The Pyramid of Pain: Beyond the Basics
July 25, 2025
14 min read
Finding the right starting point when establishing or enhancing your security team’s monitoring and detection capabilities can be a challenge, especially when you’re trying to justify the need for (more) budget or resources. The Pyramid of Pain offers a practical framework for making those decisions. Developed by David Bianco in 2013, this model goes beyond being just a visual hierarchy of indicators. It’s designed to help security teams focus their efforts where they can have the most impact, by targeting the indicators that are genuinely difficult for attackers to change and thus causing them PAIN.
The value of the Pyramid of Pain lies in its ability to bridge the gap between threat intelligence and day-to-day security operations. Rather than collecting and responding to every low-level indicator, the model encourages teams to prioritize those that will significantly disrupt adversaries’ activities. This approach not only makes better use of limited resources but also helps justify investments in more advanced detection and response capabilities.
In this article, I’ll take a closer look at the origins and intent behind the Pyramid of Pain, and show how it can be applied in practical ways by security analysts. Whether you’re just getting started or looking to mature your security operations, understanding and using this model can help guide your team’s efforts and support stronger, more resilient defenses.
While doing research for this article, I initially wanted to create a modern and sleek-looking version of the model, because – well, look at it – it seems like it was drawn up in Microsoft PowerPoint. It turns out that it kind of is. While watching a B-sides recording from the creator and learning that the model was created in Microsoft SmartArt, I had no choice but to use the original work of art.
Want to know another fun fact about the Pyramid of Pain? Check out the trivia section at the end of this article.
The Origin and Purpose of the Pyramid of Pain

Why Was the Pyramid Created?
By Analysts, For Analysts
For most security and Threat Intelligence professionals, the year 2013 is a watershed moment in the history of cybersecurity and Threat Intelligence. This is the year that Mandiant, now part of Google Cloud, released its APT1 report, exposing the extensive cyber espionage activities conducted by China’s People’s Liberation Army Unit 61398 against organizations worldwide. And thus marking a turning point in understanding that not only nation-states are being targeted.
Bianco read the APT1 report and noticed that the indicators, part of the appendices, weren’t being applied very effectively. The entire point of detecting indicators is to respond to them and respond to them quickly. Because when you respond fast, you have denied the adversary the use of those indicators, which in turn forces them to change their operations.
Bianco designed the model to help security professionals prioritize their efforts, ensuring that defenders focus on actions that inflict the most operational pain on attackers. He aimed to help security teams “get beyond the atomic indicators and into the behaviors” to create a more effective detection.
Bridging Intelligence and Operations
The model closes the gap between threat intelligence and day-to-day security monitoring, translating abstract indicators into actionable priorities. In one simple image, the model shows that real value does not lie in onboarding millions of trivial indicators, like hashes, IP addresses, and domain names. Those are simple to switch! But to focus on where it can really hurt the adversary and where they need to invest time and money to change their game.
Still, incorporating low-level indicators can provide rapid, automated blocking and support early detection of known threats, serving as a valuable component in a comprehensive security strategy.
Driving Strategic Defense
The pyramid encourages defenders to move beyond surface-level indicators (like hashes, IPs, and domains) and target adversary behaviors that are genuinely disruptive to change. The strategic shift begins with Network and Host artifacts such as registry keys, file paths, URL patterns, or user agents. Detecting these artifacts forces threat actors to make changes to their code, recompile, retest, and redeploy, which is not only annoying but also costly for them.
The downside of prioritizing your effort on things that offer the most potential benefit and make your systems most resistant to a particular threat actor is that this comes with a cost in terms of resources and, consequently, money for the defenders as well.
The Pyramid’s Structure
Six Levels, Ascending Difficulty
From hash values at the bottom to Tactics, Techniques, and Procedures (TTPs) at the top, each level represents a step up in the effort required for an adversary to adapt when defenders detect and block them.
Pain as a Metric
The higher up the pyramid, the more “pain” or cost you inflict on the adversary. Forcing them to invest more resources, time, and creativity to continue their campaign. However, the same is true for your own investment in time, resources, and money.
Dynamic, Not Static
In all its simplicity, the model is designed to evolve with the threat landscape without changing itself. It encourages you to strive for continuous improvement and adaptation in defensive strategies.
