Best Nmap Alternatives
June 18, 2025
17 min read
Working with a terminal on Unix or Linux can feel like mastering a manual transmission in a car—there’s a sense of complete control, with the ability to harness its full capabilities. However, for some, this experience might seem too complex and time-consuming. These individuals lean toward simpler, more intuitive tools that handle the technical details for them.
The same divide exists in the digital world. Some users enjoy the raw power of the terminal, while others prefer web-based and graphical interfaces that provide efficient, no-fuss solutions to their needs.
This blog takes a balanced approach, covering both sides: detailed guides focused on terminal-based tasks, as well as reviews of user-friendly web-based tools. In today’s post, we’re continuing our focus on web-based alternatives, showcasing some of the best Nmap online substitutes to the traditional command-line method.
Discover the Best Nmap Alternatives
When exploring online alternatives to Nmap, one limitation you’ll encounter is the inability to easily execute Nmap scripts, as you would with the terminal version. Web-based scanners are generally restricted to the scanning features offered by their developers, and you might not have the same level of flexibility as with Nmap on the command line.
However, these online alternatives typically focus on scanning the most commonly targeted ports. If you’re seeking a straightforward scan without requiring extensive customization, these platforms can serve your needs quite effectively.
In this guide, we will first cover the simplest options suitable for casual users, and then explore more sophisticated alternatives that not only provide port scan results but also integrate additional cybersecurity insights.
A common disclaimer across many of these services is that scans should be conducted as part of a defensive strategy, primarily to check for open ports within your own network. Many platforms impose restrictions, such as limiting the number of scans from a single IP, to prevent misuse of the service for scanning external or third-party networks.
Masscan: The Blazing Fast One
Masscan is an asynchronous, event‑driven port scanner capable of surveying the entire IPv4 address space in mere minutes. It’s designed for situations where raw speed is paramount and you need to discover open ports across vast network ranges.
Project Details:
Masscan implements its own TCP/IP stack and uses an efficient event loop to send and receive packets at extremely high rates. It can scan up to tens of millions of packets per second (depending on your hardware and network), making it ideal for large‑scale internet surveys. Output formats are compatible with Nmap (XML) and Grepable, allowing easy integration with existing workflows.
Strengths:
- Unmatched Speed: Able to scan the entire public IPv4 address space in under six minutes on commodity hardware.
- Lightweight & Single‑Executable: Written in C, Masscan is distributed as a single binary with no external dependencies.
- Flexible Timing Controls: Fine‑tune packet send rates, timeouts, and retries to match available bandwidth and avoid tripping intrusion detection systems.
- Nmap‑Compatible Output: Export results in Nmap XML format, facilitating downstream analysis with your existing toolchain.
Weaknesses:
- Higher False‑Positive Rate: At extreme speeds, packet loss can lead to misreported open ports unless you throttle the scan rate appropriately.
- Steeper Learning Curve for Advanced Tuning: Mastery of its many rate‑control parameters is required to optimize for both speed and accuracy.
Typical Usage:
Masscan is favored by security researchers and large‑scale monitoring projects that need an initial map of open ports across vast address ranges. It’s often used as a “first pass” before feeding discovered targets into more detailed scanners like Nmap or Nessus.
License Model:
Released under the BSD license, Masscan is completely open‑source and free for both commercial and non‑commercial use. Its permissive licensing makes it easy to embed in proprietary toolchains.
Platforms:
Masscan runs on Linux, macOS, and Windows (via Cygwin). It requires raw socket or libpcap privileges, so scans are typically executed with root/administrator permissions.
Usage Example:
root@MacBook-Air ~ % sudo masscan -p80,8000-8100 x.x.x.x/30 --rate=10000
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2025-06-17 10:24:22 GMT
Initiating SYN Stealth Scan
Scanning 4 hosts [102 ports/host]
Discovered open port 8000/tcp on x.x.x.x
Discovered open port 8001/tcp on x.x.x.x
Discovered open port 8002/tcp on x.x.x.x In this scenario, the scan targeted ports
Nmap.online: The Cloudy One
Nmap.online offers a streamlined, browser-based version of the popular Nmap tool, bringing network scanning capabilities directly to your fingertips without the need for local installation. Designed for users who need quick and accessible network analysis, Nmap.online is an invaluable tool for anyone needing to assess open ports, services, and potential vulnerabilities on their network from any device with an internet connection.
Project Details:
Nmap.online is a web-based service that uses the Nmap scanning engine, one of the most trusted tools in network security. It allows users to perform a variety of network scanning tasks such as identifying open ports, checking service versions, and assessing vulnerabilities. The platform provides a user-friendly interface that simplifies complex Nmap commands and presents results in an easy-to-read format. This online service is ideal for users who want the power of Nmap without the technical requirements of running it locally.
Recommended Reading
Nmap Cheat Sheet: Top 10 Scan Techiques
Strengths:
- Ease of Access: Being a web-based solution, Nmap.online can be accessed from any modern browser, removing the need for software installations or complex setup processes.
- User-Friendly Interface: Unlike the traditional command-line Nmap, Nmap.online offers a clean and simple graphical interface, making it easy for users of all technical backgrounds to perform network scans.
