From Starlink to Star Wars - The Real Cyber Threats in Space
November 21, 2025
22 min read
Every time you navigate with Google Maps, stream a movie on a flight, or track a storm approaching your city, a silent army of satellites makes it all possible. These orbiting machines are the invisible threads holding together our global economy, communication systems, and defence networks.
But what if those threads were cut, or hijacked?
In the modern world, space has gone from being a distant scientific playground to a crucial extension of our digital world. And just like every other connected system, it’s becoming a target. Hackers, cyber-spies, and even militaries are starting to see satellites not as tools of exploration, but as weapons, shields, and strategic leverage.
The scary part is that many satellites weren’t built for this kind of fight. A lot of them run on outdated software that was designed decades ago, and can’t be patched remotely. That means once something goes wrong up there, it might stay wrong.
In this article, we’ll explore the hidden world of space cybersecurity, how satellites that power our daily lives are becoming targets in a new kind of digital conflict. From internet constellations like Starlink and OneWeb to military systems orbiting miles above us, the battle for space is no longer just about rockets and payloads; it’s about data, access, and control.
We’ll uncover how hackers exploit vulnerabilities in satellite communication, revisit real-world incidents where space systems were compromised, and see what experts are doing to make the final frontier more secure.
This article is part of the Future of Cybersecurity series, a collection of upcoming stories exploring how technology frontiers are reshaping digital security.
Because our world is growing more connected. The boundaries of cybersecurity are expanding, even beyond Earth.
The Rise of the Space Internet
Not too long ago, getting internet from space sounded like something out of a sci-fi movie. But today, it’s quietly becoming real, and it’s changing how the entire planet connects.
Thousands of satellites are now orbiting above us, forming invisible webs that can beam internet to even the most remote of areas.
The idea is simple but powerful. Instead of depending on fibre cables buried under the ocean or cell towers that stop at borders, companies like Starlink, OneWeb, and Amazon’s Project Kuiper are building the internet straight from the sky.
How It Actually Works
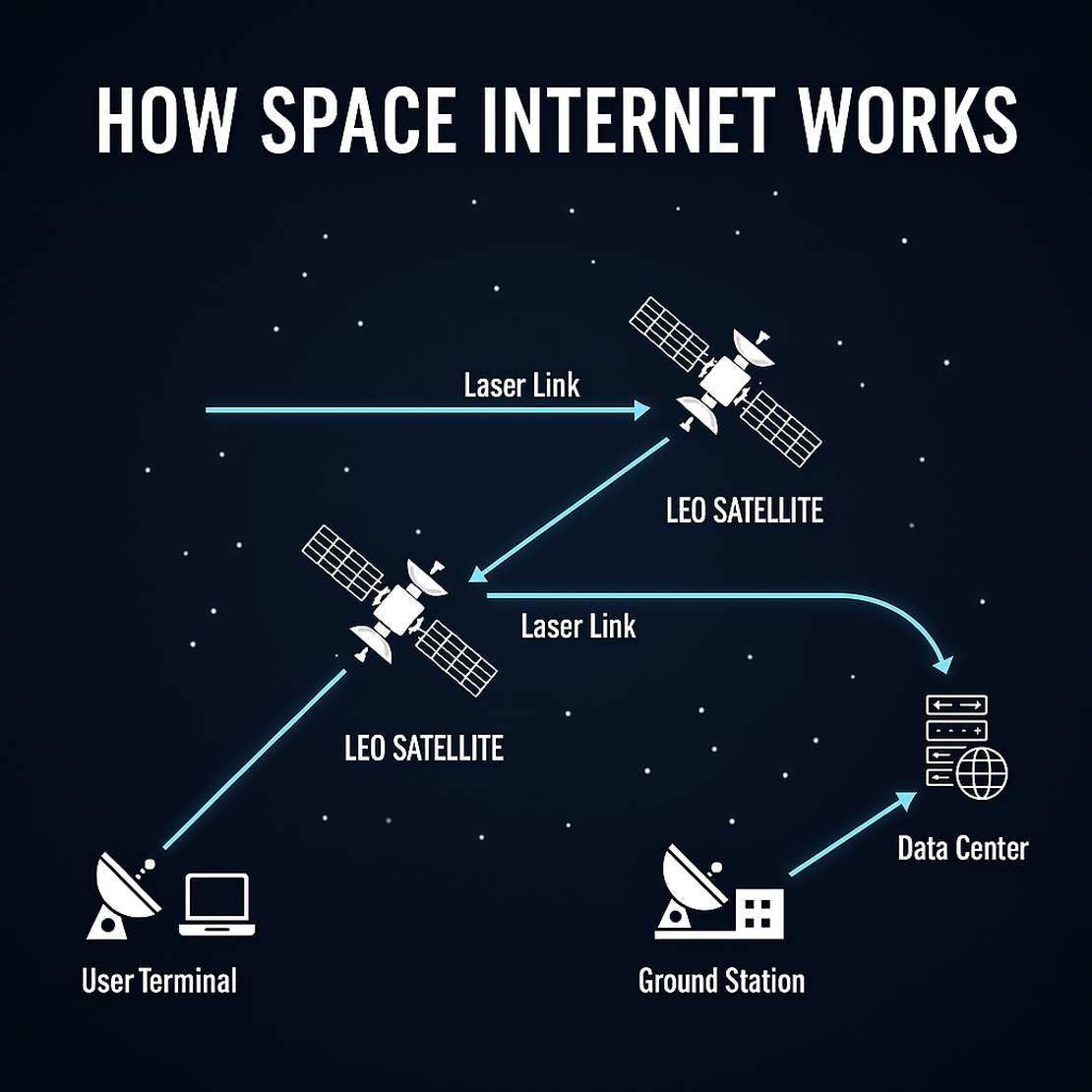
Think of each satellite as a flying Wi-Fi router. They move in Low Earth Orbit, just a few hundred kilometers above us, and talk to both the ground stations and each other, using laser beams that transfer data at almost the speed of light.
