Netlas vs Urlscan: Tools Comparison
June 5, 2025
7 min read
Urlscan.io is a sandbox-based platform for analyzing web pages. It reveals both high-level domain details — such as IP addresses and ASN — and specific page configurations. We’ve had multiple inquiries from users asking how Netlas compares to Urlscan. In this article, we’ll examine both tools and their respective feature sets.
Spoiler alert – these tools serve very different purposes.
Seeing is Believing
See how Netlas can elevate your threat analysis. Book a quick demo with our team.
Features
We’ll begin by examining the features offered by each application. For every capability, we’ll first describe how Urlscan implements it, followed by any comparable functionality available in Netlas.
Main Page
The screenshot below depicts Urlscan’s homepage, which displays a feed of recently scanned websites alongside a search bar for initiating new scans. Users can request scans without registering, though these unauthenticated scans are publicly accessible.
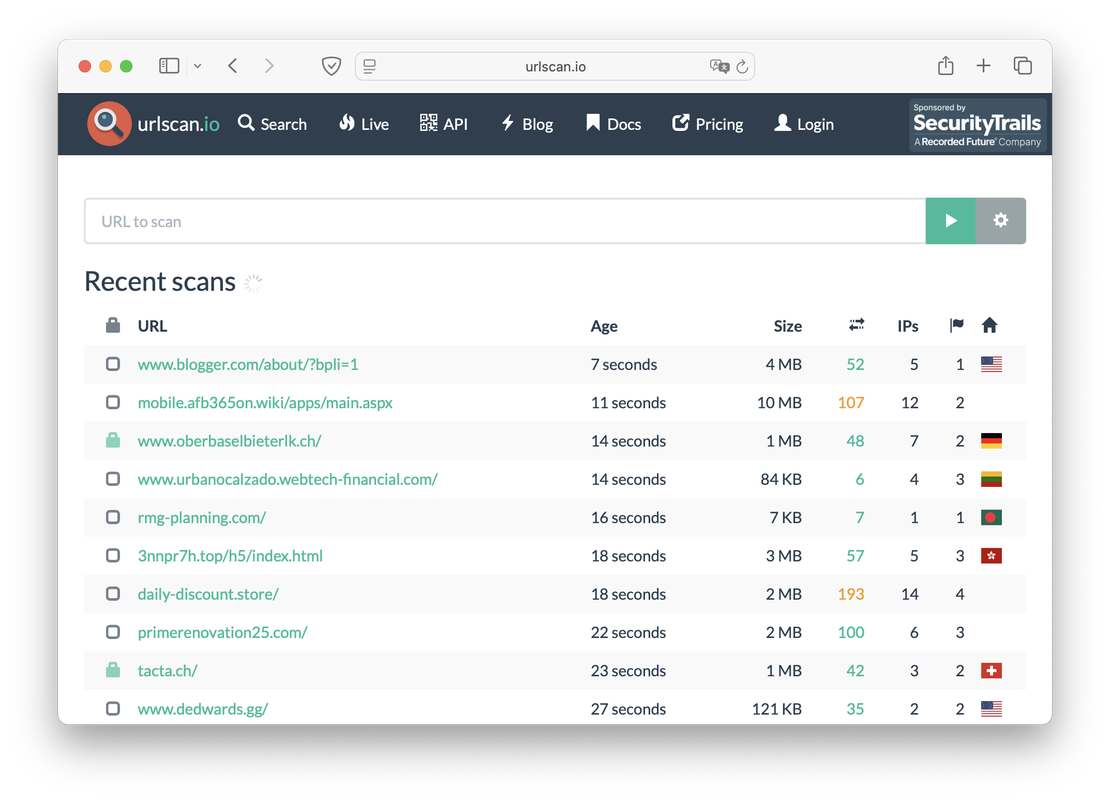
There are three types of scans in the application:
- Public. The scanning result is visible to everyone, the only option that is available for free.
- Unlisted. These scans are visible to their creator, verified security companies and organizations registered on the Pro platform.
- Private. The scan result is visible only to the creator and those with whom he shared the unique ID.
As a test, we will run a scan of the well-known target.com.
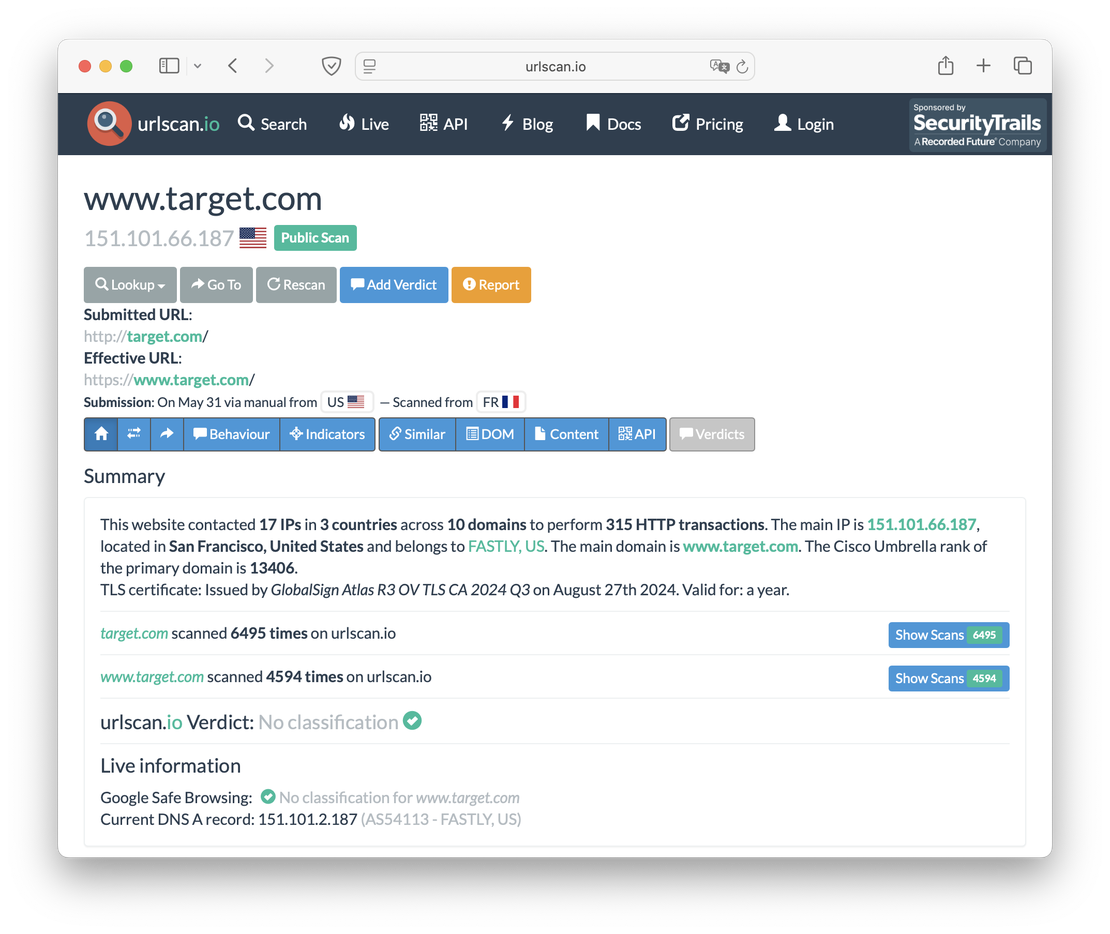
The page displayed above presents key details: the number of times the site has been crawled, the count of associated IP addresses, and the hosting location of its primary A-record. However, the data gathered extends well beyond these metrics.
As for Netlas, the first page a user sees when opening a web application is the IP/Domain Info tool. Let’s request target.com there.
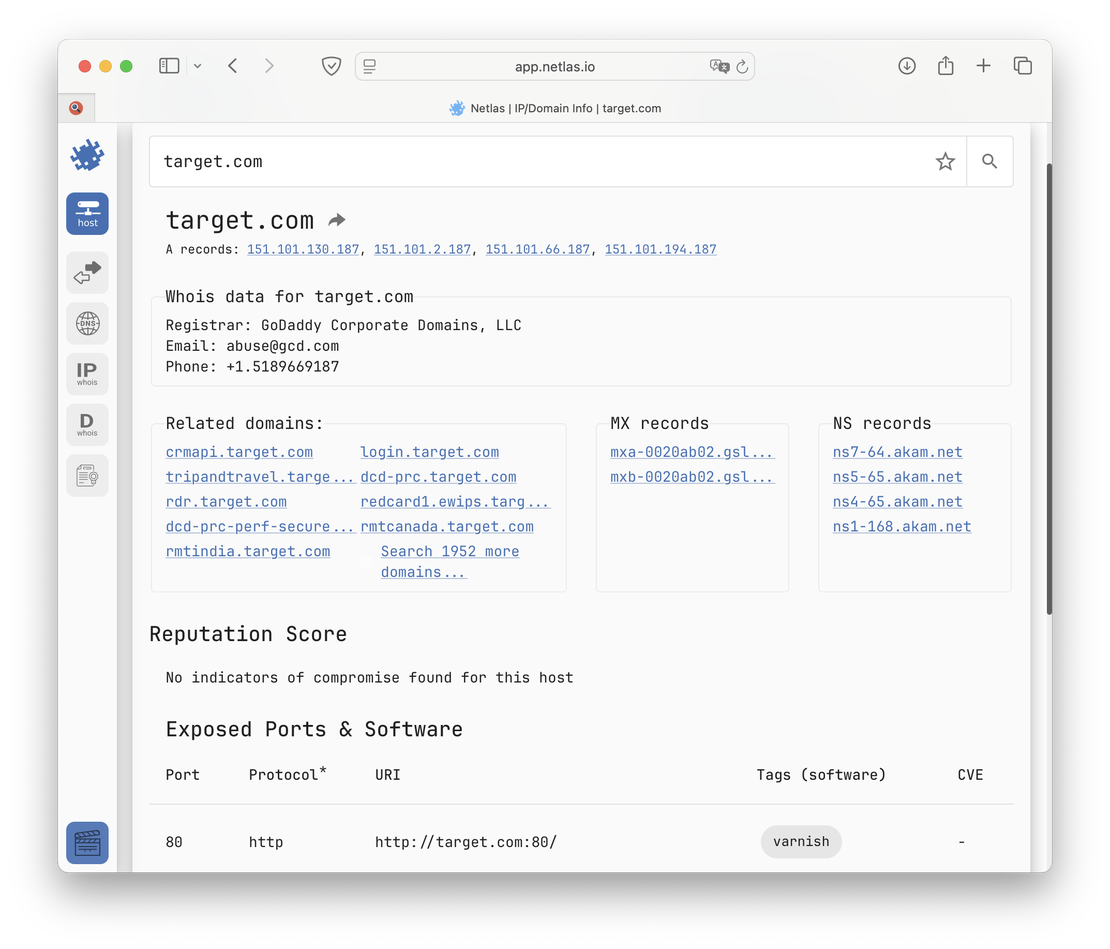
Here, Netlas displays the linked IP addresses and domains, along with a summarized WHOIS record. Additionally, it provides a Reputation Score derived from RST Cloud’s Indicators of Compromise (IoCs).