- Quick Results: The platform allows users to receive scan results in real-time, providing fast insights into network configurations and security status.
- Comprehensive Scan Options: Nmap.online provides a wide array of scanning capabilities, including the detection of open ports, service versions, and protocol information, making it a robust tool for network monitoring.
Weaknesses:
- Limited Customization: While Nmap.online covers most basic and intermediate scanning needs, it lacks the flexibility and depth offered by the full, terminal-based Nmap tool, especially for more advanced use cases.
- Privacy Concerns: As a cloud-based service, there may be concerns regarding the privacy and security of data being scanned and transmitted over the internet.
- Scan Limits: Free access to Nmap.online may come with restrictions on the number of scans or the size of the networks you can analyze, with some advanced features locked behind a paywall.
Typical Usage:
Nmap.online is typically used by IT professionals, network administrators, and security experts who need quick, remote access to network scanning tools. It’s also favored by those who need to perform regular vulnerability assessments or network audits but do not want the hassle of managing local scanning software. The tool is suitable for smaller businesses or individual users who need to verify open ports, monitor network security, and troubleshoot connectivity issues.
License Model:
Nmap.online offers a freemium model. The basic version provides essential scanning features at no cost, with limitations on scan volume and access to certain advanced functions. For users who require more extensive scanning options, detailed reports, and higher limits, premium subscriptions are available, offering additional features and higher performance.
Platforms:
Being a cloud-based solution, Nmap.online is accessible through any modern web browser on major platforms, including Windows, macOS, and Linux. This ensures flexibility for users on various devices and operating systems, allowing network scans to be performed on-the-go from desktops, laptops, or even mobile devices, as long as there is an internet connection.
Usage Example:
The following image shows the main page of the application.
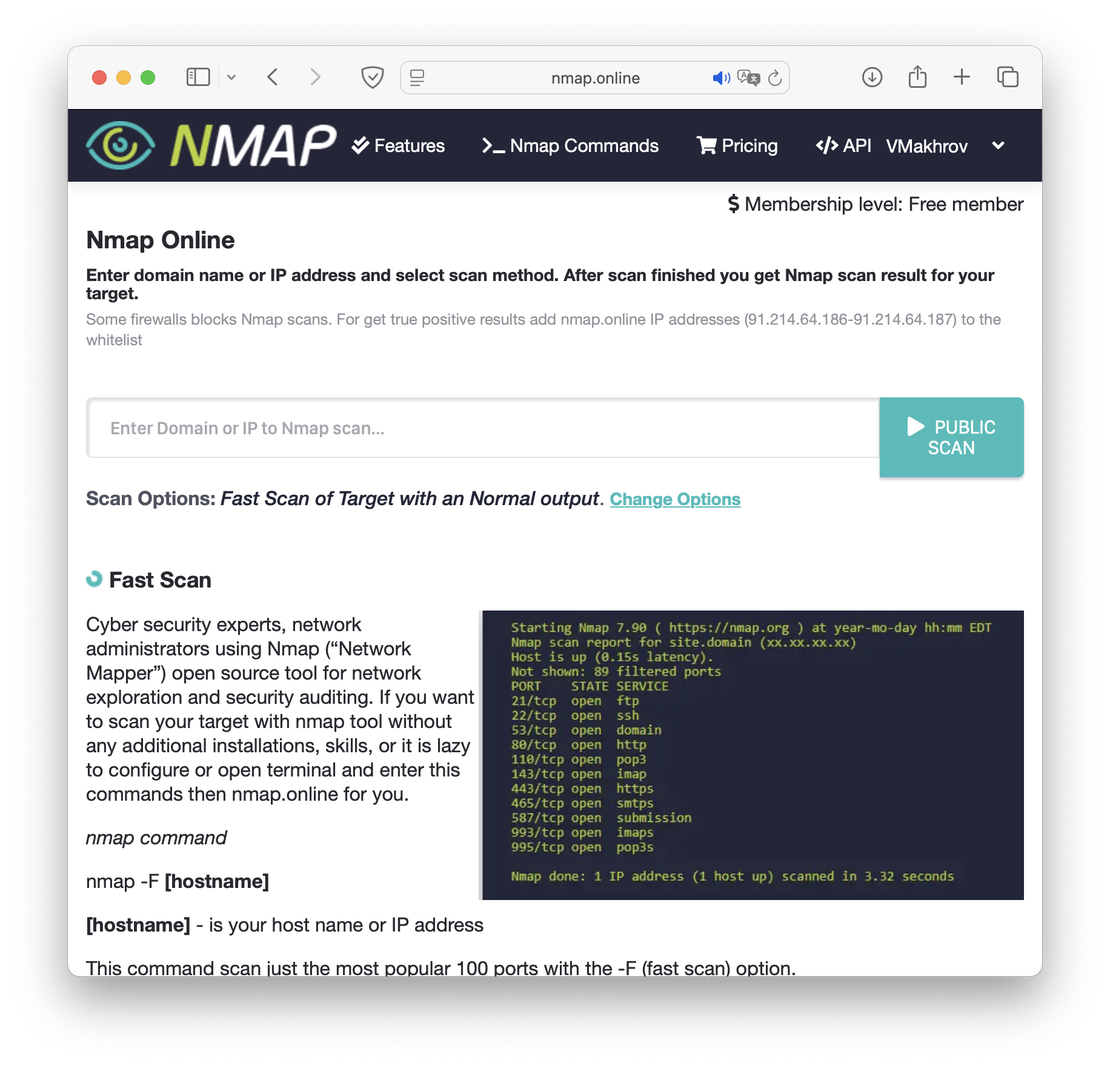
To kick off a scan, just enter your target into the search bar. Keep in mind that free‑tier accounts can’t run private scans—any results you generate will be publicly visible.