So when you connect to Starlink, your data might jump from your rooftop antenna to one satellite, then to another, and then to a ground station on another continent, all in milliseconds.
It’s fast, global, and reliable, but this kind of web of connectivity also brings a new kind of problem.
Expanding Competition
The number of satellites in orbit has grown rapidly over the last few years. Starlink, owned by SpaceX, currently operates more than 6000 satellites, and the company plans to expand it to over 12000 by the year 2027, and to over 34000 in the long term.
OneWeb has deployed around 600 satellites, focusing on government and commercial clients, while Amazon’s Project Kuiper is preparing to launch a constellation of over 3,200.
These projects are part of what experts call “mega-constellations”, which are massive groups of interconnected satellites forming a network that covers the entire planet. While they do bring faster internet and global access, they also cause orbital crowding and increase the risk of space debris. A single collision amongst them could create thousands of fragments that may damage other satellites, creating a chain reaction known as the Kessler Syndrome.
Real World Impact
These satellites have already shown their potential in real situations, for example:
- During the Tonga Volcanic eruption in 2022, the undersea cable that connected the island to the world was cut off, when Starlink was deployed to restore communication within days.
- During the war between Russia and Ukraine, Starlink terminals were used to maintain communications for civilians and government agencies in the event of damage to local infrastructure, as well as for the military on both sides of the conflict.
- Rural Regions in Africa, India, and South America have started using satellite based internet for education, telemedicine and agriculture data collection.
The Hidden Risk in the Sky
Every time a new satellite joins the network, it is another node that needs to be secured. And because these systems are constantly moving and handing off connections to one another, there is no single fixed point to guard.
If one part of the system gets exploited, the attack could affect hundreds of satellites.
It’s not just a bad connection anymore; it’s the potential to take entire regions offline, or worse, to spy on global data traffic flowing through space.
The Space Internet is really crucial for us, but it’s also creating new dependencies. Many countries and organizations now rely on privately owned satellite networks controlled by a few large corporations.
If these systems are ever disrupted, large parts of the world could lose access to communication instantly.
As we move forward, ensuring security, sustainability, and fair access will be really important. Space is no longer just an empty void; it’s slowly becoming the backbone of our digital world.