Impact on Security Mindset
Elegant in its simplicity, the pyramid has caused a significant shift in the way of thinking about different types of indicators of compromise.
Prioritization:
It helps analysts prioritize detection and response efforts for maximum effect.Resource Allocation:
Directs investment of time and technology toward high-impact, high-pain indicators, rather than those that are easily changed and offer minimal value.Continuous Learning:
Encourages teams to review and refine their detection strategies, always aiming higher up the pyramid.
Recommended Reading
Best Attack Surface Visualization Tools
Request Your Free 14-Day Trial
Submit a request to try Netlas free for 14 days with full access to all features.
Deep Dive: Split the Pyramid into three
The purpose of this article is to provide insight into the practical use of the pyramid for security teams. For this reason, I will not give a detailed summary of every layer of the pyramid, as the original author and many subsequent articles have done. Instead, I made a logical combination of the steps into low, medium, and high pain for the adversary.
Low Pain IOCs
In practice, the first three levels can be grouped as “low-pain” indicators of compromise (IOCs). They have much in common (e.g., relatively short time-to-live) and are very similar in management.
- Hash Values
- Unique digital fingerprints of files. Easily changed by attackers with minor file modifications. Blocking by hash is fast but only effective for known, static threats.
- IP Addresses
- Network locations used by attackers. Simple to rotate using VPNs or new infrastructure. Blocking IPs can be helpful, but attackers adapt quickly.
- Domain Names
- Human-readable addresses. Slightly harder to change than IPs due to registration and propagation delays, but still relatively low effort for attackers to swap out.
- Use these low-level indicators for immediate blocking purposes, understanding that their usefulness is often short-lived.
- These indicators are known to generate a lot of noise and false-positive alerts within a Security Operations Center. When possible, always combine with other intelligence to avoid whack-a-mole defense.
- Automate both the ingestion and expiry of these time-sensitive indicators to minimize noise and maintain detection accuracy.
IOCs Sources
As mentioned before, these low-pain indicators are easy to implement into your security operations. You can obtain these indicators from various sources, including free and community-driven resources, as well as commercially available options.
To complete the picture, I will provide a few sources below. However, these are merely the tip of the iceberg; numerous community and commercial products are also available. There are also multiple security companies that offer a free community edition in addition to their commercial enterprise products.
Please let me know in the comments if you want me to write an article on threat intelligence indicator sources.
Where to get indicators for free
- AlienVault OTX (Open Threat Exchange)
Offers a large, community-driven repository of threat intelligence, including hashes, IPs, and domain names. Data is available in formats like CSV, JSON, and STIX for easy integration.
URLhaus (by abuse.ch)
Focuses on sharing malicious URLs, domains, and associated IP addresses used for the distribution of malware. Provides regularly updated feeds and APIs for free access.Spamhaus (by abuse.ch)
Maintains blocklists of malicious IP addresses and domains, widely used for email and network security. Their SBL (Spamhaus Block List) and DBL (Domain Block List) are freely accessible for non-commercial use.AbuseIPDB
It is a widely used, community-driven threat intelligence platform specializing in the collection and sharing of reports about malicious IP addresses. Its primary focus is on helping organizations and individuals identify, block, and report abusive IP activity, such as hacking attempts, spam, DDoS attacks, and other forms of cyber abuse.
Commercial Indicator Feeds
There are plenty of commercial feeds that deliver high-quality, low-pain IOCs. Keep in mind that these products are sold at premium prices, which often makes it impossible to incorporate them into the security operations of smaller organizations or organizations with a small security budget.
CrowdStrike
Offers the Falcon Adversary Intelligence platform, which delivers real-time threat intelligence, including context-enriched indicators of compromise (IOCs) such as hashes, domains, and IP addresses.DomainTools
Specializes in domain and DNS-based threat intelligence, offering enterprise-grade feeds and APIs for domain names, IP addresses, and related infrastructure.Provides API access and integration with SIEM and other security tools, making it a robust source for operational threat data.RST Cloud
One notable commercial alternative is RSTCloud, which stands out for delivering high-quality indicators. RSTCloud scrapes and transforms publicly available threat reports into machine-readable formats, generating comprehensive summaries and detailed intelligence on threat actors, malware, CVEs, TTPs, industries, countries, indicators, and their interrelationships. Importantly, they offer these services at a fraction of the cost of major security vendors, including those listed above.Your own investigation
Last, but by no means least. In my opinion, the best source for low-pain indicators is your own security incident response, threat hunts, and pivots of generally known and/or published ones. Indicators you discover within your own environment (such as suspicious hashes, IPs, or domains) are directly tied to your specific network, assets, and threat landscape. This means they are immediately actionable and relevant to your security posture.