Let’s delve into the sections of the main pages in more detail.
Domain and IP Info
As the tab name indicates, this section presents fundamental details about the domain and its IP addresses. First, it lists every IP address associated with the site:
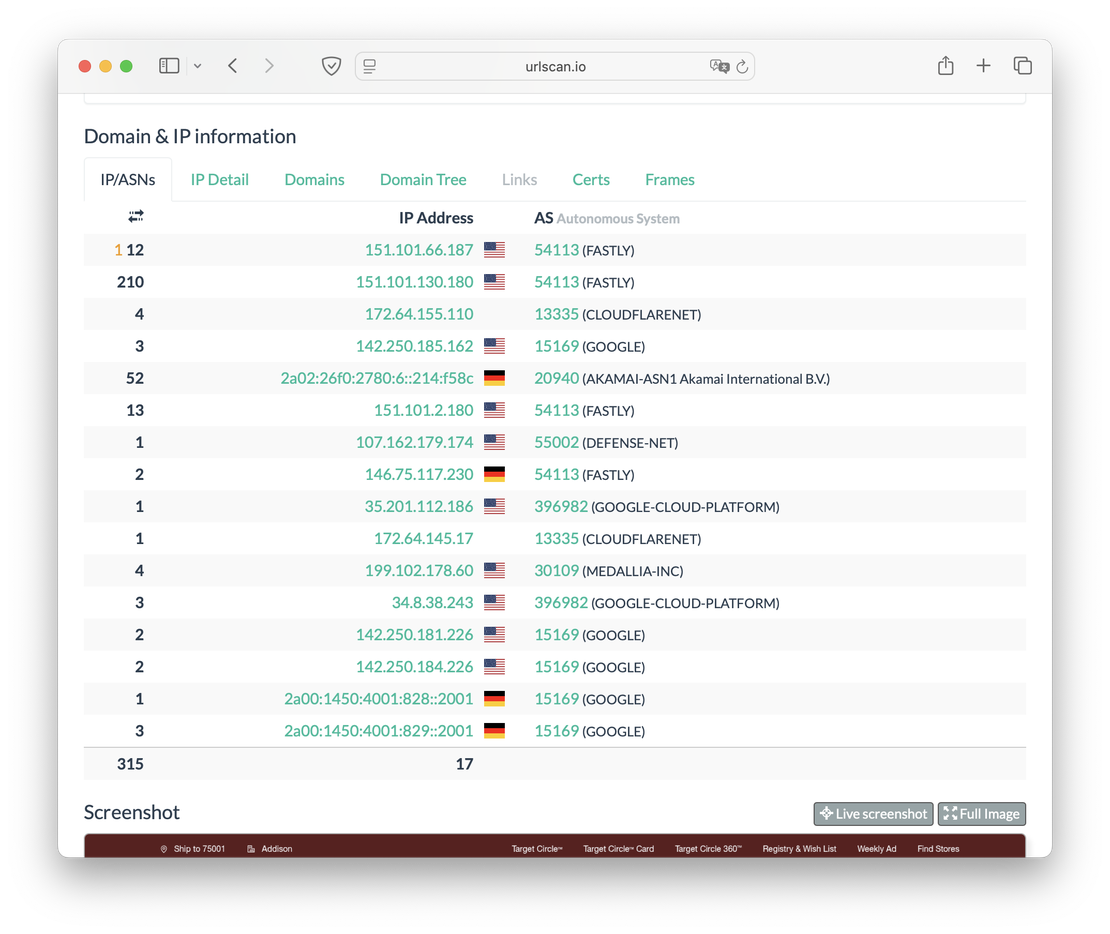
Both the addresses themselves and the autonomous systems they belong to are returned here.
In the case of Netlas, this information is provided in the IP/Domain Info tool.
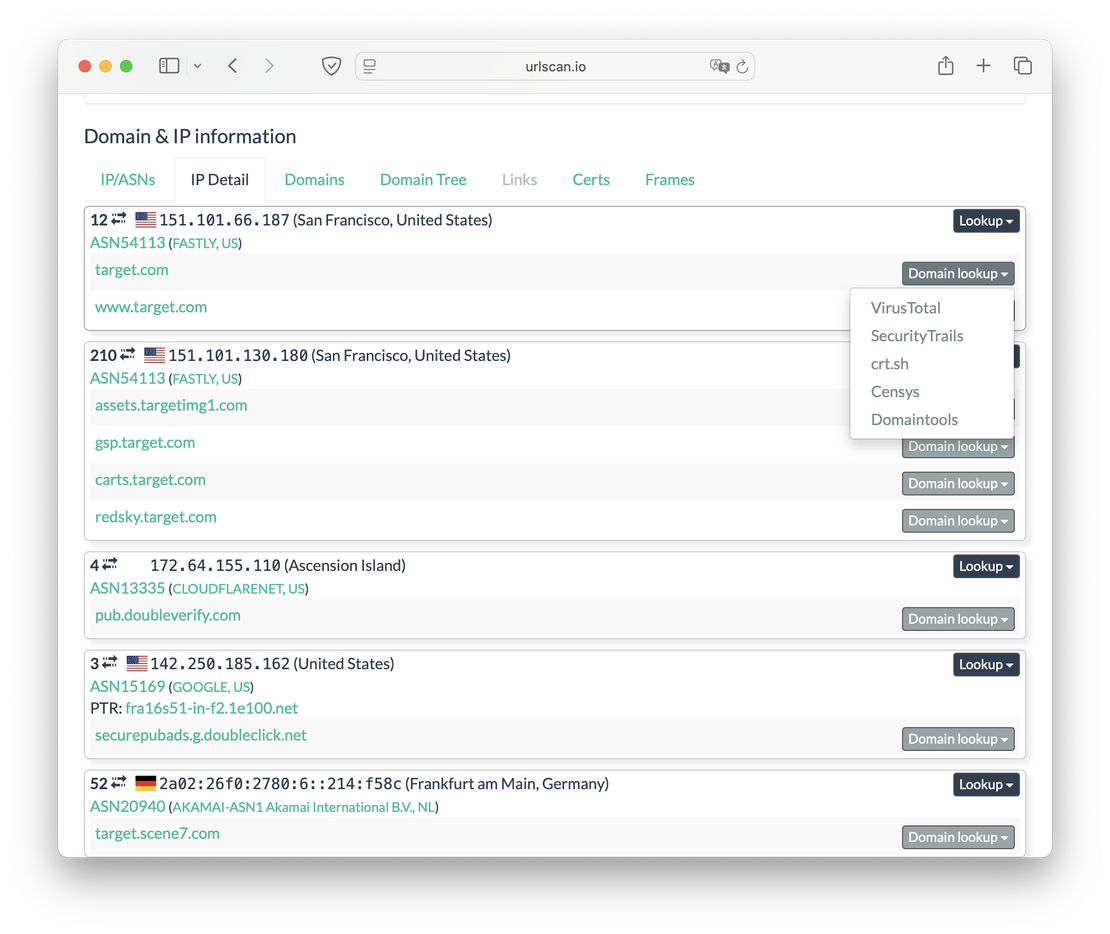
The IP Detail tab offers a deeper dive into each IP address, listing all domains for which it serves as an A record. For every listed domain and IP, users can also view lookups from third-party services like VirusTotal, SecurityTrails, and more.
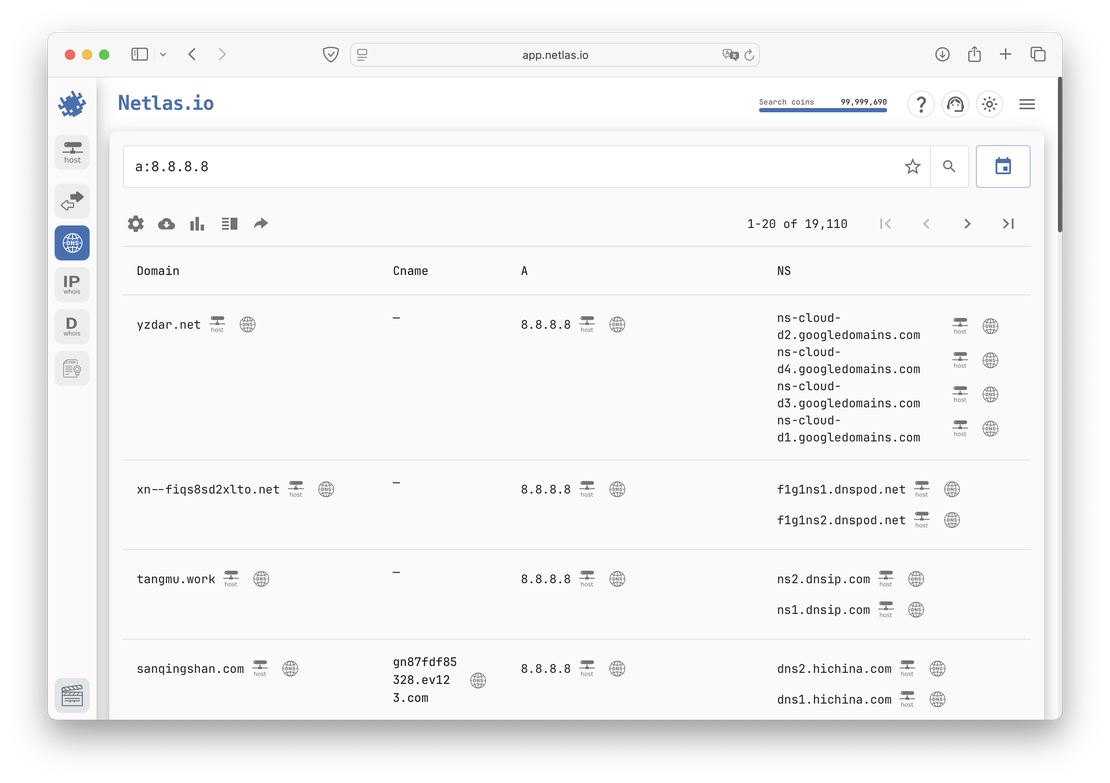
Netlas offers similar functionality through its DNS Search tool. For example, querying a:8.8.8.8 returns all domains for which that IP is an A record. However, unlike Urlscan, Netlas does not include direct links to third-party lookup services in its results.
Next come the Domains and Domain Tree tabs, which contain information about the subdomains of the site you are looking for.