Anatomy of a Satellite
Looking from far away, satellites might look like distant dots moving across the night sky, but up close, they’re highly complex machines, a mix of hardware, software, and communication systems orbiting hundreds of kilometers above Earth.
To understand how hackers could target the satellite, we first need to understand how a satellite actually works.
A typical satellite can be divided into three main sections:
- The Bus (Body)
- The Payload (Purpose)
- The Communication System (Control and Data Flow)
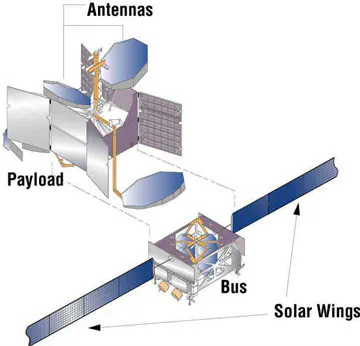
Each part plays a specific role, and each can become a potential entry point for attackers.
1. The Bus: The Satellite’s Body
This is the backbone of a satellite. It houses all the essential systems that keep it alive and functioning.
Some main components are:
- Power System: Solar panels and batteries supply electricity
- Thermal Control: Regulates temperature as the satellite faces extreme heat and cold.
- Propulsion System: Small thrusters or reaction wheels adjust its position and orbit.
- Onboard Computer: The brain that manages power, navigation, and communication.
Now let’s see where the vulnerabilities could exist:
- Command Hijacking: If attackers intercept or spoof command signals, they could manipulate orbit or disable systems.
- Unpatched Firmware: Older satellites may still run outdated software without encryption or authentication.
- Telemetry Manipulation: Fake data could be injected into the satellite’s health monitoring systems to hide faults or mislead ground operators.
2. The Payload
This is why the satellite was launched.
The payload is the part that performs its main job, whether that’s communication, imaging, navigation, or research.
Key Elements of a Payload:
- Transponders: They receive signals, amplify them, change frequencies and then retransmits them to ground stations.
- Antennas: They are used for receiving and transmitting signals to and from the satellite.
- Sensors and Instruments: Majorly used to collect data, examples include cameras and spectrometers.
- Receivers: They convert radio frequencies to signals.
- Transmitters: They send processed signals back to Earth
Examples:
- Communication satellites: transponders and antennas.
- Weather satellites: sensors and radar imagers.
- GPS satellites: atomic clocks and signal generators.
Possible Vulnerabilities:
- Signal Interception: Attackers can eavesdrop on unencrypted downlinks or manipulate data.
- Jamming & Spoofing: By sending fake or stronger signals, hackers can disrupt communication or feed false information.
- Payload Control Exploits: If the onboard payload control software is compromised, attackers can alter transmission frequencies or shut down instruments remotely.
3. The Communication System
Every satellite needs to talk to Earth. This is handled through Telemetry, Tracking, and Command (TT&C) systems. They send data to ground stations and receive instructions from mission control.
How It Works:
- Uplink: Commands are sent from ground stations to the satellite.
- Downlink: The satellite sends data and status updates back to Earth.
- Cross-Link (Laser Link): Some modern satellites talk directly to each other for faster global coverage.
Possible Vulnerabilities:
- Ground Station Breaches: Hackers targeting the ground network can issue fake commands.
- Interception of TT&C Links: Attackers can listen or inject commands if its not encrypted.
- GPS Spoofing: By falsifying location data, attackers can make satellites believe they’re elsewhere in orbit.
Threat Landscape: How Hackers Target Space
An attack on a space system is rarely a single, brute-force event. It’s a kill chain, a series of steps, and it almost always begins on Earth.
Hackers view satellite networks in three distinct segments, each with its own set of vulnerabilities: the Ground Segment, the Communication Links, and the Space Segment.
1. Attacking the Ground Segment
This is, by far, the most common attack vector. Why build a billion-dollar antenna to attack a satellite 500 km away when you can just hack the building on Earth that controls it? These are IT networks, and they suffer from the same vulnerabilities as any corporate system.