The scan results will look something like this:
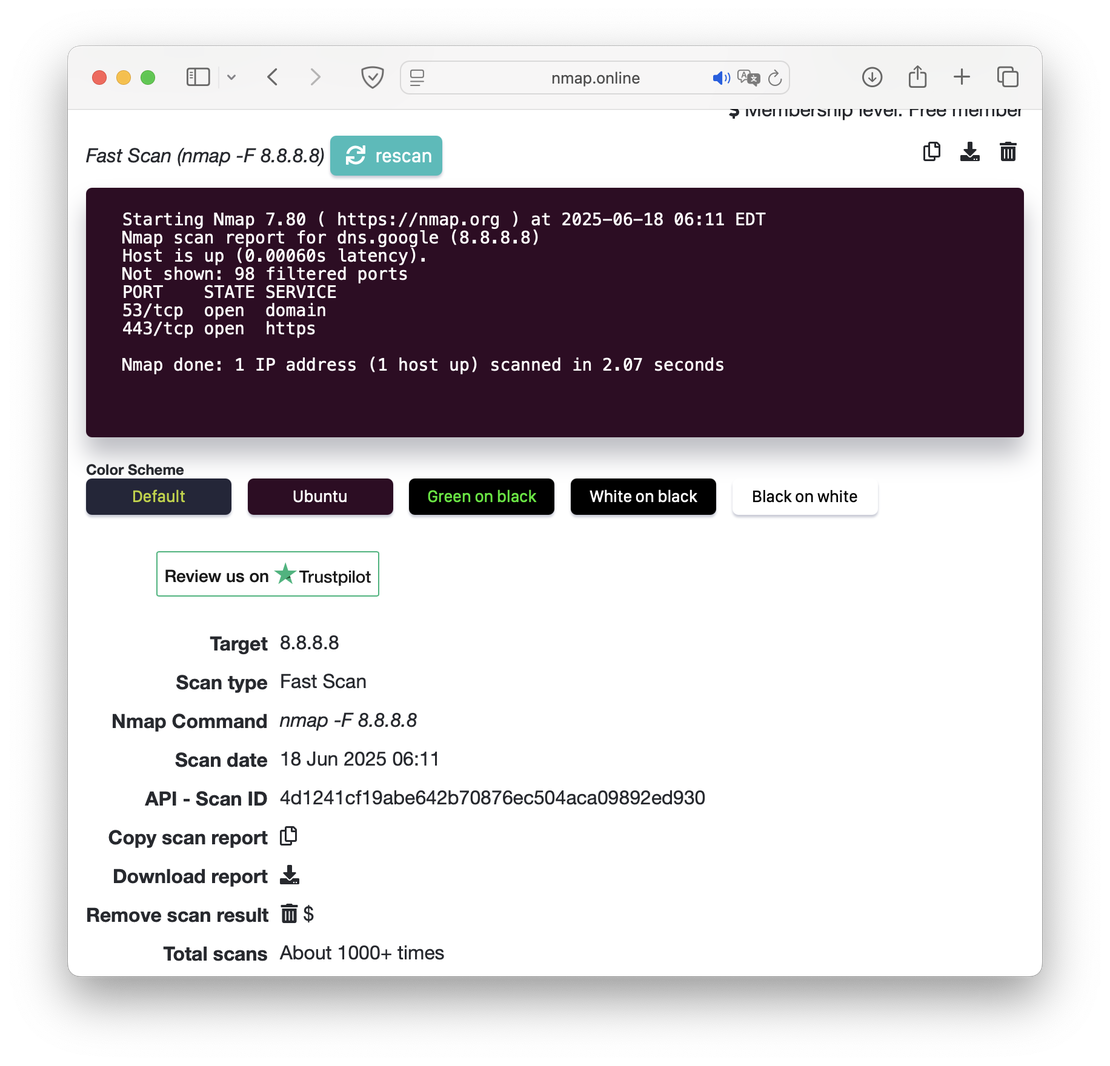
Netlas.io: The Stealthy Passive One
Netlas is a cutting-edge search and analysis engine designed to support cybersecurity investigations, threat intelligence, and attack surface management. Unlike traditional tools that require manual data gathering and scripting, Netlas aggregates and structures massive volumes of internet-wide scan data, DNS records, domain metadata, and digital certificates, enabling users to instantly access actionable insights with simple queries. It’s a powerful resource for analysts, researchers, and defenders seeking to uncover exposed assets, detect malicious infrastructure, and understand digital footprints.