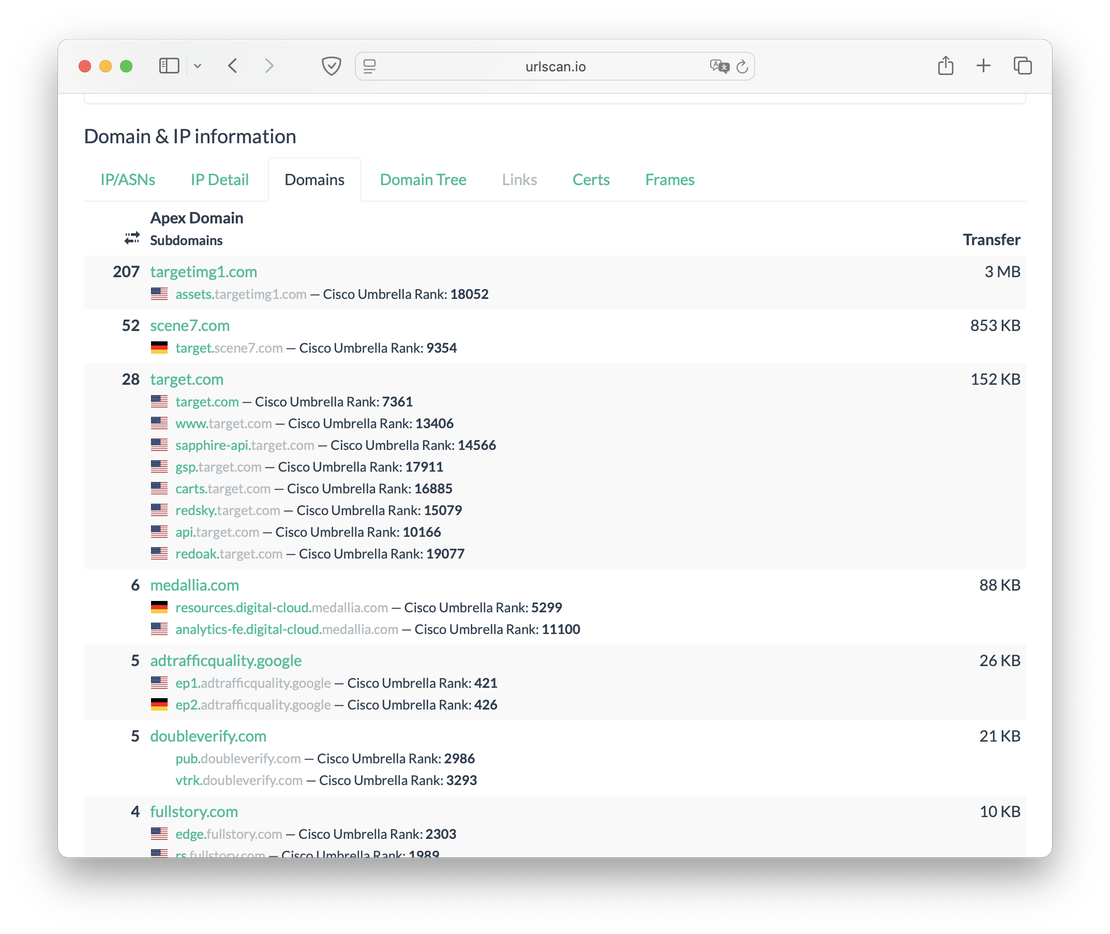
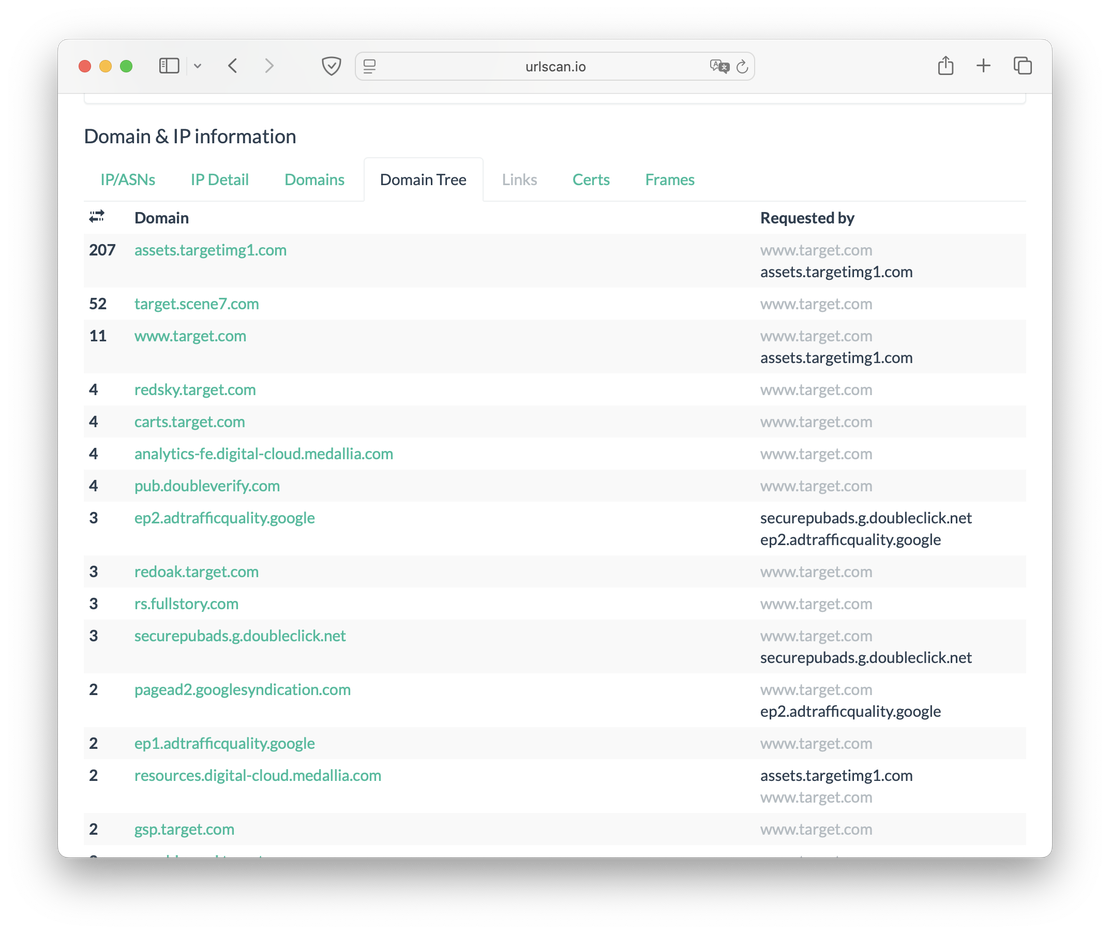
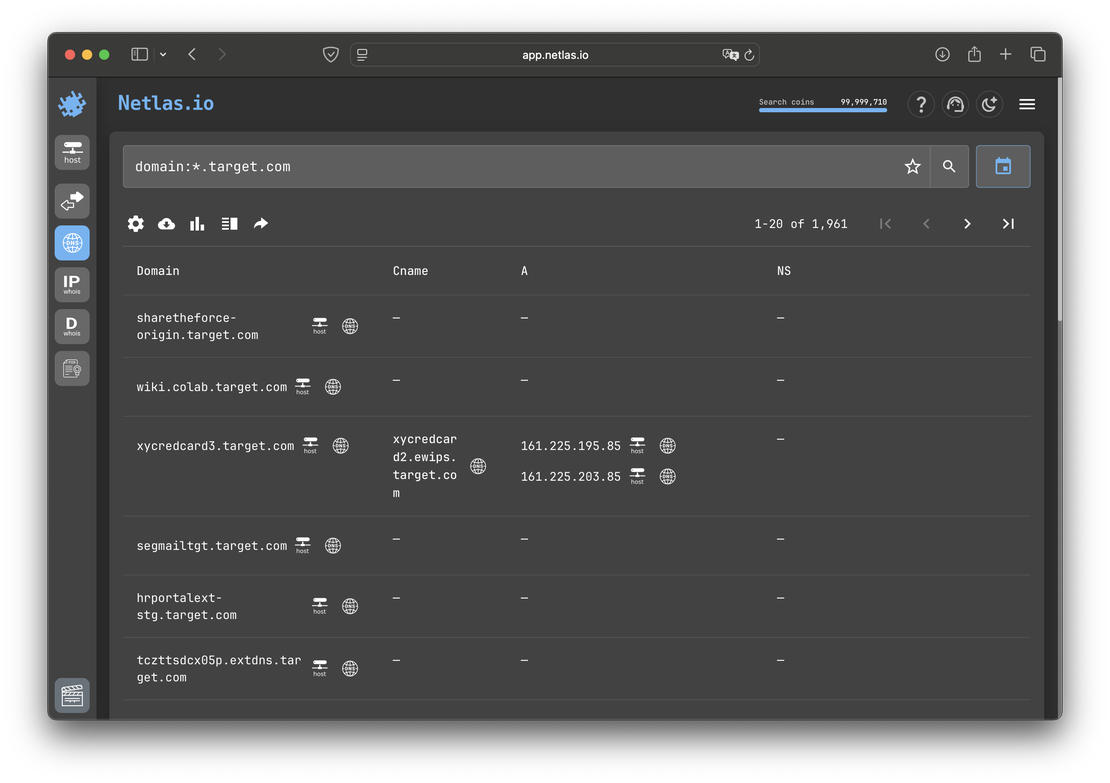
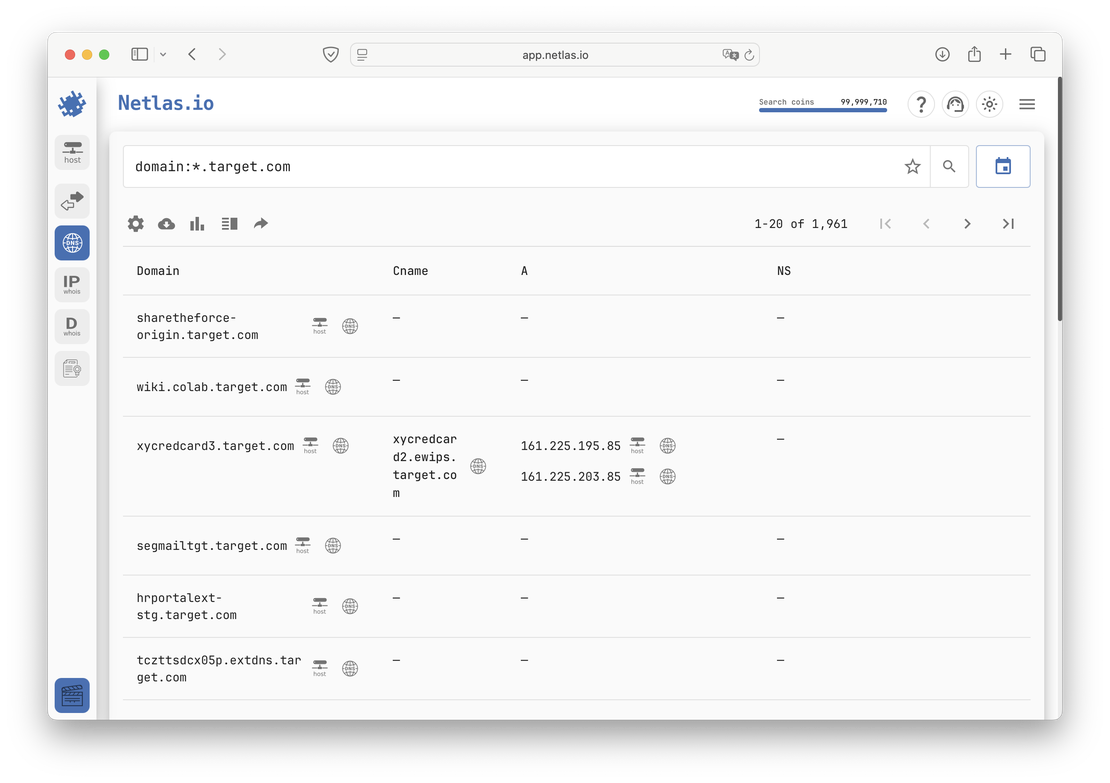
To explore subdomains in Netlas, you can also use the DNS Search tool. The request domain:*.target.com will return all subdomains of the corresponding site:
The Links tab displays all outbound links from the scanned site. In our example (target.com), no outgoing links were identified, and Netlas does not offer this capability. Consequently, we’ll move ahead to the Certs tab.