Supply Chain Attacks
The attacker doesn’t attack the network at all. They inject malicious code into a trusted software before it’s even installed. This way, the attacker tricks the system into willingly distributing the malicious code to all its connected devices.
Ground Station Intrusion
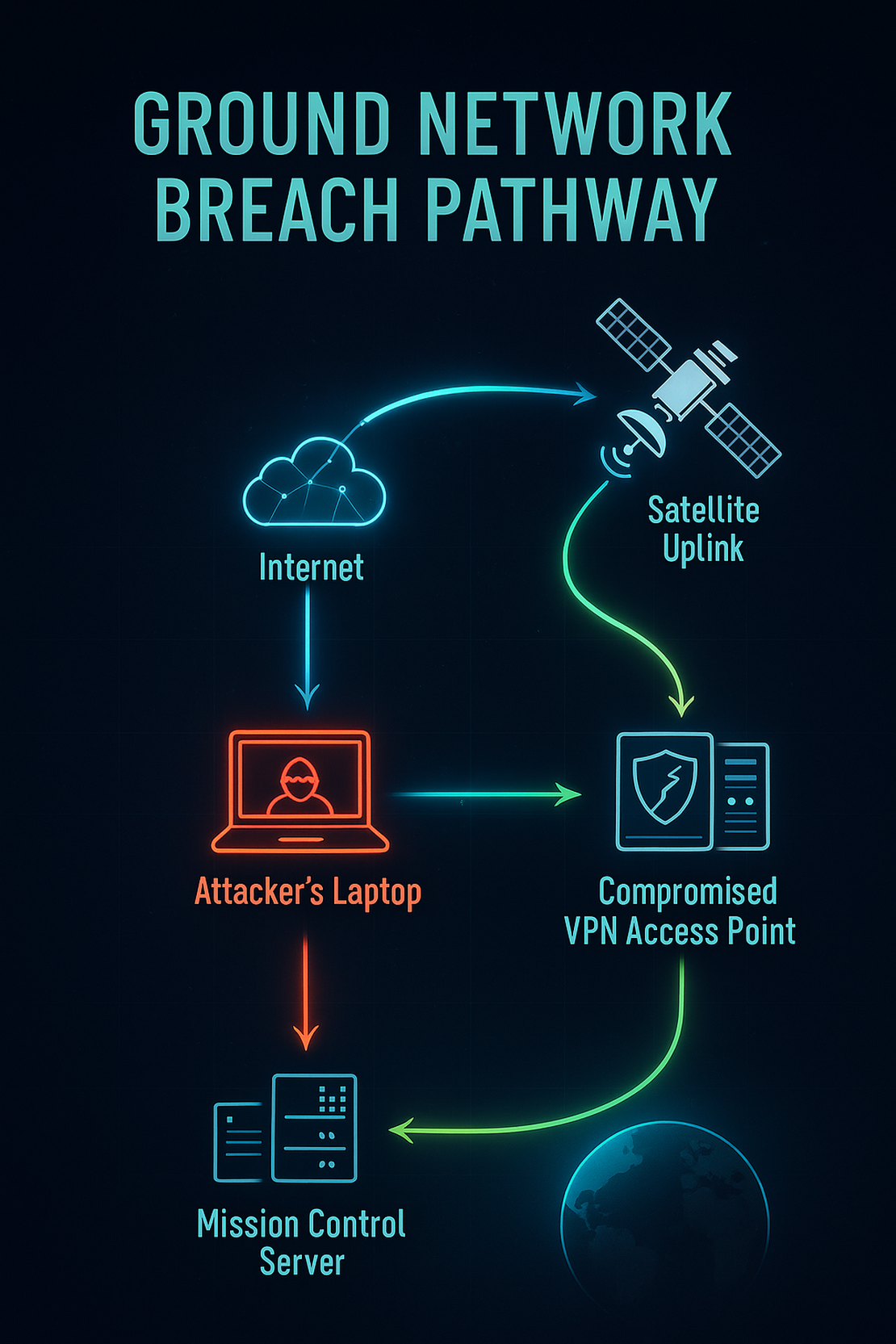
This is a classic network infiltration. The ground station is a data center running on standard IP networks, using commercial VPNs, and managed by humans who can be phished.