Project Details:
Netlas continuously collects and indexes public data from internet scans, DNS zone transfers, WHOIS records, certificates, and passive DNS sources. It allows users to explore this data through a robust search interface or via its powerful REST API. Netlas enables detailed queries with fine-grained filters for assets like IP addresses, domains, open services, SSL certificates, and even screenshots of remote desktops. The platform also supports real-time analysis and provides tools to manage attack surfaces, discover shadow IT, and monitor adversary infrastructure.
Recommended Reading
Whois History: How to Check the Domain Owner History
Strengths:
- Multi-Source Intelligence Fusion: Netlas brings together data from various sources—such as internet scans, DNS, WHOIS, and SSL/TLS certificates—into one searchable platform.
- Search First, Scan Later: Instead of launching new scans, users can instantly query existing global data. For custom needs, Netlas provides a Private Scanner for tailored, on-demand scans.
- Fuzzy and Flexible Queries: The query language supports wildcards, range searches, regex, and fuzzy logic, making it ideal for catching typosquatting domains, phishing infrastructure, or exposed assets.
- Data Enrichment and Context: Beyond raw scan results, Netlas provides enriched metadata, such as threat tags, geolocation, ASN info, and screenshots, helping analysts prioritize threats faster.
- User-Friendly CLI and SDK: With an official Python SDK and CLI tool, users can automate tasks, fetch scan data, and integrate Netlas into their own pipelines or SIEMs.
Weaknesses:
- Relatively Young Dataset: Compared to longer-established platforms, Netlas has less historical depth, especially for archived data like DNS records.
- No Internal Network Scanning: Netlas focuses on internet-facing assets; it does not offer capabilities for scanning internal or private networks.
- Requires Understanding of Query Syntax: While the UI is intuitive, getting the most out of Netlas often requires some familiarity with its query language and data schema.
Typical Usage:
Netlas is widely used by threat hunters, SOC teams, MSSPs, and OSINT investigators. It supports a range of tasks, including domain investigations, phishing site detection, attack surface discovery, incident response, and infrastructure attribution. It’s particularly valuable in fast-paced investigations where time and precision are critical, such as tracking malware C2 infrastructure or identifying vulnerable assets.
