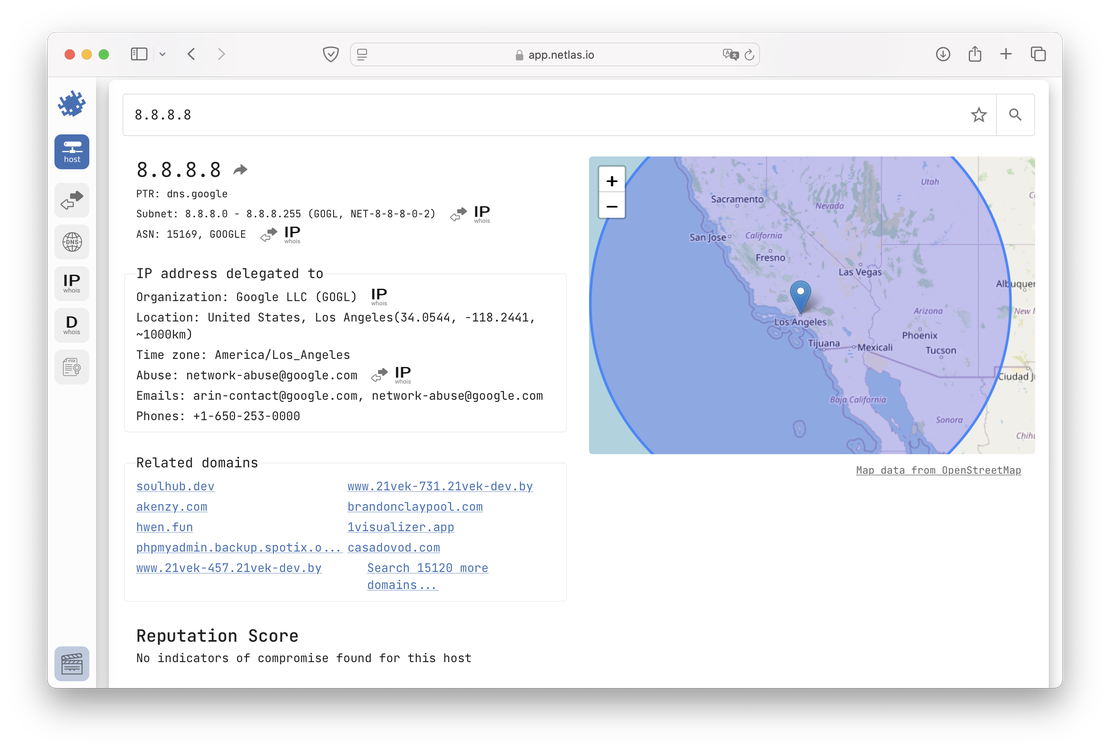
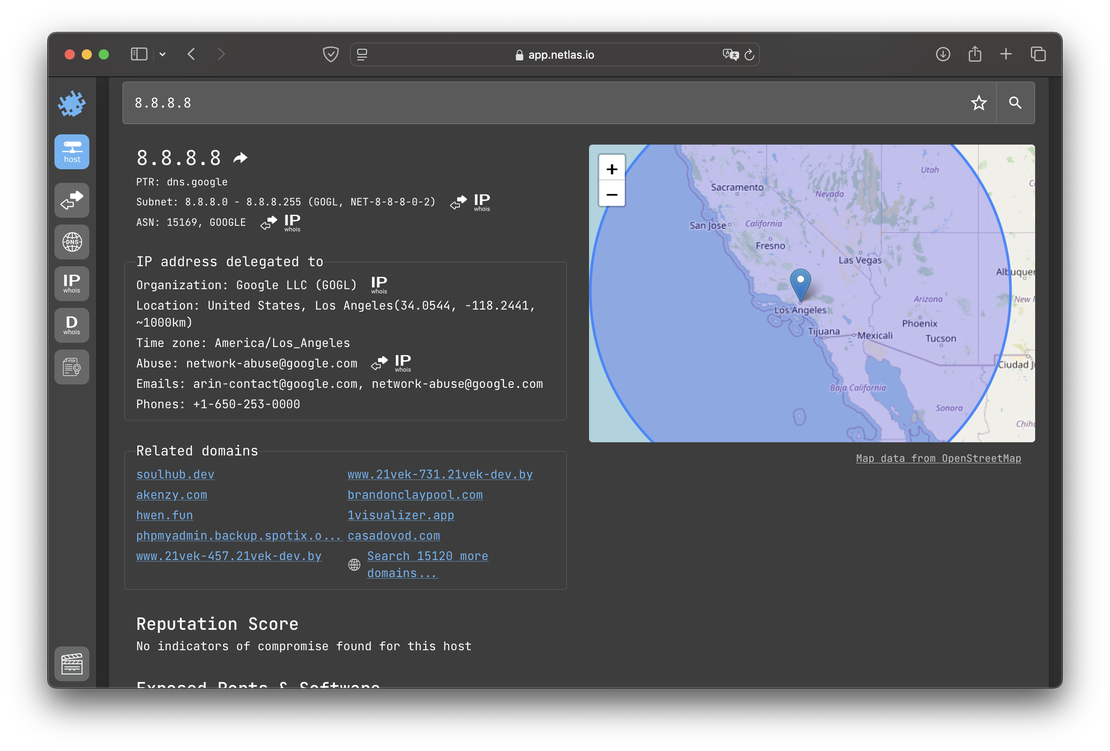
DNS Search. The primary function of this tool is to provide users with detailed information about DNS records. It supports both forward DNS search and reverse DNS search, allowing for comprehensive DNS analysis.