By breaching the ground station’s IT network, an attacker can gain access to the Mission Operation Center computers and send commands as if they were a legitimate operator.
User Terminal Exploitation
This is a new, massive attack surface created by mega constellations. Every Starlink or OneWeb terminal is a network-connected device, essentially an IoT endpoint. A vulnerability in the terminal’s software could allow an attacker to take it over.
For example, in 2022, A security researcher Lennert Wouters demonstrated a hardware attack on a Starlink dish using a $25 homemade modchip. He was able to glitch the terminal’s processor during boot-up to bypass security and gain root access.
2. Attacking The Communication Links
This is a direct attack on the radio frequency signals traveling between the ground and the satellite. This is the domain of Electronic Warfare, and it doesn’t require much hacking; it requires physics.
Jamming
This is like the brute force method. The attacker uses a powerful transmitter to shout radio frequency noise, which is on the same frequency as the satellite is using. This noise drowns out the actual signal, and the receiver on the ground cannot make sense of the data. It’s equivalent to a Denial of Service attack for satellites.
Spoofing
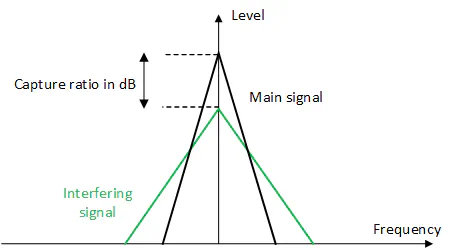
This is far more insidious than jamming. Instead of just shouting, the attacker impersonates them and broadcasts a fake, but realistic-looking signal that is stronger than the actual one. The capture effect forces the receiver to lock onto the fake signal. We will discuss the capture effect later in this article.
In 2013, researchers from UT Austin famously demonstrated this by spoofing the GPS signal of an $80 million Superyacht. The yacht’s navigation system then followed the fake coordinates, slowly veering off course.
Eavesdropping:
Passively listening in is called eavesdropping. Many satellite downlinks, especially for media feeds or older scientific data, are unencrypted. The assumption was that you’d need a giant expensive dish to listen.
But the rise of cheap Software defined radios (SDRs) completely changed this. For under $100, anyone can buy a USB-based SDR that can tune into a massive range of satellite frequencies and, with the right software, decode the signals. Researchers have used SDRs to intercept everything from unencrypted military drone footage to commercial airline data.

3. Attacking the Space Segment
This is the most difficult, expensive, and interesting category of attack. It involves targeting the satellite itself.
Direct Software Exploits
Gaining access to the satellite’s brain, the On-Board Computer. This could be done by finding a vulnerability in its command protocol or by exploiting the legacy software it runs on.
Many satellites in orbit today run on real-time operating Systems (RTOS) like VxWorks or RTEMS. A 2020 security audit of a version of VxWorks (which is used on the Mars Rovers, and among many other space assets) found many critical vulnerabilities, including a stack overflow which could allow for remote code execution. If an attacker can get a malicious command packet to the satellite, they could theoretically take it over.
Kinetic Anti Satellite (ASAT) Attacks
This is the physical “Hard kill” option. A nation state launches a missile from the ground and guides it to physically collide with the satellite, shattering it into pieces.
In November 2021, Russia conducted an ASAT test, launching a Nudol missile to destroy one of its own defunct satellites. This test was a success, but it created a cloud of over 1500 trackable pieces of debris that threatened the International Space Station and every other satellite in Low Earth Orbit.
Directed Energy Weapons (DEW)
Here, instead of a missile, the attacker uses a powerful, ground-based laser or high-powered microwave weapon. Lasers can be used to dazzle a satellite’s optical sensors; they can also burn out the sensors, and HPMs can fry a satellite’s sensitive electronics.
While traditional cybersecurity focuses on code and network breaches, securing our space infrastructure also means defending against electronic and kinetic threats like jamming and anti-satellite (ASAT) weapons. In modern hybrid warfare, all three methods are used to achieve the same goal: denying access to data and communications.