Medium Pain Indicators
Climbing up to the group of “medium pain” indicators – harder to detect, much costly to replace.
- Network/Host Artifacts
- Registry keys, file paths, or protocol patterns left by attacker activity. Harder to change than IP addresses or hashes, as they may require modification of a tool or technique.
- Tools
- Software used by adversaries that they bring with them (e.g., password crackers, RATs). If defenders detect and block specific tools, attackers must develop or acquire new tools, which makes it a more costly process.
- Behavioral Patterns
- These are sequences of actions where adversaries use built-in system tools. A tactic known as living off the land (LOL). These techniques are more complicated to detect between the noise of “normal” use and harder to adapt, forcing attackers to rethink their approach.
- Develop detection rules for artifacts unique to attacker tools or behaviors.
- Monitor for unusual or unauthorized tool usage on endpoints.
- Conduct hypothesized threat hunting to uncover new artifacts and behaviors, based on known indicators of adversary behavior.
Detect medium pain indicators with YARA
YARA, short for “Yet Another Recursive Acronym” – which is my number one favorite acronym – is an open-source tool that helps security professionals identify and classify malware by using custom rules to match specific patterns in files, memory, or network traffic. It works much like a search engine for malicious code. You define what you want to find, such as a string, binary pattern, or a set of conditions, and YARA scans for those indicators across your systems and network. Its rule syntax is straightforward and readable, making it accessible for malware analysts, threat hunters, and incident responders.
For detecting network and host artifacts, YARA allows defenders to write rules that look for signs left by attackers. These can include suspicious registry keys, particular file names, or unique byte sequences that malware might leave on a host. On the network side, YARA can be integrated with network detection tools to scan files as they move through your environment, searching for malicious payloads or patterns in documents, executables, and emails. This helps identify threats before they reach endpoints or move further within your network.
Network and host artifacts, as well as adversary tools, are positioned higher up the pyramid, which means they are more difficult for adversaries to modify compared to simple indicators like hashes, IP addresses, or domains. Using YARA to detect these artifacts and tools can disrupt an attacker’s operations, as it may require them to alter their methods significantly. Using YARA as part of your Security Operations Strategy improves detection and makes your defense more robust.
High Pain: TTPs
And finally, the third group related to the higher level of the Pyramid is Tactics, Techniques, and Procedures (TTPs). This term refers to the adversary’s behavioral fingerprinting.
- Tactics
- The broad goals of an attacker (e.g., data exfiltration, persistence).
- Techniques
- The specific methods used to achieve those goals (e.g., credential dumping, phishing).
- Procedures
- The concrete steps and sequences are often tailored to specific types of targets.
- Map information from your company’s compromises to a framework like MITRE ATT&CK to discover what TTPs adversaries are already using against your organization.
- Focus threat hunting on behavioral anomalies rather than static indicators.
- Collaborate with intelligence teams to stay ahead of evolving TTPs. Consider joining an ISAC or an ISAO, depending on the type of organization you represent.
Understanding MITRE ATT&CK in Detecting Adversary Behavior
MITRE ATT&CK is a comprehensive knowledge base that organizes information about how adversaries behave during cyber attacks, based on real-world observations. It breaks down the steps attackers take, from gaining initial access to moving laterally and exfiltrating data. MITRE ATT&CK utilizes matrices that contain tactics (the attacker’s objectives), techniques (the methods employed to achieve those objectives), and sub-techniques (a more granular description of the overarching technique).
Using a matrix like the MITRE ATT&CK Enterprise matrix helps security teams describe and understand adversary actions in a standardized way, making it easier to communicate about threats and coordinate defenses.