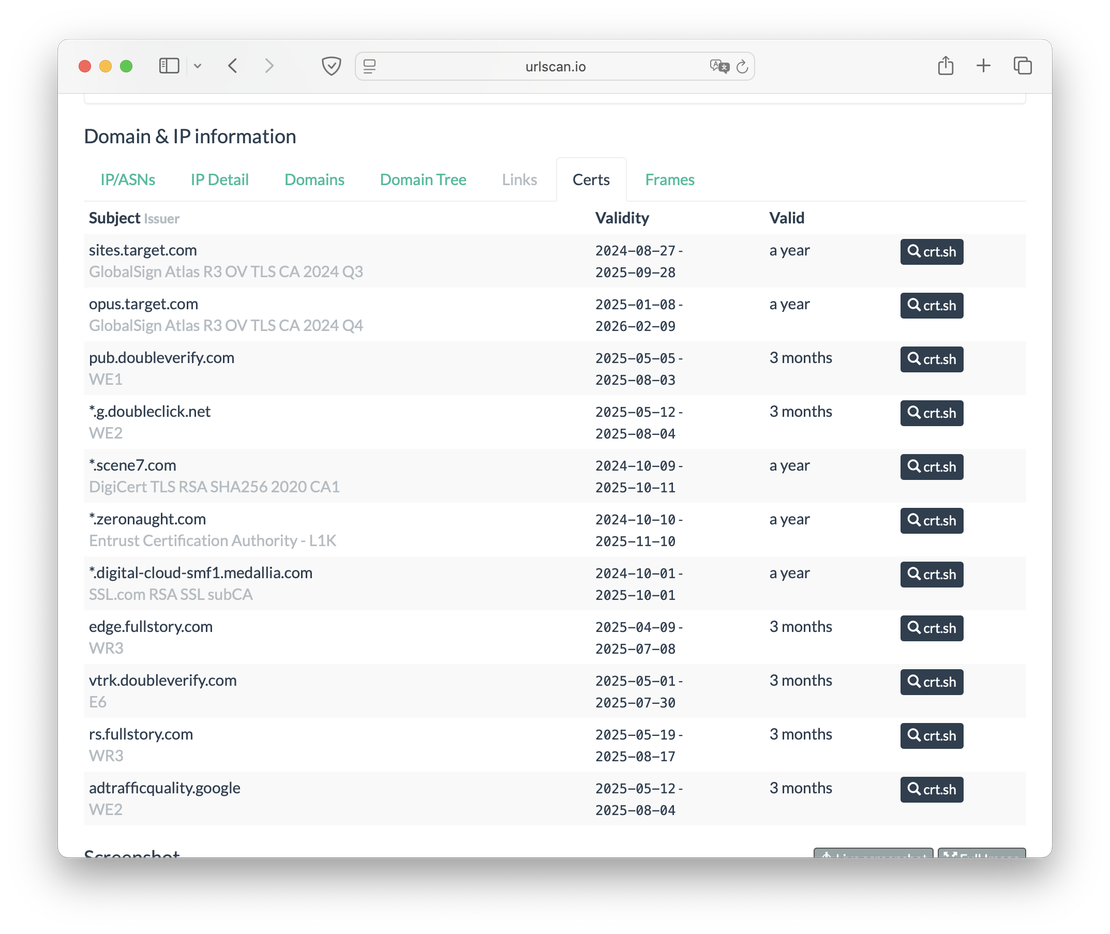
The Certs tab provides a list of SSL/TLS certificates issued for subdomains of the target site. Each entry includes the certificate’s issuer, its issuance date, and a link to crt.sh for detailed inspection.
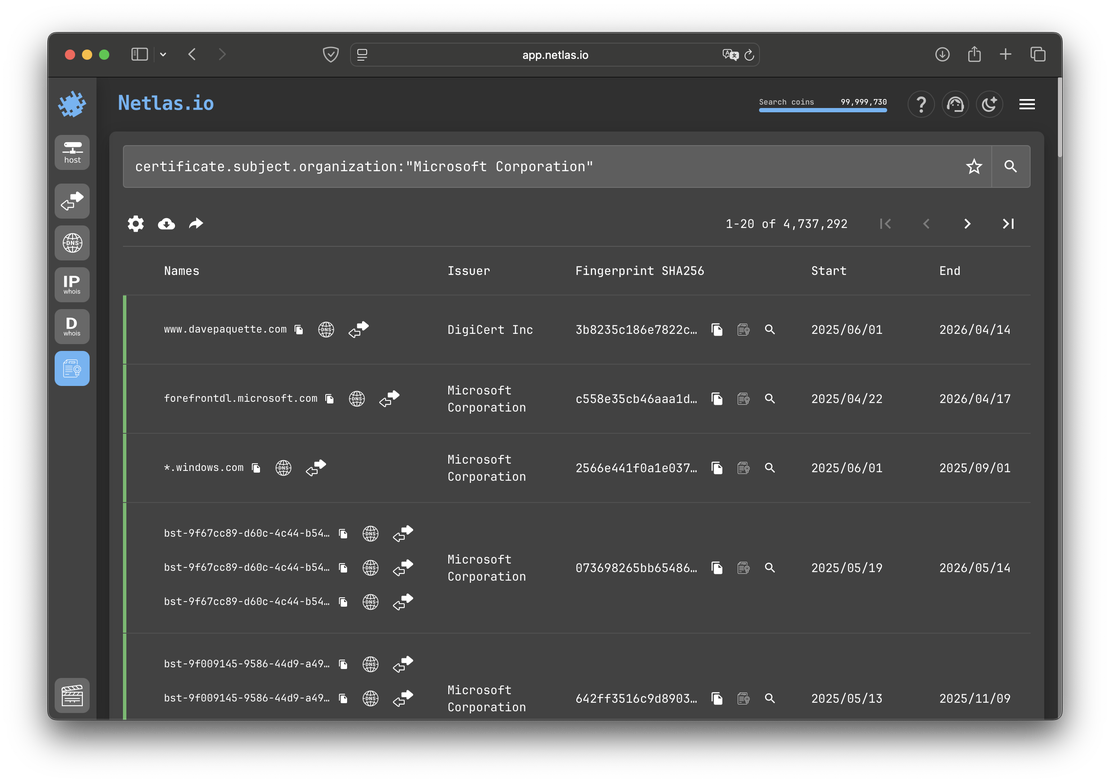
Netlas uses a separate tool for certificate research – Certificates Search. An example of its operation is shown in the figure below.
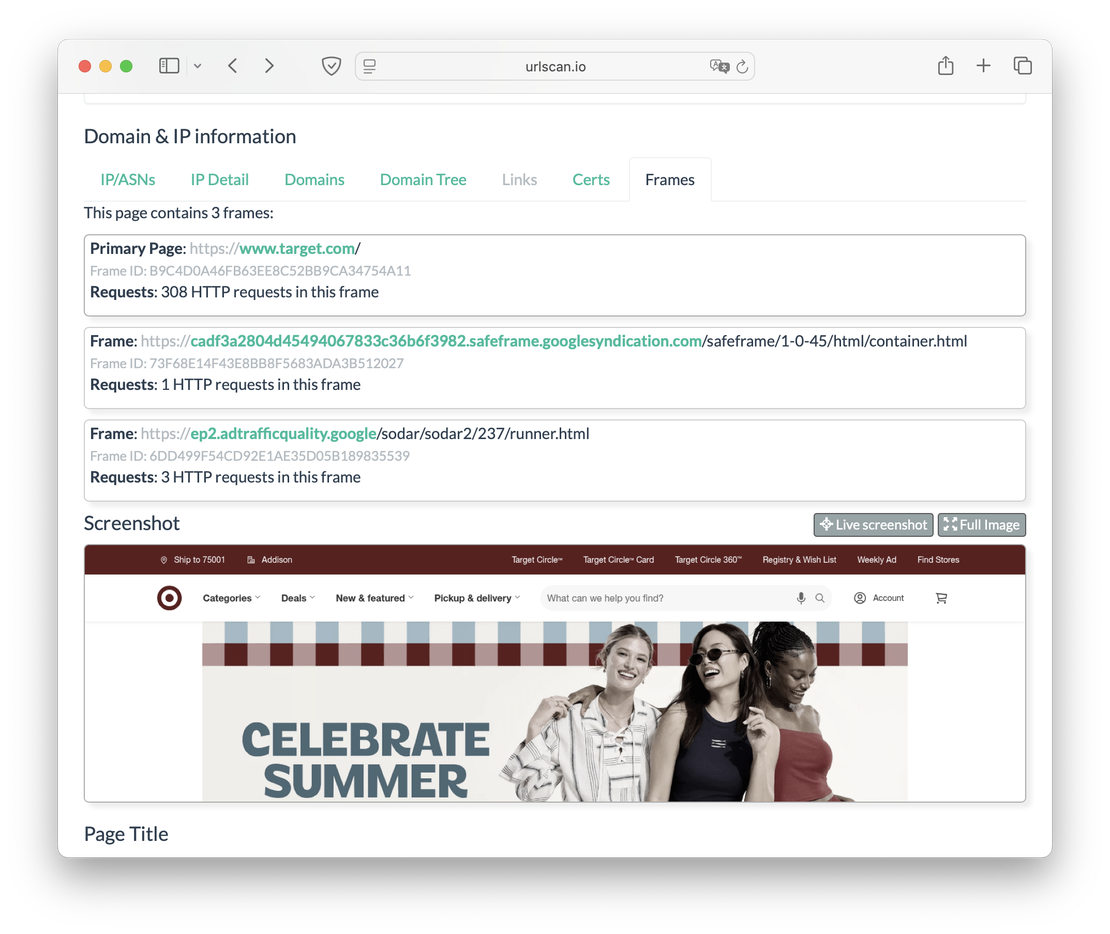
Finally, the last tab shows the frames of the domain being researched, as well as a screenshot from the main page.