License Model:
Netlas follows a freemium model. Users can create a free account to run limited searches and explore basic data. Paid plans unlock broader access to historical records, API usage, custom scanning, and team collaboration features. Business and Enterprise tiers cater to teams and large-scale workflows.
Platforms:
Netlas is accessible via any modern web browser and supports cross-platform usage on Windows, macOS, and Linux. For automation and integrations, it offers a comprehensive REST API, Python SDK, and CLI utility. This enables seamless inclusion in custom tools, scripts, or cybersecurity platforms. Team features and scan-sharing options make it collaboration-friendly for security departments and MSSPs.
Usage Example:
In the context of this article, it is worth mentioning two Netlas tools: Responses Search and Private Scanner.
The first allows the user to search for already prepared scans. The advantage of this approach is its passivity, due to which the user does not need to worry about the legality of their actions and the risk of being blocked. The disadvantage is the age of the data, since some responses may be outdated.
The image below shows a request for responses running on port 8000.
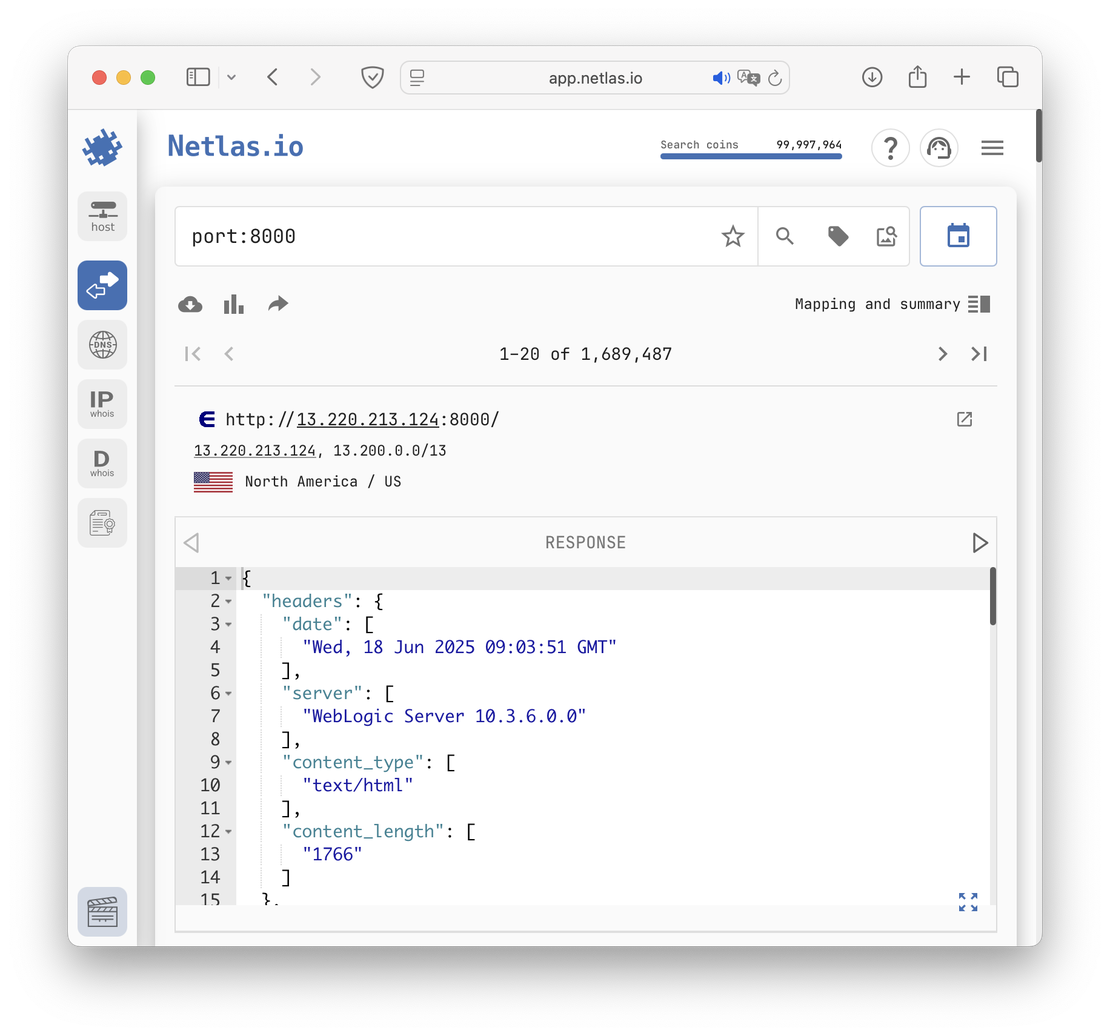
As for Private Scanner, it is more like an analogue of Nmap in the usual sense. This tool accepts IP addresses and domain names as input, and then scans them using a pool of ports, which can be found in the documentation. After the scan is completed, the user will have access to a private index, which will contain the most up-to-date data.
The following image shows an example of Private Scanner interface.
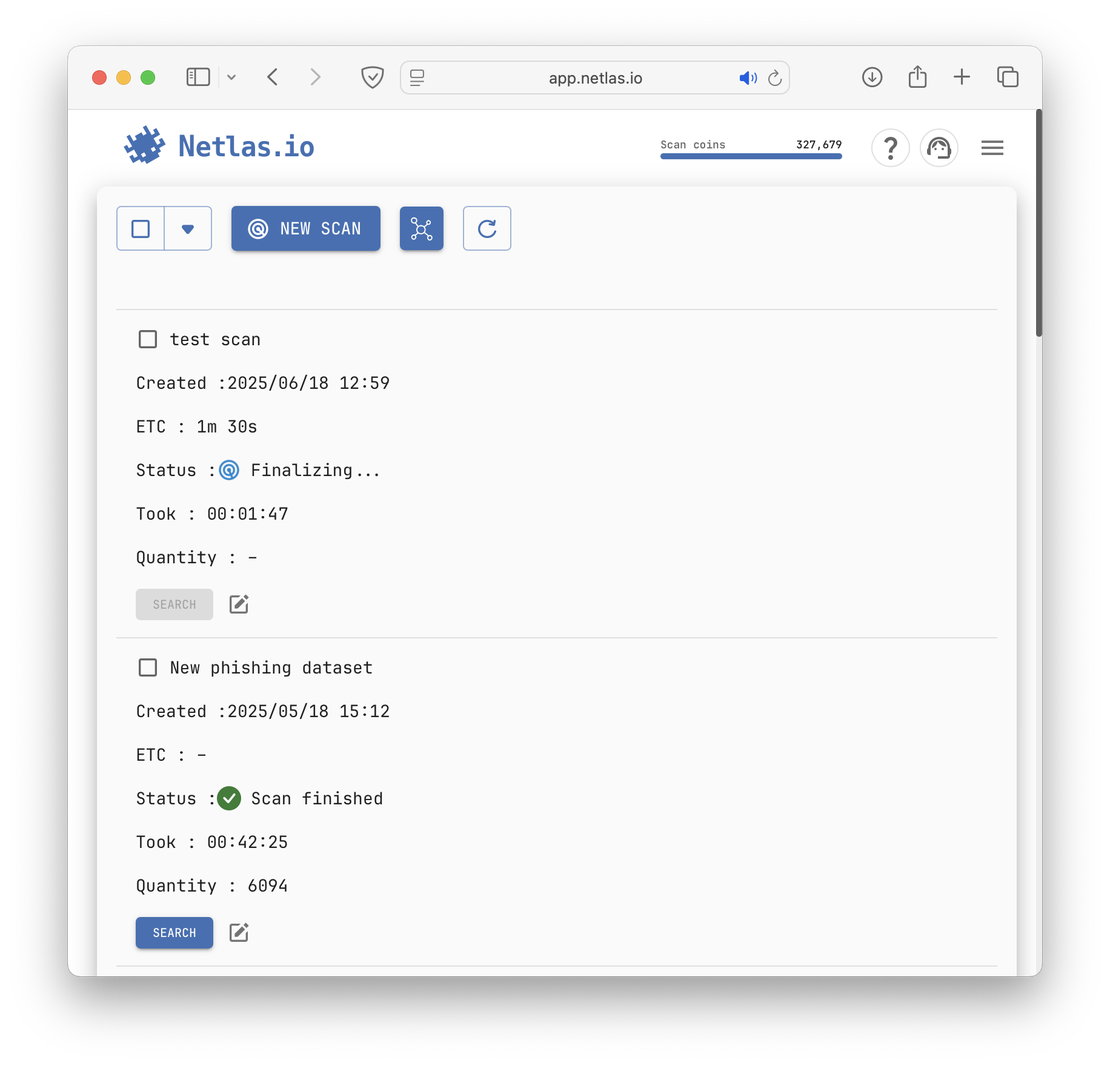
Shodan: The Veteran Spy One
Shodan is one of the most well-known and powerful network scanning tools available today, widely recognized for its ability to search and map the internet by identifying devices connected to it. As a comprehensive alternative to traditional network scanning tools, Shodan focuses on providing detailed insights into publicly accessible systems, helping users identify potential vulnerabilities and security risks across global networks.