IP WHOIS Search. This tool allows users to search within WHOIS protocol fields. Netlas collects WHOIS data for every existing IP address, making it a valuable resource for investigations or attack surface mapping.
Domain WHOIS Search. This tool is similar to the previous one, but it focuses on WHOIS protocol data for domain names instead of IP addresses.
Certificates Search. This tool allows users to search within SSL certificate fields. It is particularly useful for identifying devices and services that use specific certificates.
Netlas Team Access
Another useful feature in Netlas is team access. By joining a team, users can view private scans and attack surface discovery graphs shared by the owner. This collaborative functionality simplifies data sharing and improves teamwork. An example of the team access interface is shown in the following image.
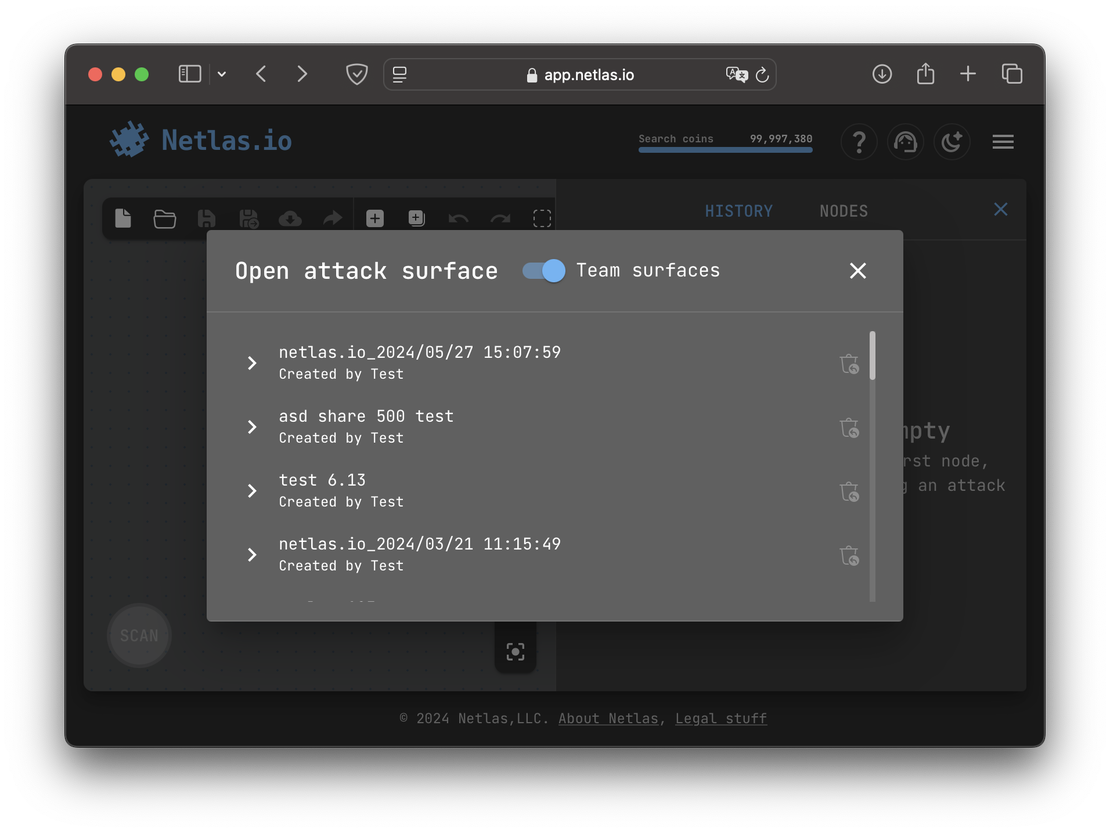
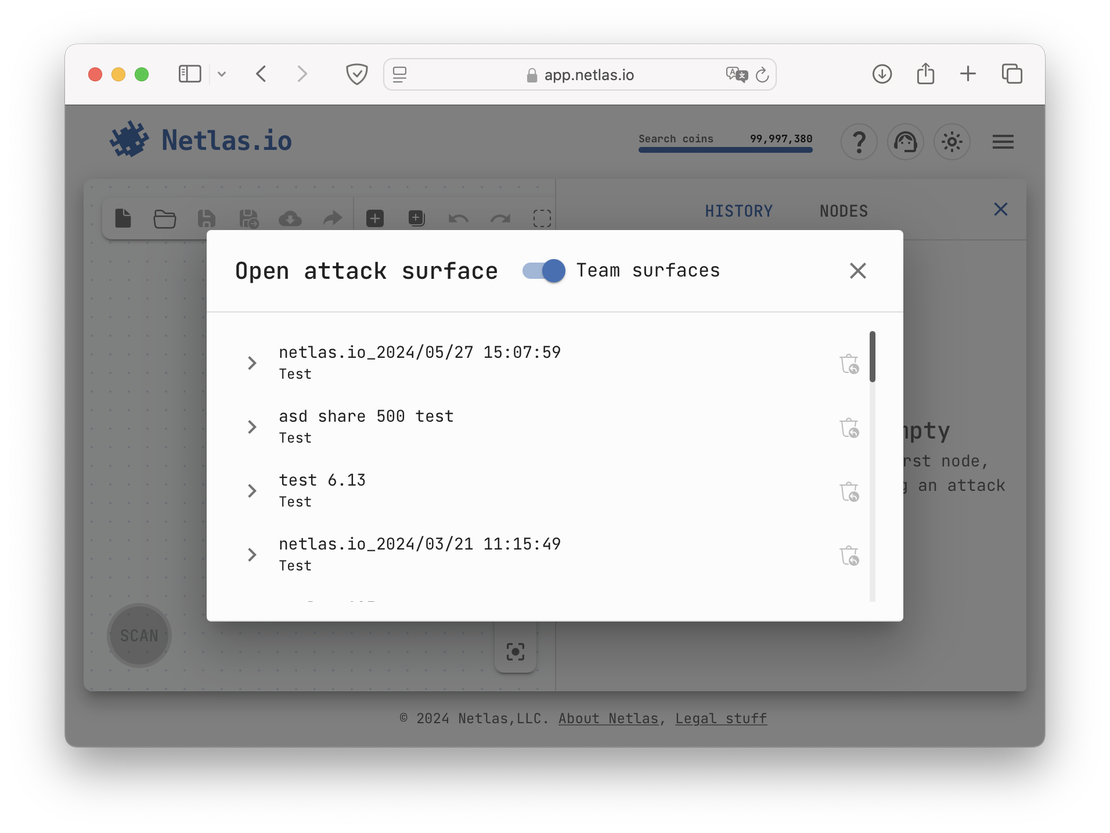
This setup greatly streamlines collaborative work, as team members can easily access shared results in one place. Without this feature, users would need to share attack surfaces as separate documents, which could significantly slow down the workflow.
Fofa Tools
Like Netlas, Fofa also provides several additional tools, which can be accessed through the Personal Center. Let’s take a closer look at them:
- Cloud Service API. A tool designed to find the source IP of CDN or Cloud WAF, such as Cloudflare, StackPath, etc.
- FofaHub. It is an utility designed to automate and visualize queries within Fofa. It operates on a block-based programming model, similar to the Scratch programming language, enabling users to build complex query workflows with ease. This approach allows for the creation of advanced scripts and processes without requiring traditional coding skills. For more information on how to use FofaHub, refer to this article. The following image illustrates an example of a script developed using this tool.
Features Comparison Summary
So, having considered this point, we can summarize all the information received. For this, I made a small table.
| Feature | Netlas | Fofa |
|---|---|---|
| Responses Search | + | + |
| API | Free users | Paid users |
| Automation | Python SDK, CLI util | Built-in automation engine |
| EASM Tools | Visual Discovery, Private Scanner | Attack Surface Inventory |
| Browser Plugins | Chrome, Firefox | Chrome, Firefox |
| DNS Data | A, AAAA, CNAME, MX, NS, TXT | A, AAAA, CNAME |
| Certificates Data | + | + |
| WHOIS Data | + | - |
| Vulnerability Data | + | - |
| Host Reputation | + | - |
Technical Differences
Before comparing the volume and relevance of data, it is important to understand the differences in scanning methods employed by Netlas and Fofa. In this section, we will explore their unique approaches to scanning, how they label data, and the number of ports each search engine scans.
Scan Differences