HTTP Transactions
Accordingly, Urlscan can view transactions made by the dynamic content. There is a separate tab for this, the image of which is shown below.
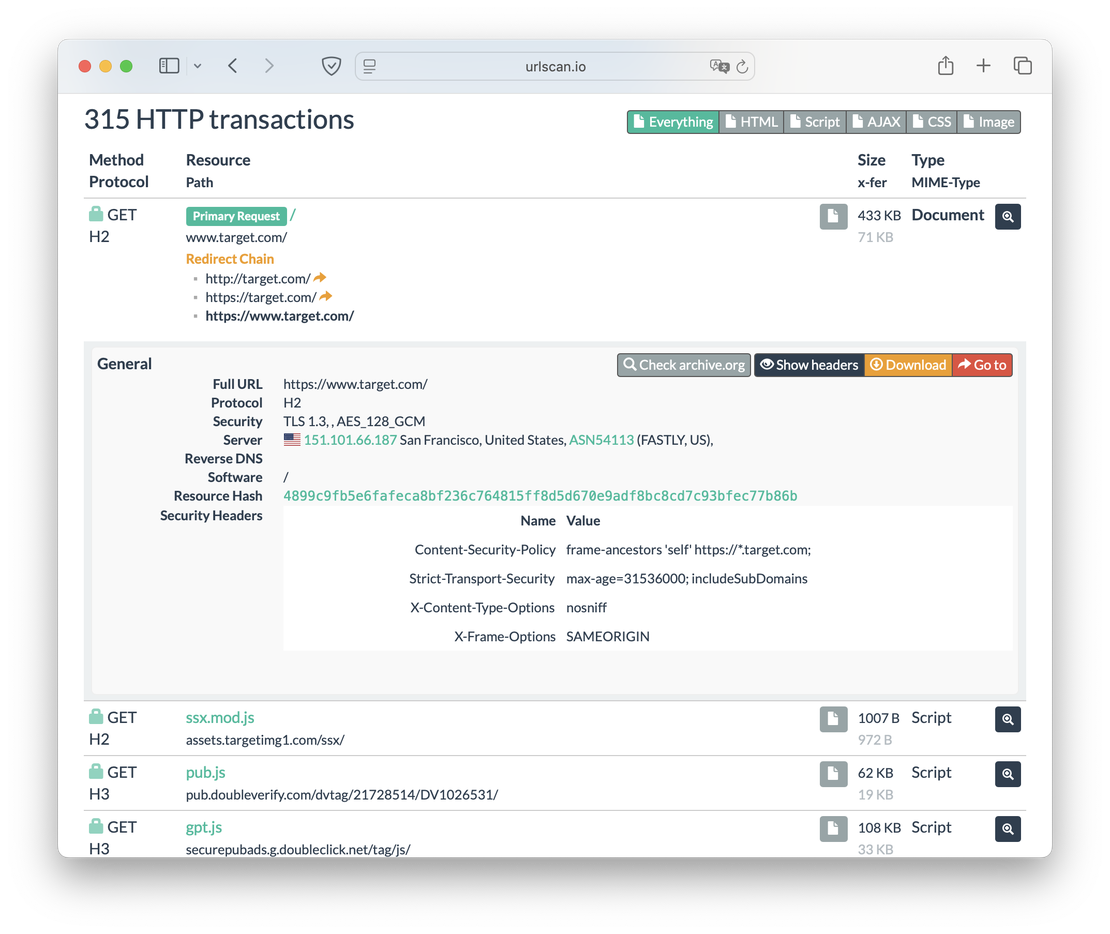
Here the user can view the scripts and documents that were loaded during the launch of the site.
Redirects
This tab shows the redirects that the sandbox encountered during the site analysis.
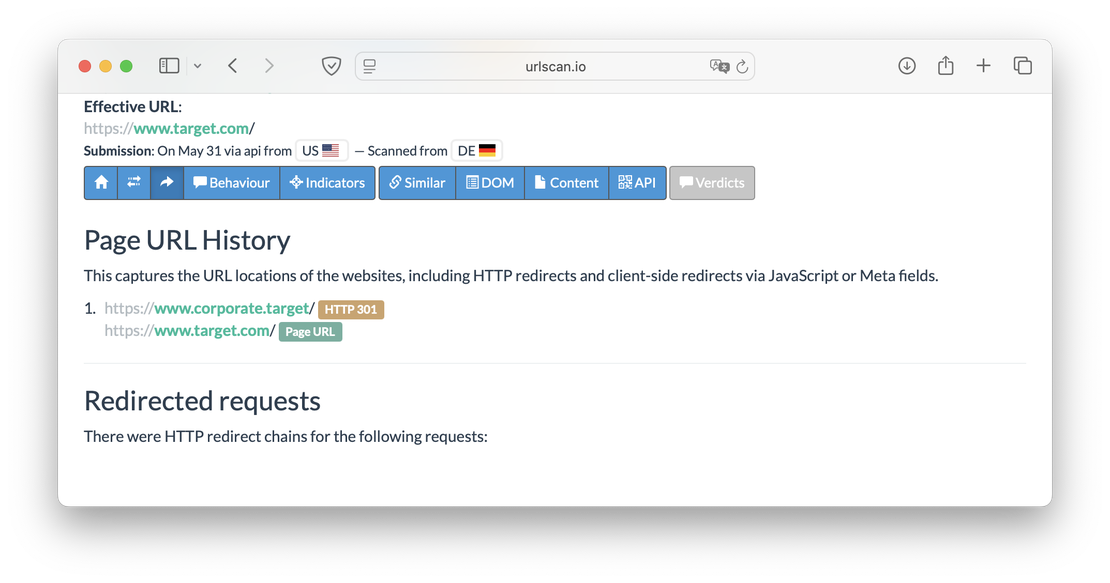
Netlas also provides information about redirects in the Responses Search tool.
Behaviour
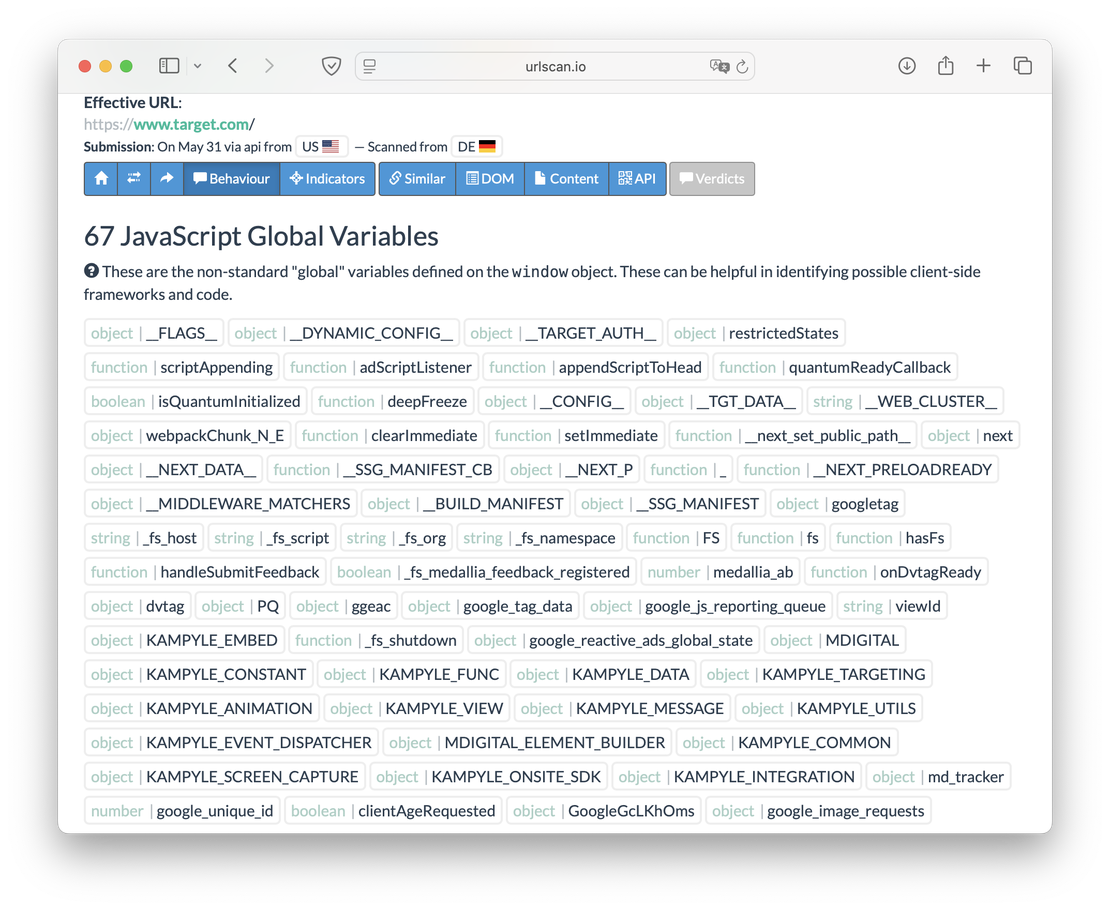
One of the most interesting tabs, it demonstrates the following aspects of the page:
- Non-standard JavaScript variables:
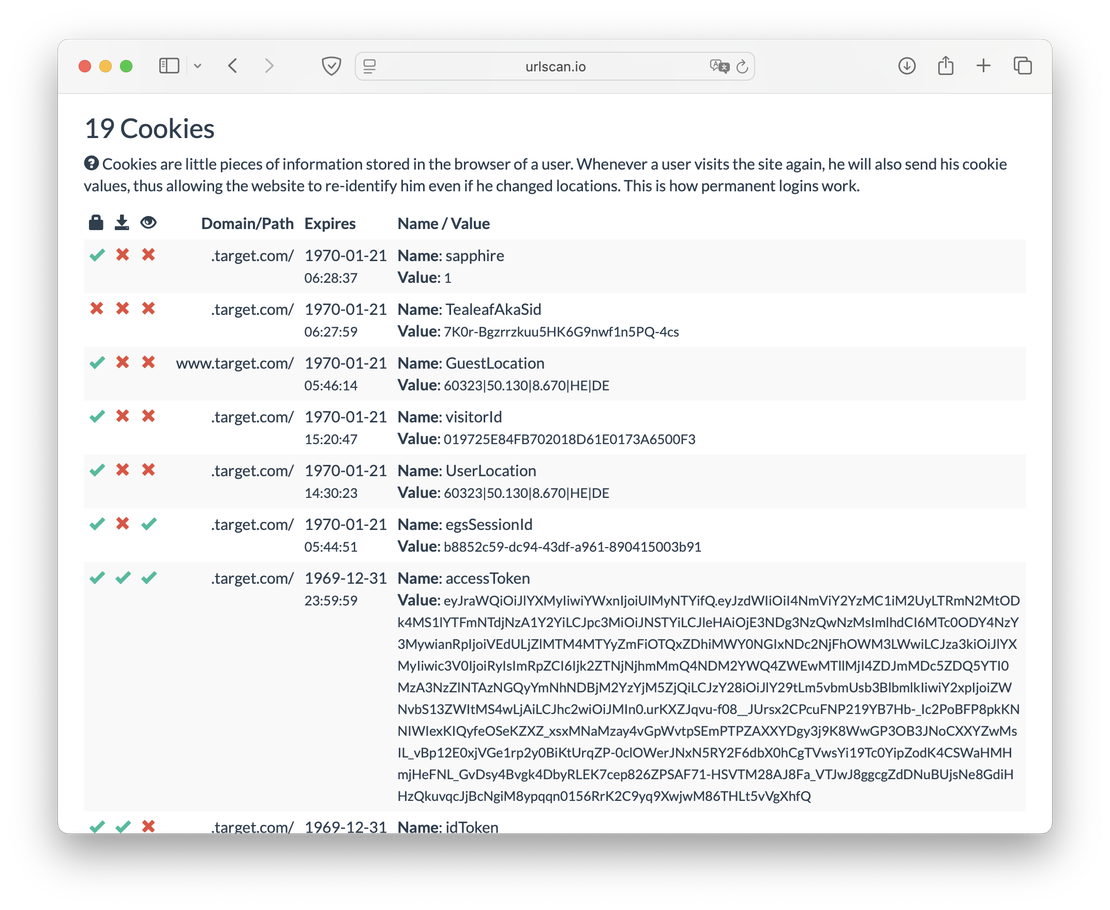
- Cookies:
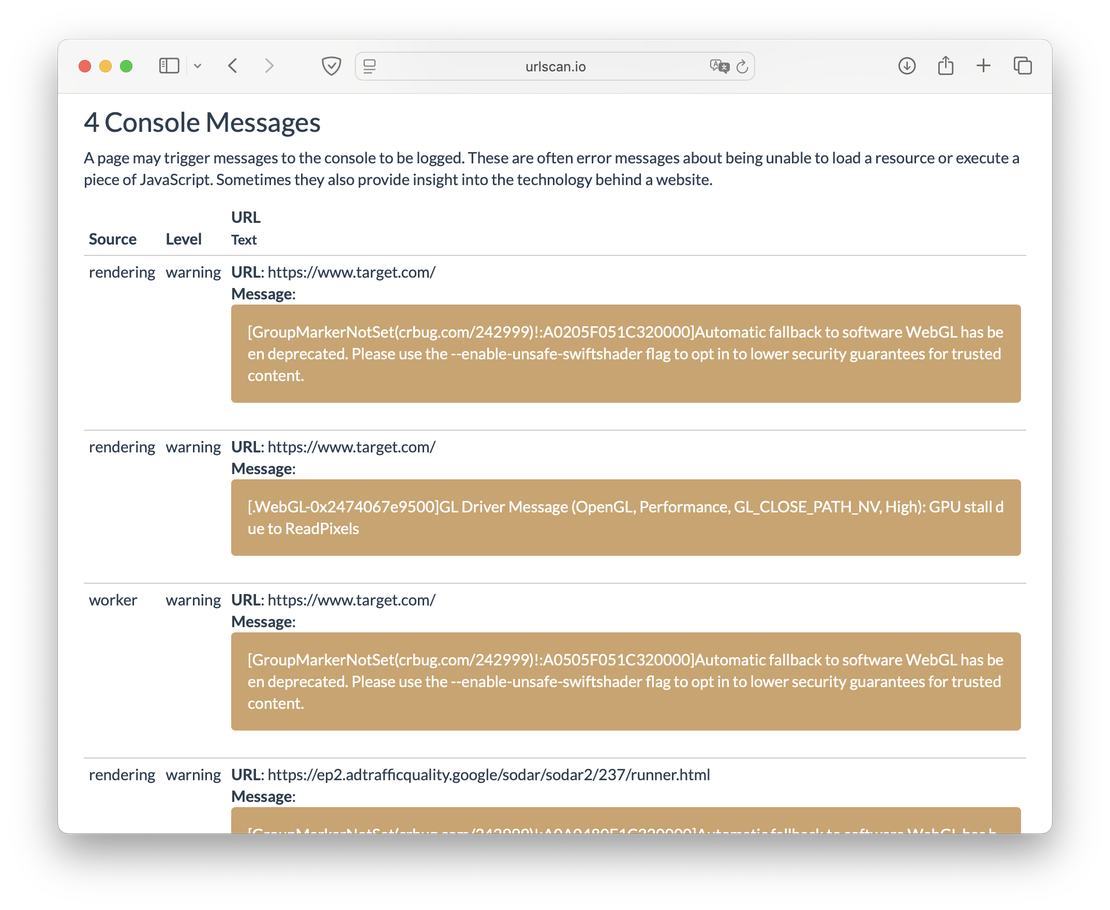