Now, let us look at some real-world Space Cyber Incidents that included exploitation of similar threats.
Request Your Free 14-Day Trial
Submit a request to try Netlas free for 14 days with full access to all features.
Real World Space Cyber Incidents
It is easy to dismiss space hacking as the plot of a James Bond movie or a futuristic video game, but the reality is far more sobering. The weaponization of space code isn’t a theoretical risk for the future; it is a historical fact.
From state-sponsored cyber warfare to rogue signal hijackings, the vulnerabilities in our orbital infrastructure have been tested and exploited for decades. Here, we discuss the most significant breaches that proved the air gap between Earth and Space is not as secure as we thought.
The Viasat Hack 2022

On February 24, 2022, exactly one hour before Russian troops crossed the border into Ukraine, a massive cyberattack paralyzed the KA-SAT satellite network owned by Viasat, which provided high-speed internet to Ukraine’s military and police forces. The goal was to blind the Ukrainian defense command during the first few hours of the conflict. This wasn’t just a DOS attack; it was a calculated, digital assassination of hardware.
Intelligence agencies later attributed this attack to “AcidRain”, a specifically designed wiper malware developed by Russian military intelligence.
How They Did It:
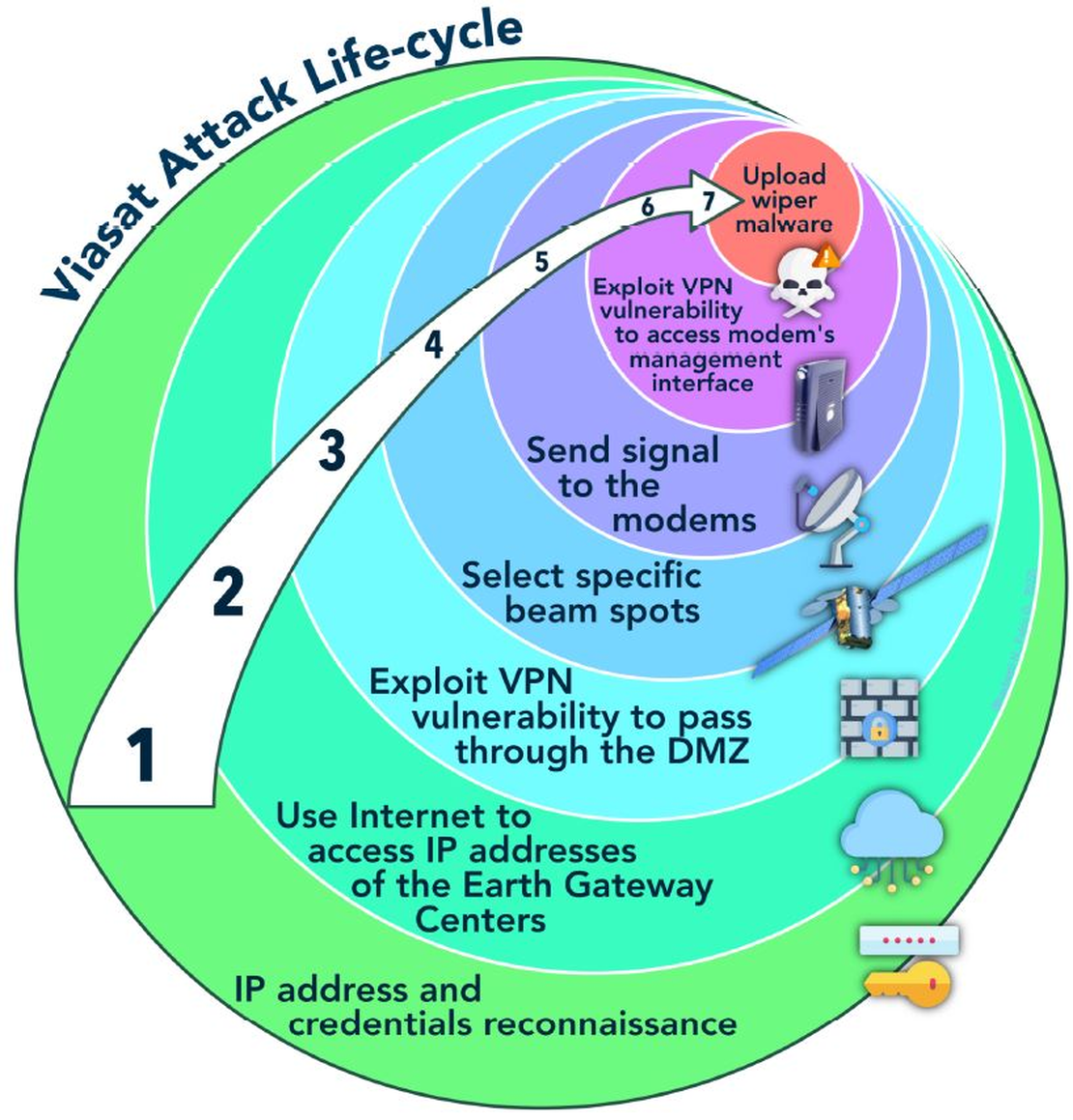
- Reconnaissance & Entry: First, the attackers identified and gained access to the trusted management network through a misconfigured VPN appliance.