Request Your Free 14-Day Trial
Submit a request to try Netlas free for 14 days with full access to all features.
Project Details: Shodan operates as a search engine for the Internet of Things (IoT) and connected devices. Unlike standard network scanners that only identify devices within a specific network, Shodan scans the entire internet, indexing devices and systems based on various criteria, including open ports, services, and vulnerabilities. It provides users with a web interface where they can search for devices by type, location, software, and more. The service also offers advanced filtering options and alerts, making it a go-to tool for cybersecurity professionals and researchers.
Strengths:
- Internet-Wide Coverage: Shodan is capable of exploring devices openly accessible across the internet, rather than being confined to local networks.
- Extensive Information Gathering: It compiles key data about each system, such as IP details, operating services, and possible security flaws, making it highly beneficial for auditing and monitoring.
- Straightforward Web Interface: Despite its high-powered functionality, Shodan’s site is designed for ease of use, accommodating both beginners and advanced users who want to run in-depth scans.
- Versatile Query Options: Shodan supports a variety of search filters and parameters, enabling users to tailor searches based on specific types of systems or particular weaknesses.
Weaknesses:
- Not Suitable for Internal Networks: Because Shodan targets devices visible on the public internet, it isn’t intended for private or internal systems unless those are externally reachable.
- Potential Exposure of Sensitive Data: By scanning publicly available devices, Shodan may uncover information that was never meant to be publicly displayed, which raises concerns about data privacy.
- Advanced Tools Require Payment: While there is a free tier, unlocking the full suite of features—including expanded data and in-depth scanning—requires a subscription.
Typical Usage:
Security experts, penetration testers, and network administrators commonly turn to Shodan for broad scans across the internet to locate services or devices that might be missed by conventional network scanning methods. Researchers also leverage its capabilities to study the security posture of IoT devices, and organizations rely on it to evaluate whether their externally facing systems are shielded from threats.
License Model:
Shodan uses a freemium system. At no cost, users can run limited searches and view basic data. More powerful options—like detailed scan results, greater query limits, and specialized security alerts—are unlocked through paid tiers. Pricing depends on the scale of queries and the level of service required.
Platforms:
As a primarily browser-based solution, Shodan can be accessed on any device running a modern web browser, whether it’s Windows, macOS, or Linux. Additionally, a RESTful API allows integration into custom security tools and automated workflows. Mobile applications are also available, enabling on-the-go analysis and scanning from smartphones or tablets.
Usage Example
Shodan’s interface and feature set closely parallel those of Netlas. You can filter search results by specific ports in its main query bar, and use Shodan Monitor to schedule recurring scans of chosen hosts with a customizable port list.
Recommended Reading
Netlas vs Shodan: Platforms Comparison
ZoomEye: The Other Passive One
ZoomEye is a robust online network scanning tool designed to provide users with deep insights into the devices, services, and vulnerabilities that exist across the internet. Often referred to as a powerful alternative to traditional scanning methods, ZoomEye specializes in identifying open ports, running services, and potential security threats by scanning devices across global networks. It is particularly useful for professionals looking for a fast, web-based solution to conduct comprehensive network assessments.
Project Details:
ZoomEye functions as an internet-wide search engine that scans connected devices, providing detailed information about their configuration, vulnerabilities, and potential security issues. It uses advanced algorithms to index devices and services across the internet, including IoT devices, servers, and other network-connected systems. With a user-friendly interface, ZoomEye allows users to search for specific types of devices or vulnerabilities and filter results based on various criteria like location, service type, and more.
Strengths:
- Wide Coverage: ZoomEye is capable of scanning the entire internet, helping users detect a wide range of devices and services, including those that may not be easily identifiable with traditional network scanning tools.
- Detailed Information: The tool offers extensive details about devices, such as open ports, operating systems, and running services, making it an excellent resource for security assessments and vulnerability detection.
- Search Flexibility: ZoomEye allows users to perform highly customized searches, including the ability to filter results by various parameters such as geographical location, service type, and device manufacturer.
- Real-Time Alerts: The platform supports real-time notifications and alerts, allowing users to stay updated on any new vulnerabilities or exposed devices that may require immediate attention.
Weaknesses:
- Limited Scanning for Private Networks: ZoomEye primarily focuses on public-facing devices, so it cannot be used to scan internal or private networks unless those devices are exposed to the internet.