Netlas begins by assuming the presence of a specific protocol for the scanned port and then verifies whether the service matches the expected protocol. If the service does not match, it is labeled as RAW. If the protocol is confirmed, the service is recorded as the initially detected protocol.
At the same time, we were unable to determine exactly how Fofa detects protocols. However, there is another important nuance in its scanning technology that is worth mentioning.
When using Fofa, it is important to note that its crawler tends to collect information primarily from service headers rather than their content. For example, a website running on the popular port 80 might be scanned daily, but only the headers are updated. The website’s body may have been scanned weeks ago and could remain outdated.
This approach distinguishes Fofa from Netlas, whose crawlers collect both headers and content simultaneously.
Number of Scanning Ports
It is also important to note that the number of ports scanned by both search engines is limited.
For public data collection, Netlas scanners examine up to 146 ports per IP address, including 141 TCP ports and 5 UDP ports. A detailed list of these ports is available in the relevant section of the documentation. While this number may seem restrictive, the Private Scanner can mitigate the limitation by increasing the number of scanned ports to approximately 1,300.
At the same time, Fofa scans more than 1,200 ports. While the exact list is not publicly available, we conducted a comparison using the list of ports scanned by Shodan. Fofa successfully scanned all of these ports.
Recommended Reading
Netlas vs Shodan: Platforms Comparison
Scanning Timing
As previously mentioned, Fofa does not scan all ports with the same frequency. During our research, we observed cases where some ports on the same IP address were scanned just a day ago, while others had not been updated for several weeks. This discrepancy arises because Fofa’s crawlers prioritize more frequently used ports.
In contrast, Netlas crawlers treat all ports as equally important. As a result, when an IP address is scanned, the scan date applies uniformly to all of its open ports, regardless of their popularity.
These differences can potentially mislead users when evaluating data relevance between the two systems. If comparisons focus solely on the date of the last IP address scan, Fofa might seem to have an advantage. However, as demonstrated in the experiment in the next section, the overall freshness of the data is generally comparable when greater attention is given to the ports.
Request Your Free 14-Day Trial
Submit a request to try Netlas free for 14 days with full access to all features.
Volume and Relevance of Data
The most valuable metric for any search engine is the amount of data it can provide and its relevance. In this section of the article, we will conduct several tests, comparing Netlas and Fofa in this regard.