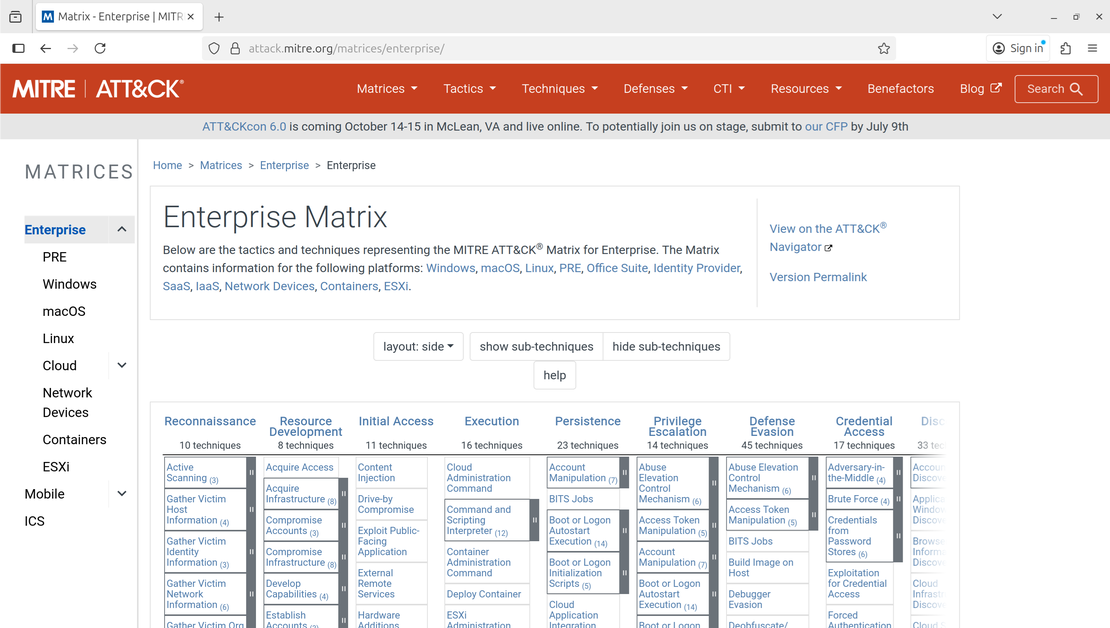
By mapping compromise activity in your environment to the tactics and techniques in the MITRE ATT&CK framework, you can focus on detecting the TTPs adversaries use, rather than just the tools or files they leave behind.
For example, if you notice unusual use of PowerShell or attempts to escalate privileges, you can check if these actions match known techniques in the framework. This approach enables defenders to identify suspicious patterns that may indicate an attack, even if the specific malware or infrastructure being used is new or has not been previously observed.
This behavioral focus on TTPs aligns with the top of the pyramid, meaning they are much harder for adversaries to modify than simple indicators, such as file hashes, IP addresses, or domains. Using MITRE ATT&CK to detect TTPs makes it more challenging for attackers to succeed, as they would need to change their core methods rather than just swapping out an IP address, malicious file, or domain name redirecting to their Command and Control (C&C) server.
Recommended Reading
Modern Cybercrime: Who’s Behind It and Who’s Stopping It
Applying the Pyramid of Pain in your Day-to-Day Security Operations
The pyramid of pain is a valuable model for your daily security operations because it helps you to prioritize which IOCs to focus on.
Every security team begins by monitoring lower-level indicators, such as file hashes, IPs, and domains, which are easy for analysts to start with. However, attackers can easily modify these, so blocking them might only delay an attack. Recognizing this, security teams should avoid wasting time on actions with little long-term impact and prevent alert fatigue caused by false positives. The next maturity step is to seek harder-to-modify indicators for more effective defense.
Using the Pyramid of Pain as a mental model, you begin to focus more on higher-level indicators, such as network or host artifacts, tools, and ultimately, TTPs. These are much more difficult for attackers to change, so detecting and responding to them can disrupt their operations in a more meaningful way.
This approach encourages a shift from reactive measures to a more proactive stance, making it harder for attackers to reuse the same methods against your organization.
Applying the Pyramid of Pain in your workflow really helps you make better use of your resources. Instead of spreading efforts thin across every possible low-level indicator, you can concentrate on those that will have the most impact if detected.
Focus on Behavioral Indicators
Behavioral indicators are tied to how attackers move within an environment, escalate privileges, or establish persistence. By using threat hunting activities to uncover these behaviors, analysts gain the ability to identify attacks even when new or unknown tools are employed.