- Complexity for Beginners: While it offers powerful features, the platform can be overwhelming for users with little to no technical background. Understanding how to filter and interpret the scan results can be challenging for novices.
- Restricted Free Access: The free version of ZoomEye offers limited access to scanning capabilities, and many advanced features, such as detailed reports and unlimited searches, are only available with a paid subscription.
Typical Usage:
ZoomEye is widely used by cybersecurity professionals, penetration testers, and network administrators to identify exposed devices, monitor for vulnerabilities, and perform routine security assessments. Its ability to scan the entire internet makes it ideal for discovering devices that are unintentionally exposed to the public, such as misconfigured servers, IoT devices, and other potentially insecure systems. It’s also popular among researchers looking to study internet infrastructure and IoT security trends.
License Model:
ZoomEye operates on a freemium model. The basic version provides limited access to its scanning capabilities, allowing users to perform a small number of searches and view basic results. For more extensive use, such as accessing detailed reports, performing unlimited searches, and receiving real-time alerts, users can subscribe to one of ZoomEye’s premium plans, which are priced based on the level of service and features required.
Platforms:
ZoomEye is a web-based tool, meaning it is accessible through any modern web browser on platforms such as Windows, macOS, and Linux. Its cloud-based infrastructure allows users to access the service from any device with internet access, providing flexibility and convenience. Additionally, ZoomEye offers an API for advanced users who wish to integrate its capabilities into other security tools or automation systems.
Usage Example:
Similar to Shodan, you can find examples of how to use ZoomEye in the dedicated article.
Recommended Reading
Netlas vs ZoomEye: Platforms Comparison
OpenVAS: The Vulnerability-Hunting One
OpenVAS is an advanced open-source vulnerability scanning tool used to identify and assess potential security threats within networks and systems. As a powerful alternative to proprietary vulnerability scanners, OpenVAS provides a comprehensive and customizable approach to identifying weaknesses in both internal and external infrastructures. It is widely used by security professionals for proactive security assessments, vulnerability detection, and risk management.
Project Details:
OpenVAS (Open Vulnerability Assessment System) is part of the Greenbone Vulnerability Management (GVM) suite, designed to provide detailed scans and comprehensive reports of network vulnerabilities. It is built on a modular architecture, allowing users to adjust and extend its capabilities. The tool is equipped with an extensive database of known vulnerabilities, enabling it to perform thorough scans of systems, web applications, and networks for misconfigurations, outdated software, and security loopholes. OpenVAS can be integrated with other security tools and offers both web-based and command-line interfaces for ease of use.
Strengths:
- Comprehensive Scanning: OpenVAS offers a wide array of scanning options, including network, web application, and host vulnerability assessments, ensuring complete coverage of potential security risks.
- Extensive Vulnerability Database: It is constantly updated with new security findings, keeping users protected against the latest vulnerabilities.
- Customizable and Flexible: The open-source nature of OpenVAS allows users to modify and extend its functionality to meet specific needs. Custom scan configurations can be created, and results can be tailored to specific formats for ease of interpretation.
- Integration Capabilities: OpenVAS can be integrated into larger vulnerability management systems, making it a versatile tool for security teams looking to automate vulnerability scanning as part of their security workflows.
Weaknesses:
- Complex Setup and Configuration: Setting up OpenVAS can be challenging for users who are not familiar with security tools or Linux-based environments. Configuration options are extensive, which can be overwhelming for new users.
- Performance Issues: Scans, especially deep or large network scans, can be resource-intensive, which may cause performance degradation on lower-end systems or in large-scale environments.
- User Interface: While OpenVAS offers a web-based interface, its design can feel less intuitive compared to commercial vulnerability scanners, potentially hindering the user experience for less experienced individuals.
Typical Usage:
OpenVAS is primarily used by network administrators, penetration testers, and security researchers to perform vulnerability assessments on IT infrastructure. It is commonly used for regular security audits, penetration testing, and compliance assessments. Organizations with in-house security teams frequently deploy OpenVAS to monitor their systems and proactively identify vulnerabilities before they are exploited by malicious actors. Additionally, it is valuable for conducting risk assessments and ensuring systems are up to date with the latest security patches.
Recommended Reading
7 Tools for Web Penetration Testing
License Model:
OpenVAS is distributed under the GNU General Public License (GPL), making it completely open-source and free for both personal and commercial use. Users can freely access, modify, and distribute the software as per the terms of the GPL. The open-source nature encourages community-driven improvements and regular updates, ensuring that the tool remains relevant in identifying the latest security vulnerabilities.
Platforms:
OpenVAS is primarily designed for Linux-based platforms, where it runs smoothly on distributions such as Ubuntu, Debian, and CentOS. It can be installed on both virtual machines and physical servers, offering flexibility in deployment. Additionally, OpenVAS can be used on macOS with appropriate configuration, though Linux remains the preferred platform for full functionality. The web-based interface is accessible via modern browsers, providing ease of access across different operating systems.
ZMap: The Modular Hacker One
ZMap is an open‑source network scanner optimized for conducting large‑scale internet research. Its modular design lets you plug in different probe modules for HTTP, SSH, DNS, and other protocols, going beyond mere port discovery.