First, it should be noted that we could conduct research simply by the query *. However, firstly, this is not interesting, and secondly, it does not reflect the full picture. Therefore, the following tests were taken: 5 popular ports, 5 popular web servers, 5 popular DBMS and 10 recent vulnerabilities.
All these objects were found both in Netlas (current General Data index) and in Fofa (data for the last month).
Volume Tests
The first test is dedicated to port analysis. Its results are in the table below.
| Port | Netlas | Fofa |
|---|---|---|
| 80 | 344,649,754 | 66,085,975 |
| 443 | 285,487,197 | 58,707,782 |
| 7547 | 28,938,904 | 41,837,069 |
| 22 | 16,128,472 | 26,860,768 |
| 161 | 18,450,728 | 19,306,119 |
Netlas demonstrates a clear advantage when it comes to web ports 80 and 443. This result is unsurprising, as Netlas places greater emphasis on domain names rather than solely focusing on IP addresses, a distinction that sets it apart from many competitors. On port 161, the results show approximate parity, while for the remaining ports, Fofa takes the lead.
Overall, both search engines performed comparably in this test. Let’s proceed to the next evaluation: popular web servers.
| Web Server | Netlas | Fofa |
|---|---|---|
| Nginx | 123,862,604 | 21,239,380 |
| Apache | 72,716,713 | 12,347,906 |
| Microsoft IIS | 18,609,097 | 3,735,120 |
| Cisco-IOS | 4,346,096 | 58,144 |
| Cloudflare | 149,442,851 | 986,526 |
In this test Netlas leads in all cases, sometimes by a significant margin. The reason for this stems from the already mentioned attention paid to web ports during development.
Next we will look at popular databases.
| Database | Netlas | Fofa |
|---|---|---|
| PostgreSQL | 477,224 | 1,020,013 |
| MongoDB | 90,442 | 277,041 |
| MySQL | 2,732,712 | 4,532,897 |
| Elastic | 711,743 | - |
| CouchDB | 5,204 | 429,284 |
In this experiment, Fofa holds the palm. The only exception is Elastic. Netlas can easily find it, since this DBMS has a frequently used web interface, while Fofa failed to detect a single object at all.
Finally, let’s move on to the fourth test, CVEs.
| CVE | Netlas | Fofa |
|---|---|---|
| CVE-2024-39710 (Ivanti Connect Secure) | 16,488 | 106,666 |
| CVE-2024-45763 (Dell SonicOS) | 17,112 | 12,830 |
| CVE-2024-46538 (pfSense) | 55,660 | 24,080 |
| CVE-2024-49768 (Waitress Python Server) | 20,793 | 22,287 |
| CVE-2024-50388 (QNAP NAS) | 112,519 | 110,172 |
| CVE-2024-46483 (Xlight FTP) | 2,122 | 2,336 |
| CVE-2024-45157 (Rancher) | 3,461 | 5,756 |
| CVE-2024-9264 (Grafana) | 99,139 | 115,308 |
| CVE-2024-49193 (Zendesk) | 19,541 | - |
| CVE-2024-3656 (Keycloak) | 12,626 | 24,890 |
In this test, we once again observe approximate parity: some products are better detected by Netlas, while others are more effectively found by Fofa.
Therefore, when considering Data Volume alone, there is no clear winner in this comparison. Each engine excels in its respective areas, and the choice of which to use ultimately depends on the specific needs and objectives of the researcher.
Data Relevance
When it comes to data relevance, both search engines offer similar performance.
Netlas crawlers typically go through the entire Internet every 3 weeks. You can confirm this by reviewing the crawl periods on the About page. Unfortunately, Fofa, as in the case of scanned ports, does not provide this information in open form.
In this regard, it was decided to conduct a small test that would allow us to experimentally calculate the average age of the data. To perform this test, the script randomly generated two senior octets of an IP address, from which a subnet with a /16 mask was selected. Two addresses in this subnet were randomly chosen from the available data in both search engines, and their scan age was recorded for comparison.
It is important to reiterate that Fofa and Netlas differ in how they scan the contents of services. For this comparison, we included only those responses that were fully scanned, such as bodies, banners, and other relevant data.
| Average Data Age, days | |
|---|---|
| Netlas | 18 |
| Fofa | 21 |
The results indicate that, based on this small test, the average relevance of Netlas’ data is slightly better than that of Fofa. However, it’s important to keep in mind the restrictions outlined in the Technical Differences section. In our study, we focused only on ports that matched in both search engines, with full content, but alternative approaches could be employed, such as considering the scan date for IP only or the timing of the first ports scanned.
Engines Limitations
After reviewing the capabilities of both search engines, it is essential to consider their limitations. Not all features are available to every user, as some are restricted to paid subscription plans.
In this section, we will provide the subscription plan tables for Netlas and Fofa, along with a summary table outlining the minimum required plan for accessing various features.
Netlas Plans
| Plan | Cost at month |
|---|---|
| Community | 0 $ |
| Freelancer | 49 $ |
| Business | 249 $ |
| Corporate | 830 $ |
| Enterprise | Custom |
Fofa Plans
| Plan | Cost at month |
|---|---|
| Registered User | 0 $ |
| Personal | 49 $ |
| Professional | 149 $ |
| Business | 1,499 $ |
| Corporate | 5,400 $ |
As you can see, the prices are roughly comparable. While Netlas is generally more affordable in most cases, Fofa frequently offers discounts that can narrow or even eliminate this gap. That said, pricing alone does not determine the value of these tools.