Behavior-focused hunting involves taking a holistic view of attack chains and mapping observed activities to frameworks like MITRE ATT&CK. It means looking for sequences such as:
- unusual PowerShell executions,
- signs of lateral movement,
- repeated privilege escalation attempts,
- suspicious use of administrative tools,
- and many other behavioral indicators.
These events are more resilient to evasion and reveal underlying strategies rather than just surface-level artifacts.
Custom Detection Rules
Instead of relying solely on vendor-provided signatures, security teams should develop their own rules bound to specific infrastructure using YARA or SIEM tools.
Behavioral detection rules are most potent. Especially when informed by threat intelligence on active adversary TTPs and by lessons learned from previous incidents. Over time, layering customized behavioral rules strengthens the organization’s overall security posture and optimizes the impact of incident response efforts.
Incident Response and Escalation
Escalation paths should be defined based on the severity of detected indicators:
- When an incident is identified at one of the Pyramid’s lower levels, responses can be quick and automated for containment and mitigation.
- Higher detection levels should trigger more thorough investigation and remediation.
Creating escalation paths involves setting clear criteria for when to escalate and defining suitable response actions for each level. For instance, automated blocking may start with known malicious domains, but persistent or novel behaviors should trigger manual investigation. At the highest levels, responses include cross-team collaboration, forensic analysis, threat hunting, and alerts.
This structured approach allows organizations to respond effectively, reducing disruption and minimizing overlooked targeted attacks.
Learning from Incidents
After responding to any security incident, teams should systematically review and document which level of the Pyramid of Pain was targeted. Over time, documenting and analyzing the Pyramid level associated with each incident supports a culture of continuous improvement.
Lessons learned from each attack inform how detection rules and response processes can be refined or expanded to target higher-value indicators in the future. In April 2025, NIST released the 3rd revision of its Special Publication (SP) 800-61 “Incident Response Recommendations and Considerations for Cybersecurity Risk Management”. I am really excited about the fact that they revised the model to a more practical and realistic breakdown of phases. The Lessons learned part of the model is where the feedback loop is positioned.
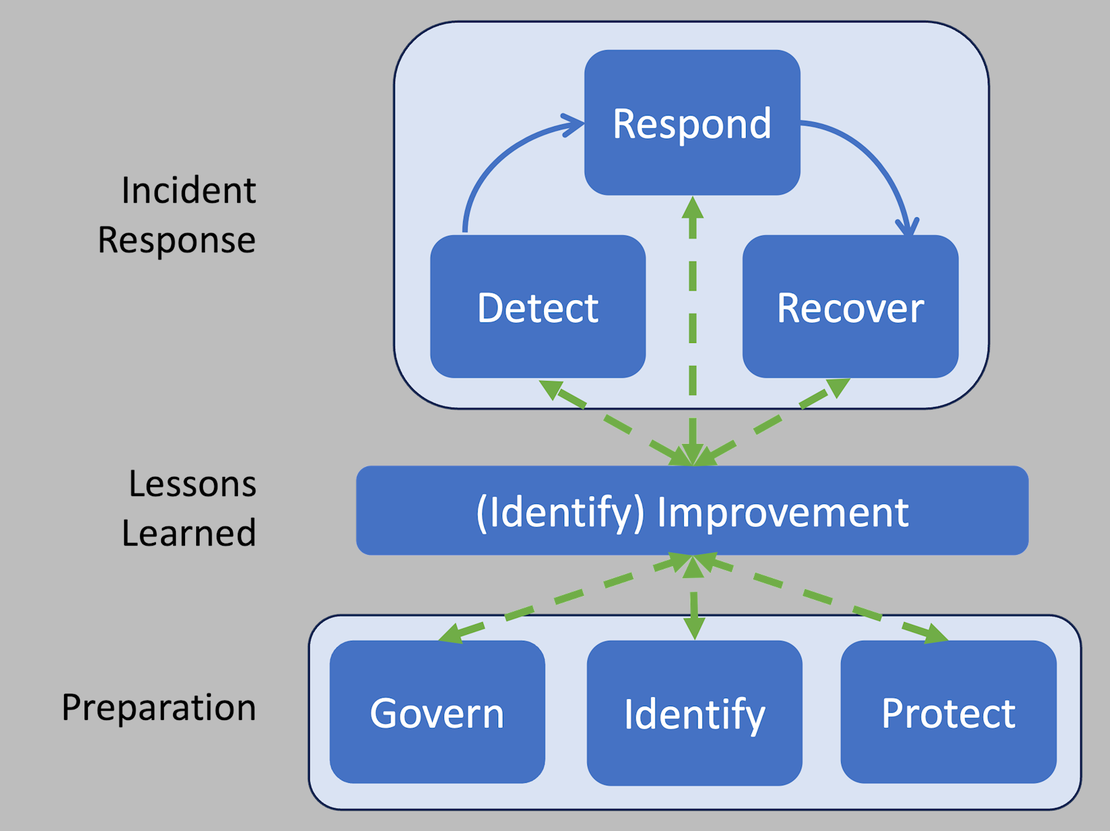
Push Detection Up Iteratively
Security teams should routinely review which detection rules and processes are working and which are being bypassed, using feedback from incident investigations, threat hunting outcomes, and new intelligence. With each new iteration, analysts can identify gaps and push detections further up the pyramid, increasing the cost and difficulty for attackers.