- Pivoting: Once they were inside, they weren’t on the critical network yet, They had to pivot, moving laterally to discover the management platform, which was the central nervous system for the KA-SAT network.
- Hijacking Control: They established a shadow session, acting as a legitimate operator, and began sending their own commands to the modems.
- The AcidRain Payload: From this trusted position, they executed their final command through which they pushed the AcidRain malware as a fake firmware update. The malware didn’t just disconnect the modems; it overwrote their flash memory permanently.
This attack successfully disrupted communications for the Ukrainian military. However, the spillover damage was massive.
- Over 5800 wind turbines in Germany lost remote monitoring capabilities because they relied on Viasat modems.
- Emergency services in France experienced outages.
- A lot of modems were now instantly useless and required factory replacement.
This incident proved that Supply chain attacks are the biggest threat to space. You don’t need a rocket to take down a satellite; you just need admin access to the ground server that pushes the software updates.
The Terra EOS & Landsat Breaches (2007-2008)
In a chilling report released by the US-China Economic and Security Review Commission, it was revealed that hackers had achieved “command and control” access to U.S. government satellites not once, but four times between 2007 and 2008.
The Incidents:
- Landsat-7 (Oct 2007): The earth observation satellite experienced 12 minutes of interference.
- Terra EOS (June 2008): The outcome was much more severe in this case. Hackers achieved all the steps required to command the satellite for two whole minutes.
- Terra EOS (Oct 2008): The attackers returned, bypassing security again for nine minutes this time.
NASA satellites communicate via TDRSS (Tracking and Data Relay Satellite System), but they also dump data to commercial ground stations. The investigation later revealed that the hackers didn’t hack NASA directly. They targeted the Svalbard Satellite Station in Norway, which is a commercial facility that connects to NASA via the internet.
How It Happened:
- The hackers compromised the ground station’s internet-facing network.
- They monitored the data that was flowing into the station to understand the communication protocols.
- They successfully spoofed the authentication tokens, tricking the satellite into believing the commands were coming from a legitimate Operations Center.
The scary part is that during those 9 minutes in October, the hackers had Level 4 Access. This means they had access to the satellite’s flight control box.
They could have:
- Fired the thrusters to degrade the orbit
- Shut down the battery heaters, which would freeze the battery cells
- Pointed the optical sensors at the sun to blind them, but they did none of this, they simply gained access, proved they were there, and left.
The “Captain Midnight” Hijack (1986)
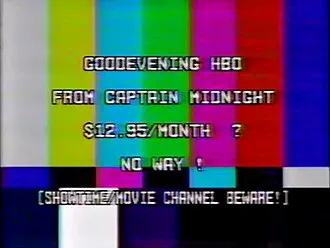
Before the internet era, Hacking space was a game of brute force. The most famous case occurred in 1986, on April 27th, and it perfectly illustrates the concept of Signal Overpowering, a vulnerability that still plagues satellites today.