Next, we will present a summary table that highlights the capabilities of both search engines and specifies the subscription plan required to access each feature.
Features
| Feature | Plan in Netlas | Plan in Fofa |
|---|---|---|
| Historical Lookups | Community | Registered User |
| DNS Lookups | Community | Registered User |
| Search by Domain | Community | Registered User |
| Search via API | Community | Personal |
| Search via CLI | Community | Personal |
| Fuzzy Search | Community | Personal |
| Commercial Use | Freelancer | Business |
| Scanner | Freelancer | Corporate |
| Search by Vulnerability | Business | - |
| Search by Tags | Business | Professional |
| Bulk Data Files | Enterpise | - |
It becomes clear that many features common to both search engines are only available in Fofa starting with paid subscriptions, often at higher tiers. One significant drawback for users is the strict limitations on API access and commercial use.
Additionally, even if your subscription grants API access, some fields may remain unavailable. For example, during our tests for data relevance, we encountered this limitation with the lastupdatetime field, which requires at least a Professional subscription to access.
Another drawback is that fuzzy search is not available in Fofa’s free subscription tier. This limitation can significantly complicate the workflow for independent researchers and enthusiasts who rely on this feature for efficient analysis.
Some of these shortcomings are partially mitigated by the use of F points, an internal Fofa resource that can be purchased (at a rate of $6 for 10,000 points and beyond). By spending F points, users can access certain features unavailable at their subscription level. However, it’s important to note that F points cannot resolve all issues, such as the unavailability of specific API fields.
Ease of Use
This section also touches on some limitations of the search engines. While these points are subjective and do not affect the overall results of our comparison, they are still worth mentioning for a more complete perspective.
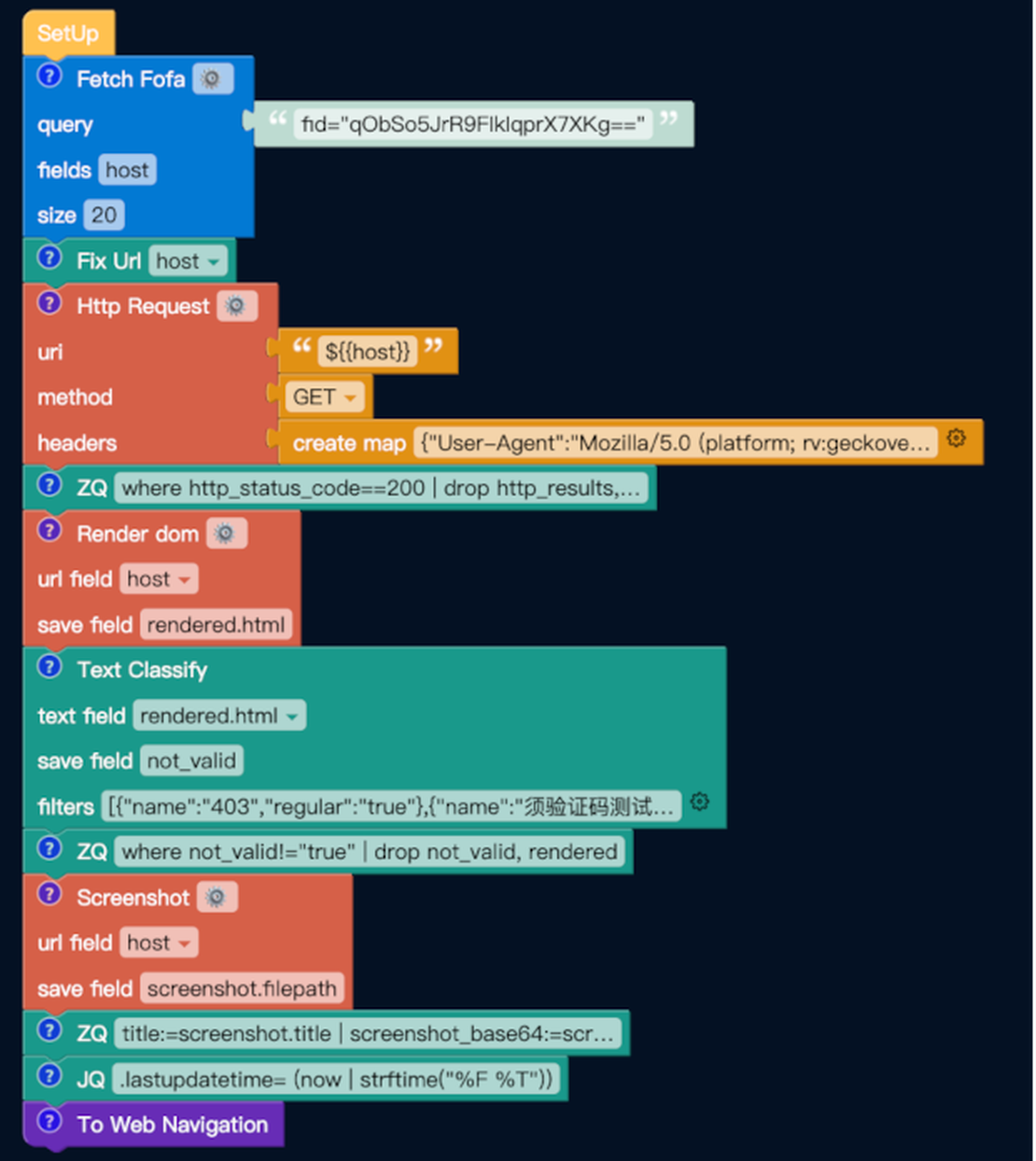
- Queries Creation. Most queries in Fofa are limited to IP addresses, products, domains, or simple terms entered into the search bar. While this works well for basic searches, it becomes restrictive when building more complex patterns. Netlas, on the other hand, allows for flexible query customization and enables users to search by any field of any detected protocol. In contrast, Fofa doesn’t provide dedicated filters only for specific protocols. All that’s left for users to do is enter the required text into the search bar, hoping that the full-text search will allow them to find the desired field. Another drawback of the Fofa search engine is the lack of autocomplete functionality in its search bar. Netlas addresses this with query suggestions in the Responses Tool, significantly improving search speed and efficiency. The following image demonstrates how these suggestions appear in Netlas.