Project Details:
Built on a high‑performance C core, ZMap sends customizable probes at line speed and processes responses asynchronously. An extensible plugin framework allows you to craft protocol‑specific modules (“ZMap modules”) to extract service banners, measure latency, or test TLS configurations—all in a single pass.
Strengths:
- Extensible Plugin System: Write or use existing modules (e.g., zgrab for banner grabbing) to tailor scans to specific protocols.
- High Throughput: Capable of scanning millions of IPs per second when appropriately provisioned.
- Research‑Friendly Output: Provides structured JSON results that integrate easily into data analysis pipelines.
- Broad Community Adoption: Widely used in academic and industry research, with active development and documentation.
Weaknesses:
- No Built‑in Deep Version Detection: Requires pairing with tools like ZGrab or custom modules to extract service details.
- Resource‑Intensive Setup: Achieving maximum throughput often necessitates distributed architectures and careful tuning of network hardware.
- Less User‑Friendly: Lacks a GUI; configuration is entirely via command‑line options and flags.
Typical Usage:
Researchers and large organizations leverage ZMap for internet‑wide surveys—such as measuring SSH adoption, TLS cipher usage, or HTTP header practices—by combining its scanning speed with custom modules to gather rich metadata in one sweep.
License Model:
ZMap is distributed under the 3‑clause BSD license, enabling free use in both open‑source and proprietary projects without licensing fees.
Platforms:
The core ZMap engine runs on Linux (with raw socket or libpcap support). Companion modules like ZGrab are available for Linux, macOS, and Windows, typically installed via Go or prebuilt binaries.
Usage Example:
ZMap is a command-line utility, so its usage is similar to Masscan and Nmap. Below is an example taken from the official documentation of the tool.
root@MacBook-Air ~ % sudo zmap -p 80 -r 128 171.67.70.0/23
171.67.71.204
171.67.71.128
171.67.70.245
171.67.71.191
171.67.71.186
171.67.71.202
171.67.70.240
171.67.70.242
171.67.71.192
0:05 42% (7s left); send: 512 done (127 p/s avg); recv: 91 17 p/s (17 p/s avg); drops: 0 p/s (0 p/s avg); hitrate: 17.77%
0:06 50% (6s left); send: 512 done (127 p/s avg); recv: 91 0 p/s (15 p/s avg); drops: 0 p/s (0 p/s avg); hitrate: 17.77%
0:07 59% (5s left); send: 512 done (127 p/s avg); recv: 91 0 p/s (12 p/s avg); drops: 0 p/s (0 p/s avg); hitrate: 17.77%
0:08 67% (4s left); send: 512 done (127 p/s avg); recv: 91 0 p/s (11 p/s avg); drops: 0 p/s (0 p/s avg); hitrate: 17.77%
0:09 75% (3s left); send: 512 done (127 p/s avg); recv: 91 0 p/s (10 p/s avg); drops: 0 p/s (0 p/s avg); hitrate: 17.77%
0:10 84% (2s left); send: 512 done (127 p/s avg); recv: 91 0 p/s (9 p/s avg); drops: 0 p/s (0 p/s avg); hitrate: 17.77%
0:11 92% (1s left); send: 512 done (127 p/s avg); recv: 91 0 p/s (8 p/s avg); drops: 0 p/s (0 p/s avg); hitrate: 17.77%
Dec 05 22:29:12.352 [INFO] zmap: completed Here SYN/ACK packets were sent to port 80 of each address in the IP range 171.67.70.0/23. The packet sending rate was set to 128 per second.
Summary
In closing, today’s landscape of network and device scanners offers a diverse array of solutions to suit varying needs. For quick, no‑installation reconnaissance, web‑based services like Nmap.online, Netlas.io, and ZoomEye deliver instant insights into open ports and connected devices — albeit with less configurability than their desktop counterparts.
When raw speed and massive scale are priorities, Masscan and ZMap shine. Thanks to their custom TCP/IP stacks, they can sweep vast address ranges in mere seconds, making them ideal for broad surveys. If your requirements extend beyond port discovery into vulnerability assessment, OpenVAS — with its plugin‑driven architecture and detailed reporting — provides a deeper level of analysis.
Ultimately, the optimal choice hinges on your objectives — whether that’s lightning‑fast bulk scans, in‑depth vulnerability audits, passive exploration of existing data, or a user‑friendly interface. By leveraging the right mix of these tools, you can build an efficient and resilient process for surveying and monitoring any network environment.

I can show you how deep the Internet really goes
Discover exposed assets, infrastructure links, and threat surfaces across the global Internet.
Related Posts

June 19, 2025
Nmap Cheat Sheet: Top 10 Scan Techiques

October 9, 2024
Complete Guide on Attack Surface Discovery

June 10, 2025
How to Detect CVEs Using Nmap Vulnerability Scan Scripts

June 16, 2025
Google Dorking in Cybersecurity: Techniques for OSINT & Pentesting

June 14, 2025
Domain Recon: Must-Know Tools for Security Professionals

June 25, 2025
theHarvester: a Classic Open Source Intelligence Tool





