- Console Messages:
- Security Headers:
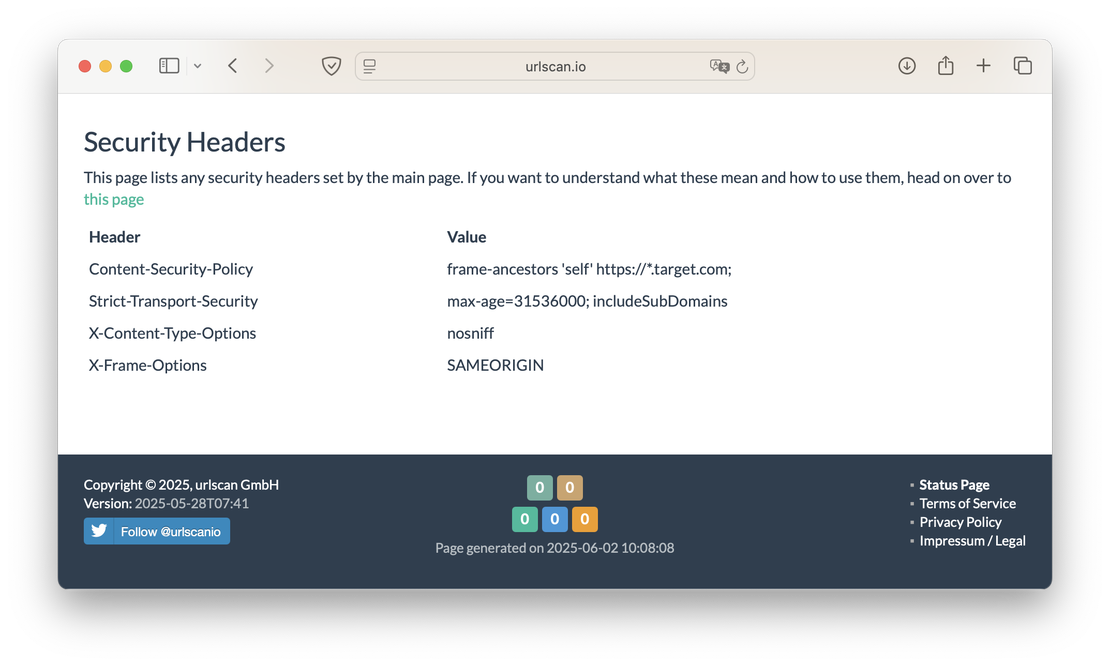
Much of the information described above can also be retrieved in Netlas via the Responses Search tool. For instance, HTTP headers and cookies appear under the http.headers section of each response, while form variables and other payload data are accessible in http.body. It’s important to remember, however, that Netlas crawlers do not fully render the site—any content generated dynamically at runtime will not be captured.
Indicators
The next tab shows indicators of the domain being investigated, allowing you to recognize resources associated with it.
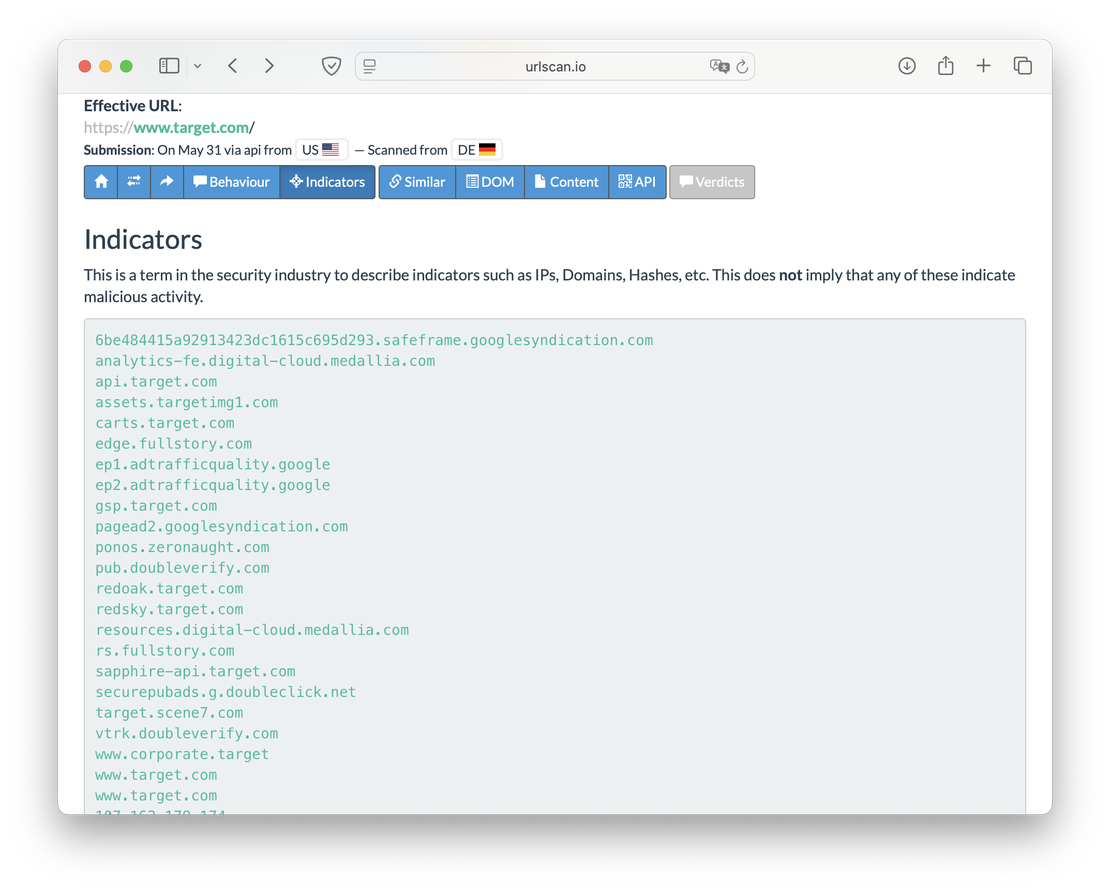
As for Netlas, it can be used to collect such indicators but does not provide a list of them.