Continuous, iterative improvement is essential for maintaining effective detection and response strategies.
Metrics and Continuous Improvement
The number of detections at each level of the Pyramid of Pain can serve as a goal for improvement, aiming not only for broad detection but also specifically for increased coverage of high-pain indicators.
The same metric can be used to evaluate your threat intelligence sources – you should shift to the sources that elevate detection capabilities to highier-pain tiers.
Resource Allocation
Investments in behavioral detection, threat hunting, and tailored intelligence are effective because high-pain indicators are harder to bypass. Decision makers can use the Pyramid of Pain coverage metric to target spending on tools, expertise, or automation that increase adversarial costs, rather than just scaling efforts at lower levels.
By clearly linking spending to improvements in high-value detection, organizations defend better and show cybersecurity maturity and accountability, gaining leadership and stakeholder support for continuous improvement.
Conclusion
The Pyramid of Pain offers a practical framework for security operations teams to think about their detection and response strategies. By understanding that not all indicators are equal, teams can avoid getting stuck in a cycle of focusing on and blocking low-level indicators that attackers can easily change. The model encourages a gradual shift in focus toward higher-value indicators – those that require more effort for adversaries to adapt to and that offer defenders a better return on their investment of time and resources.
As organizations mature, applying the Pyramid helps to make better decisions on where to allocate effort and budget. Rather than spreading resources thin across every possible indicator, teams can prioritize those that will have the most significant impact.
Ultimately, using the Pyramid of Pain in daily workflow supports a more proactive and resilient security posture. It encourages ongoing improvement by prompting teams to review and refine their detection strategies, climbing up the Pyramid higher and higher. Over time, this mindset helps security teams stay ahead of evolving threats and respond more effectively when incidents occur.
As promised at the beginning of this article, I have one more piece of trivia about the Pyramid of Pain – this is actually version 2 of the model.
Can you guess the difference between v1 and v2?
Version 1 of the Pyramid of Pain did not include file hashes because Bianco initially did not see them as useful for incident detection. In his original 2013 blog post, the bottom level of the pyramid was “IP Addresses.” He later explained that while he was aware of hashes, he considered them “terrible for incident detection” and thought using them for that purpose was “a waste of time.” This is because file hashes are extremely easy for attackers to change – any minor alteration to a file results in a completely different hash, making them trivial for adversaries to bypass.
It was only after receiving many questions about where hashes fit in the model that Bianco revised the pyramid, adding static hashes as the new bottom layer, reflecting their limited value and the minimal “pain” they cause attackers when detected and blocked.
Be sure to check out the talk about the Pyramid on YouTube and the original blog post from 2013 by David Bianco.

I can show you how deep the Internet really goes
Discover exposed assets, infrastructure links, and threat surfaces across the global Internet.
Related Posts

July 18, 2025
Hannibal Stealer vs. Browser Security

June 25, 2025
Modern Cybercrime: Who’s Behind It and Who’s Stopping It

June 14, 2025
Domain Recon: Must-Know Tools for Security Professionals

May 31, 2025
TAI Challenge 2025 Recap

June 8, 2025
Best Honeypots for Detecting Network Threats

February 12, 2025
Netlas vs Censys: Platforms Comparison


