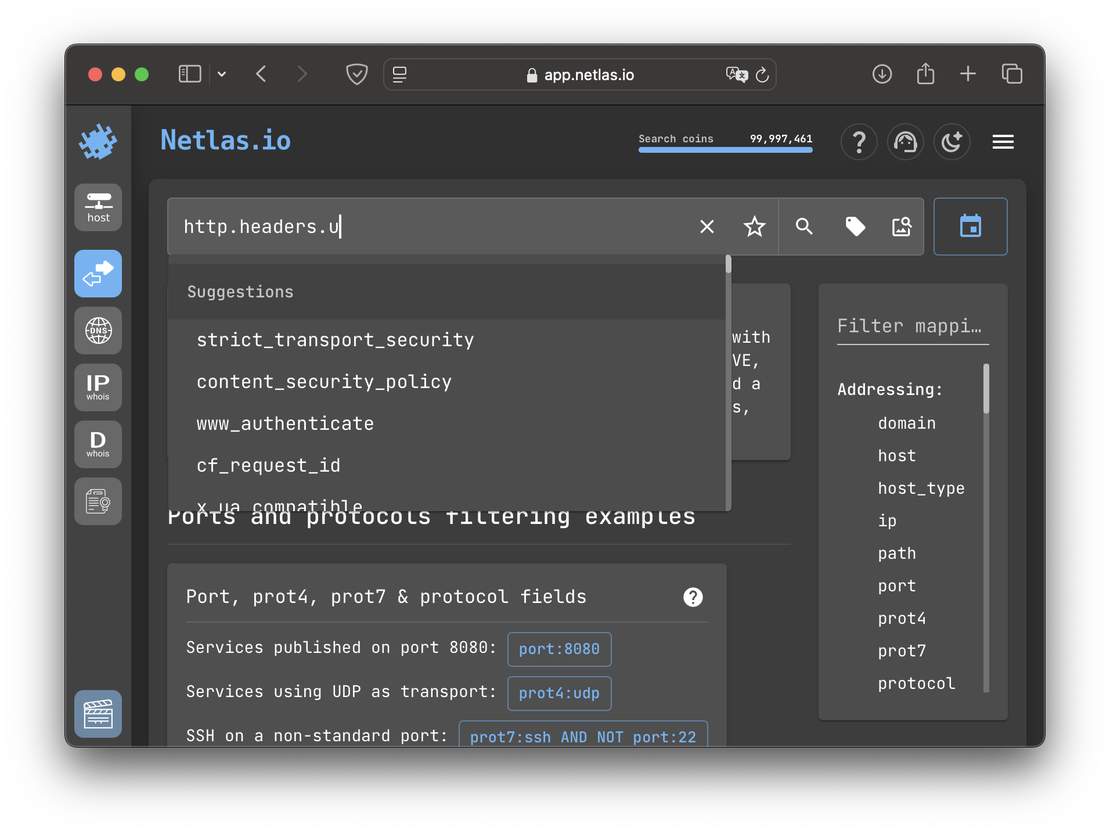
And this is what it looks like in Fofa:
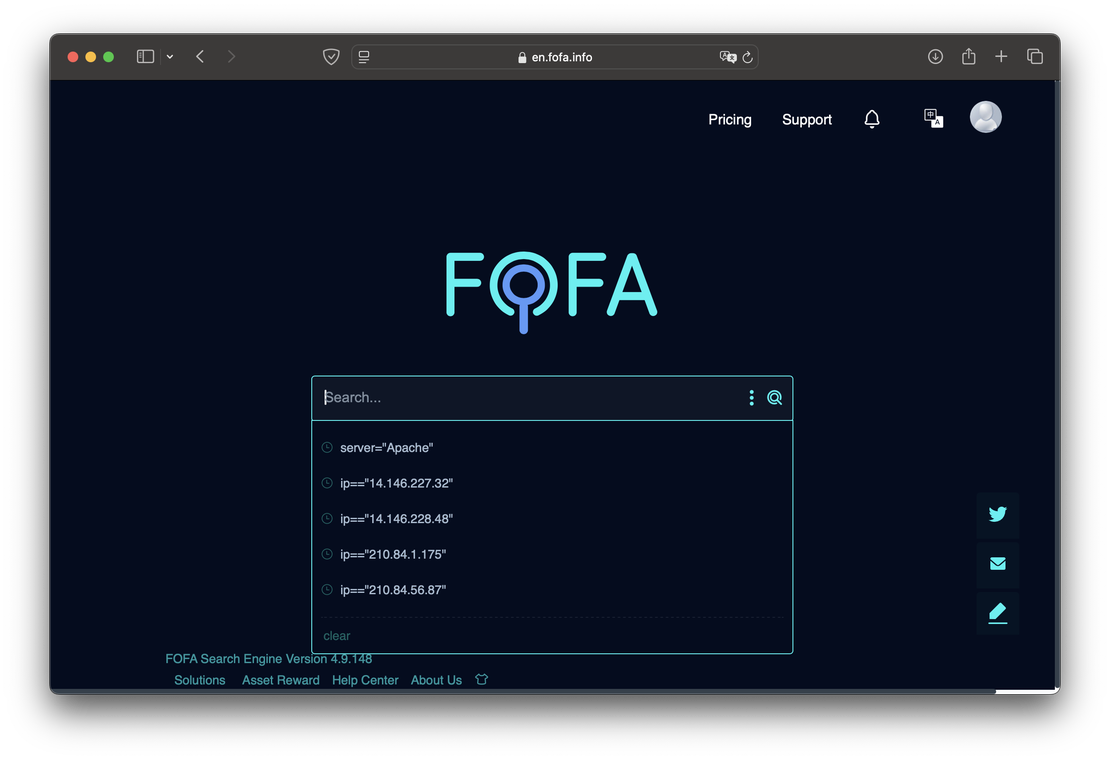
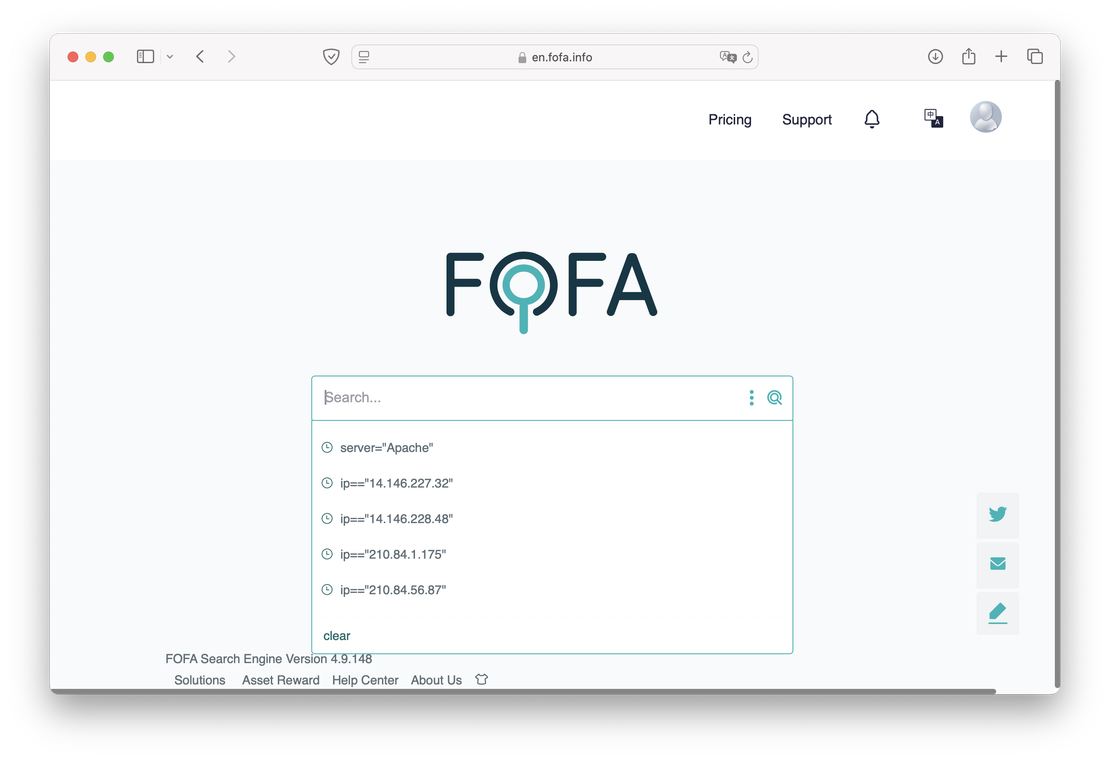
You can see that the engine only shows the search history. There are no prompts when trying to enter something, which can make it difficult for new users.