Similar Resources
Then comes a tool that allows you to view the following types of resources:
- Identical structurally.
- Pages on the same domain.
- Pages on the same IP, but on a different domain.
- Pages in the same AS, but on a different IP.
An example is shown in the picture below.
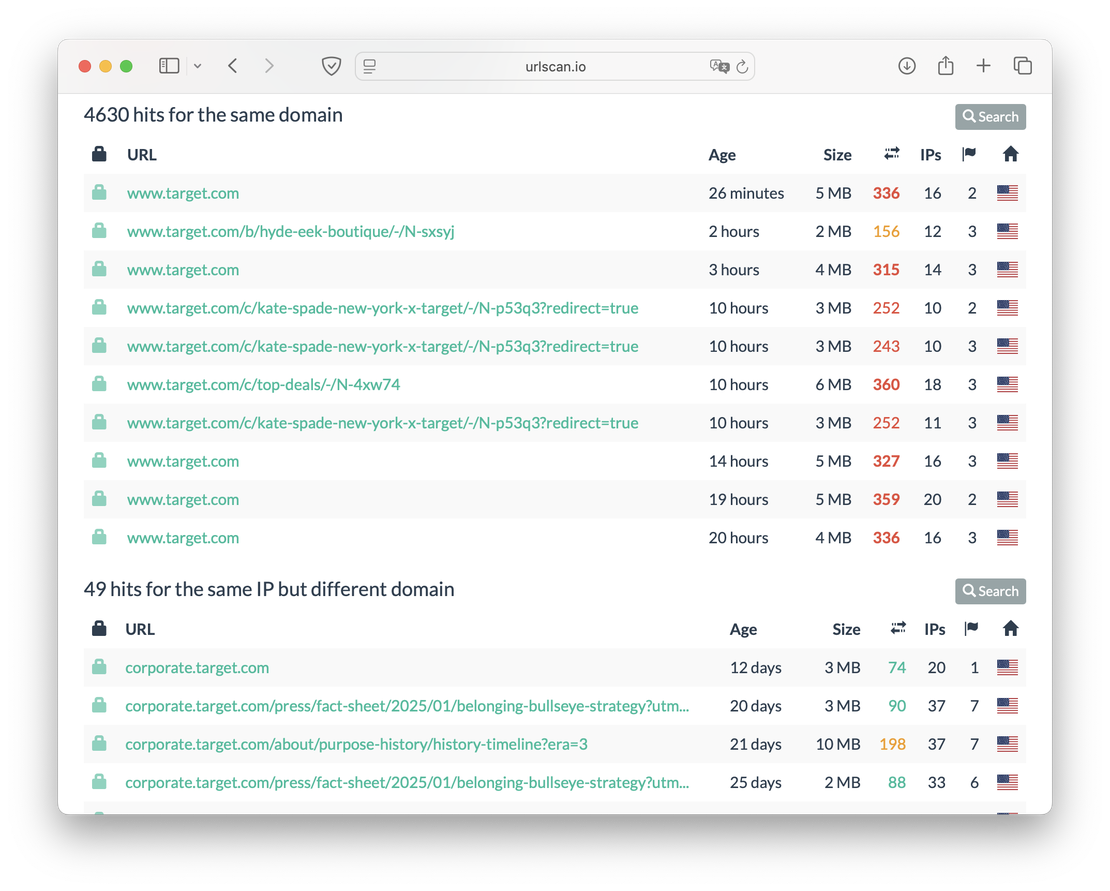
Netlas provides this data, but not in a structured way - users will have to process the received data themselves.
DOM Tree
Users can also view the Document Object Model tree:
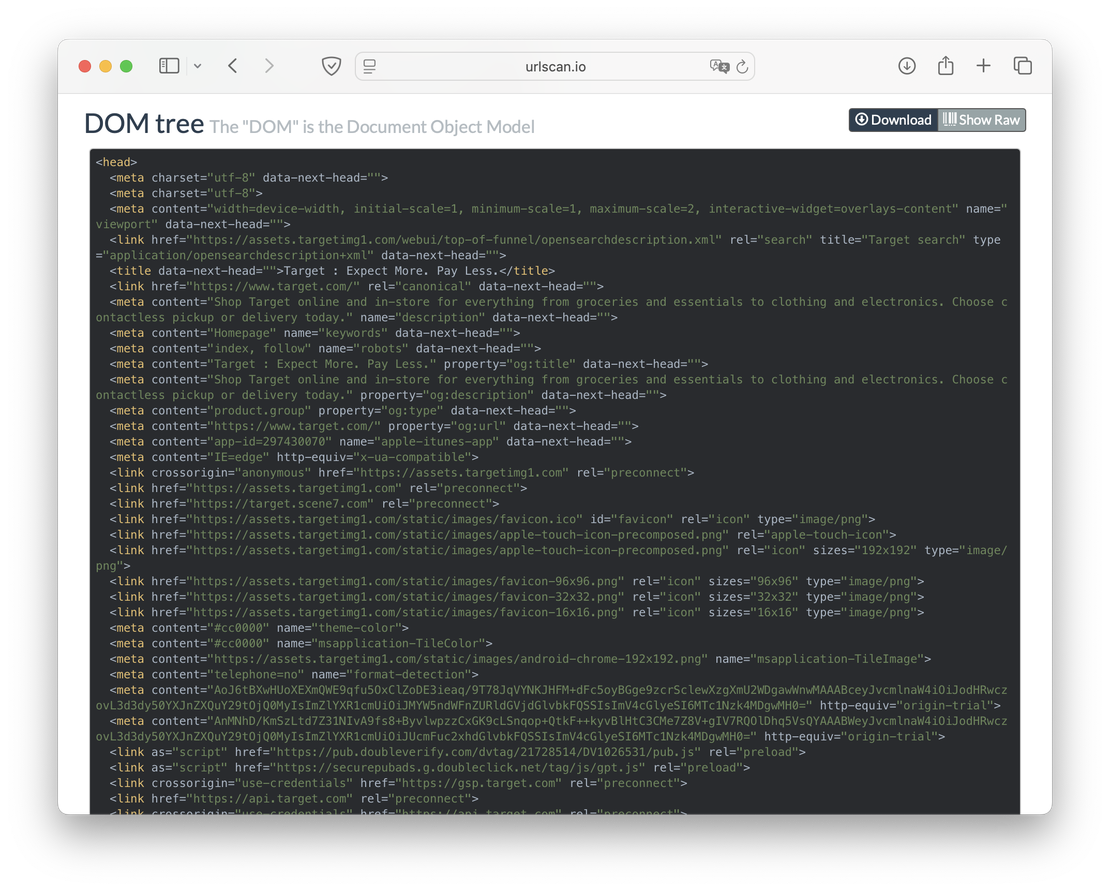
Since Netlas does not load the site completely, it cannot build a DOM tree.
Content
The last of the important tabs contains the text content that the parser received from the requested page. For example, it looks like this:
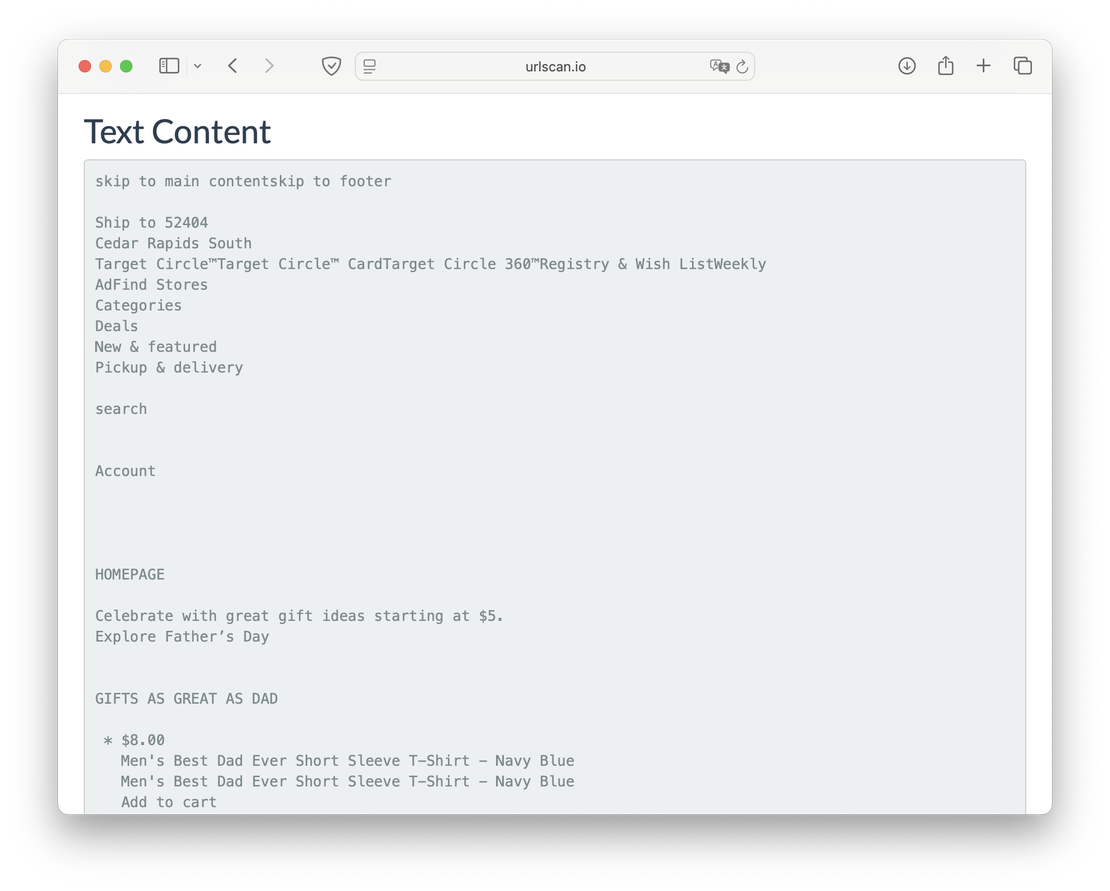
To get static content in Netlas, you need to use the Responses Search tool and access the http.body field.