- Documentation. Fofa provides a solid guide for writing queries and a well-documented API. However, issues arise when it comes to additional features. For example, consider Fofa Open Lab, which includes the Attack Surface Inventory tool, FofaHub, and Cloud Source API. Its description on the website is as follows:
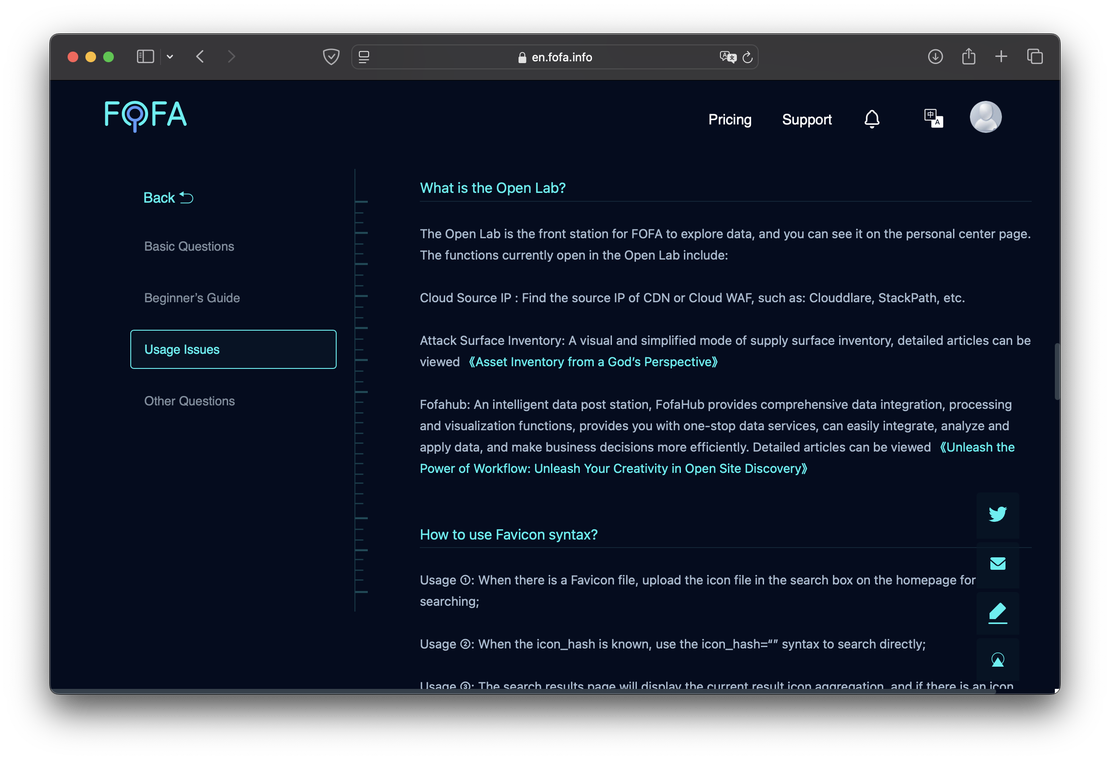
Such a brief description is unlikely to help users fully understand the tools. While there are links to articles hosted on GitHub, these primarily focus on practical examples and specific use cases. If users want to develop something of their own, they will need to study the tools’ capabilities experimentally.
Enterprise Features
Let’s take a closer look at the two highest subscription tiers, which are aimed at large organizations. At these levels, both Netlas and Fofa offer roughly comparable features. This comparison is best illustrated using two pivot tables. We’ll start with Corporate and Business tier plans.
| Feature | Netlas | Fofa |
|---|---|---|
| Price | 830 $ | 1,499 $ |
| Query Credits | Unlimited | 900,000 |
| Scan Credits | 327,680 | 900,000* |
| Available Search Filters | All | All |
| Available Fields in API | All | 38 |
| Number of API Keys | Up to 5** | 1 (Up to 5 users) |
| API requests rate limit | 1 request/sec | 2 requests/sec |
| Hostname Search | + | + |
| Bulk Data Files | - | - |
| Additional Tools | All | Without Open Lab |
Next, we’re going to Enterpise and Corporate tiers.
| Feature | Netlas | Fofa |
|---|---|---|
| Price | Custom | 5,400 $ |
| Query Credits | Unlimited | Custom |
| Scan Credits | Unlimited | Custom |
| Available Search Filters | All | All |
| Available Fields in API | All | All |
| Number of API Keys | Custom | Custom |
| API requests rate limit | Custom | 5 requests/sec |
| Hostname Search | + | + |
| Bulk Data Files | + | - |
| Additional Tools | All | All |
* - Fofa does not differentiate between types of credits; they are used uniformly across all functions. As a result, Business-level users receive 900 000 credits, which can be spent on searches, API usage, Attack Surface Inventory, and other features.
** - It is important to distinguish between the number of users and the number of API keys. In Fofa, multiple users can share a single API key, but they are all subject to the subscription plan’s limits, including a maximum of requests per second. To overcome these restrictions, additional keys would be required, which are not provided by default. Netlas, on the other hand, offers greater flexibility with its Corporate plan. When purchasing this plan, a company effectively acquires five separate licenses, each with its own API key. This setup allows for higher request volumes and more efficient collaboration.
Summary
In conclusion, both search engines offer valuable capabilities that can be utilized depending on the user’s specific needs. Netlas excels in port 80 and 443 analysis, making it particularly useful for pentesters and bug bounty hunters focusing on web-based resources.
Additionally, Netlas provides a broader range of features at a lower subscription cost. Features like free API access can be especially critical for smaller teams or independent researchers. This makes Netlas an excellent choice for small companies operating on a limited budget.
For large organizations, the best approach is to use both tools in tandem. While each has its strengths and limitations, combining them can help mitigate most of the drawbacks and deliver a more comprehensive solution.
Book Your Netlas Demo
Chat with our team to explore how the Netlas platform can support your security research and threat analysis.
Related Posts

November 21, 2024
Netlas vs Shodan: Platforms Comparison

October 9, 2024
Complete Guide on Attack Surface Discovery

July 13, 2024
Best Attack Surface Visualization Tools

June 16, 2025
Google Dorking in Cybersecurity: Techniques for OSINT & Pentesting

September 13, 2024
7 Tools for Web Penetration Testing

August 30, 2024
Using DNS History in Cybersecurity
