Other Ways to Use
In the first half of this article, we examined both tools via their web interfaces. However, Netlas and Urlscan also support additional workflows and integrations. In the following section, we’ll explore these alternative use cases in greater detail.
API and CLI
The most straightforward approach is to interact with each service via its API. Detailed documentation for the Urlscan API is available here, while you can find Netlas’s API docs here. Below is an example illustrating a call to the Urlscan API:
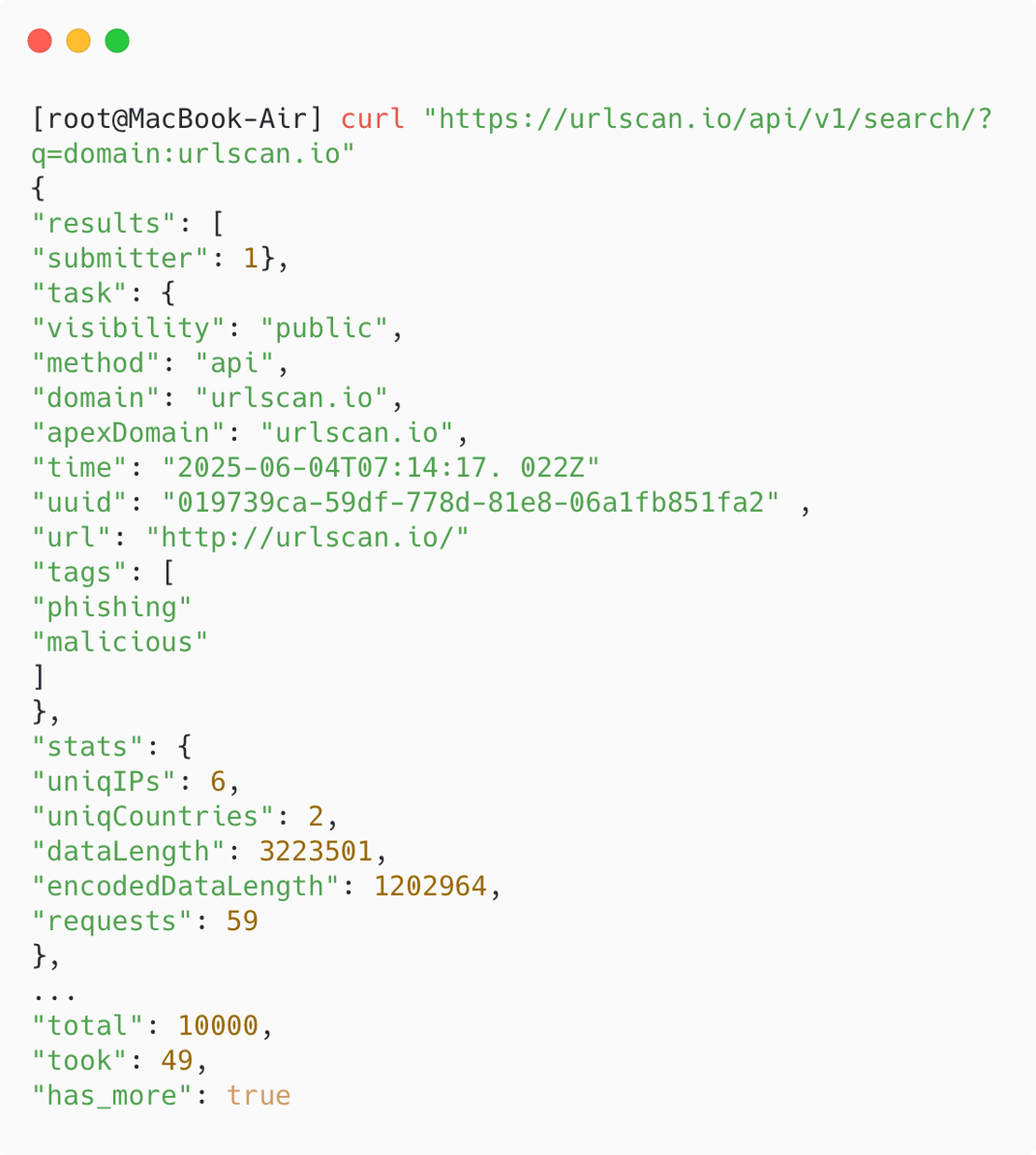
Due to the size of the API response, including it in full here isn’t practical. However, you can inspect the complete output in the web interface — each search result page features an API tab that displays the response for the target.
As for Netlas, the images below show an example of using the CLI utility.
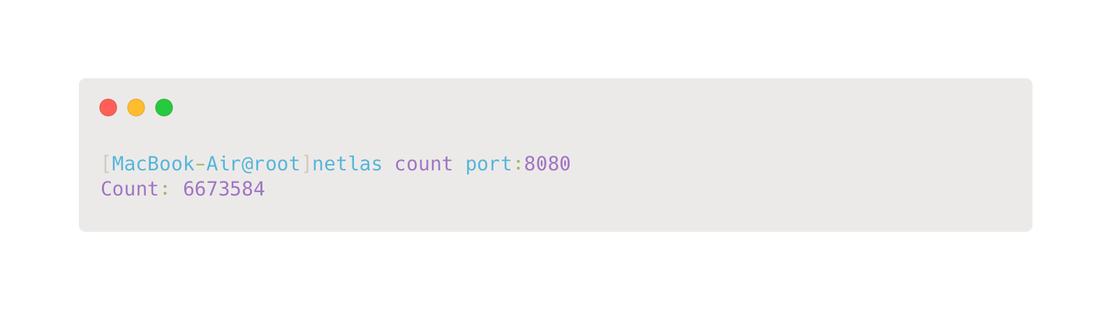
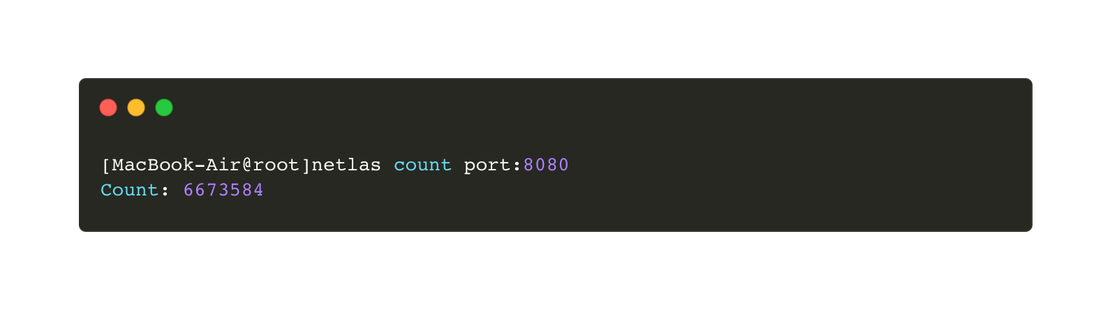
To install the utility, enter the following command:
pip install netlasIt’s simple!
Python Libraries
The next way to use tools automatically is libraries for the Python language.
The library for Urlscan has appeared quite recently. To install it, enter:
pip install urlscan-pythonNext in the script you need to create a client:
client = urlscan.Client("<your_api_key>")And then use it to start scanning:
res = client.scan("<url>", visibility="public")You can read more about the library in the official documentation.
As for Netlas, it also has a Python library. We already mentioned the command to install it:
pip install netlasAfter installing and importing the library, create a connection in the script:
netlas_connection = netlas.Netlas(api_key=apikey)Next, using the created object, contact Netlas directly:
netlas_query = netlas_connection.query(query="port:7001")Now all you must do is parse the result and extract the necessary data from it. You can find examples of scripts in our official GitHub.
Book Your Netlas Demo
Chat with our team to explore how the Netlas platform can support your security research and threat analysis.
Scanning Difference
As noted earlier, we’ve highlighted the differences between Netlas and Urlscan in terms of features and workflows. However, the most crucial distinction lies in their fundamentally different scanning methodologies.
To start, it’s important to understand that Urlscan primarily conducts on-demand scans. Although the service does automatically rescan certain flagged or high-risk sites — especially those suspected of malicious activity — to keep its dataset current, most scans are initiated by users. In contrast, Netlas employs a continuous, Internet-wide scanning model, querying responses across hundreds of ports. Netlas also provides an on-demand option through its Private Scanner tool, allowing users to update information for specific targets whenever needed.
Secondly, the underlying scanning mechanisms differ significantly. Urlscan spins up a full browser instance that mimics a real user’s session—executing scripts, loading dynamic content, and capturing generated headers and network traffic. Because each scan is initiated on demand and focused on a single target, the extra time required to render pages fully is acceptable and ensures comprehensive data collection.
By contrast, Netlas maintains a continuous, large-scale scanning infrastructure that covers hundreds of millions of domains. To optimize for speed and efficiency, our crawlers do not render web pages. Instead, they probe IP addresses and domains using tools like nmap, quickly gathering essential technical details. The trade-off is that dynamically generated content is not captured, but this approach allows us to deliver high volumes of actionable intelligence at scale.
Here, the fundamental distinction I highlighted at the outset becomes clear: these tools serve very different purposes and aren’t interchangeable. Netlas empowers users to access hundreds of millions of responses quickly delivering data on subnets, autonomous systems, and deployed technologies at scale. When performing penetration tests or investigating newly disclosed vulnerabilities, both volume and speed are paramount. In contrast, Urlscan dedicates more time to examining each individual site, providing comprehensive insights into a page’s content—including dynamically generated elements. This makes Urlscan especially valuable for tackling phishing threats or for refining intelligence gathered from other sources.
Summary
In this article, we compared Netlas and Urlscan across several dimensions—including their feature sets, methods of use, and scanning methodologies.
Obviously, these are very different tools. In situations where a mass and rapid assessment of basic aspects is needed, Netlas is more suitable. Urlscan can be used for a more in-depth study of a single service. In any case, they are not interchangeable and can show their best results when working together.
Related Posts

May 20, 2025
Netlas vs IPinfo: Tools Comparison

March 21, 2025
Netlas vs ZoomEye: Platforms Comparison

February 12, 2025
Netlas vs Censys: Platforms Comparison

December 18, 2024
Netlas vs Fofa: Platforms Comparison

November 21, 2024
Netlas vs Shodan: Platforms Comparison

July 13, 2024
Best Attack Surface Visualization Tools
