On a fine day, Viewers across North America watching the movie “The Falcon and the Snowman” on HBO suddenly saw their screens flicker. The movie signal was cut out and it was replaced by a text overlay on a color bar background, which said:
GOODEVENING HBO FROM CAPTAIN MIDNIGHT $12.95/MONTH ? NO WAY !
SHOWTIME/MOVIE CHANNEL BEWARE!
Now you must be thinking, what does this mean?
“Captain Midnight” was actually John R. MacDougall, an electrical engineer in Florida who worked at a teleport facility. He was protesting the rising fees for satellite TV dishes.
So how did he actually do it?
The Capture Effect
Satellites act as “bent pipes”; they receive a signal from Earth, amplify it, and then send it back down. They generally listen to the strongest signal they can hear.
- HBO was uplinking its movie feed to the Galaxy 1 satellite.
- MacDougall pointed his massive industrial uplink dish at the same satellite.
- He transmitted his text signal on the exact same frequency but increased the wattage significantly.
- The satellite’s receiver was overwhelmed by MacDougall’s stronger signal. Due to the “Capture Effect” in FM modulation, the satellite locked onto the stronger signal and treated HBO’s signal as background noise.
 Credits - cdt21.com
Credits - cdt21.com
Though this happened in 1986, the physics still haven’t changed. This is exactly how modern military Jamming and Spoofing works. When a GPS signal is jammed in a war zone, it is simply an attacker on the ground shouting louder than the GPS satellite, confusing the receiver.
From Starlink to Star Wars - The Militarization of Space
The lines that once separated space as a sanctuary for peaceful use have effectively collapsed. Space has now become a warfighting domain, a reality accelerated by the 2022 conflict between Russia and Ukraine, which showed us that orbital systems are now central to the day-to-day conduct of armed conflict.
Defining the Modern Battlefield
The main problem is that our laws are still stuck in the 1960s. The 1967 Outer Space Treaty, which is the rulebook for space, has a massive loophole. It bans “nuclear weapons or other weapons of mass destruction” from orbit, but it doesn’t say anything about conventional missiles, lasers, jammers, or cyber attacks.
Think about it, A satellite with a robotic arm could be a friendly mechanic, used for repairing a broken satellite or cleaning up space junk. But that exact same satellite could also be used as a space stalker, creeping up on an adversary’s satellite to grab it, disable it, or smash it.
The U.S. Space Force
This new, unstable reality is why the United States Space Force (USSF) was created in 2019.
It’s an active warfighting branch. Its official goal is “Space Superiority”.

The Space Pearl Harbor Problem:
For decades, the U.S. military’s biggest fear was a Space Pearl Harbor, a sudden surprise attack that could wipe out its most critical satellites.
Why? Because the U.S. military’s entire model was built on a few exquisite, multi-billion-dollar satellites in high-altitude orbits. They were giant, expensive, and incredibly vulnerable targets. Losing even one or two in a surprise attack would be devastating.
So the space force flipped the script.
Instead of a few expensive satellites, they’re building thousands of small satellites. This new strategy is called Proliferated Warfighter Space Architecture (PWSA). It means launching hundreds, or even thousands, of smaller, cheaper satellites to Low Earth Orbit.
The Old way: “Don’t attack my giant expensive satellite, or I’ll punish you”.
The New Way: “Go ahead, attack my cheap, small satellites. I have thousands more, Your attacks won’t work because the network is a mesh and can’t be easily taken down”.
This shift is the biggest change in U.S. space strategy in 50 years.
Your Internet Provider is Also a Military Target.
The war in Ukraine was the perfect example of how the lines between commercial and military space have blurred.
The war’s first shot was a textbook space cyberattack, as we discussed earlier.
Into this vacuum stepped SpaceX. Its Starlink constellation became a lifeline for Ukraine, providing an internet backbone that the Russian military couldn’t easily disrupt.
However, this created a huge problem. A private CEO now had the power to influence battlefield outcomes. And Russia threatened that this “quasi-civilian infrastructure may be a legitimate target for a retaliatory strike”.
The U.S. government’s solution was to formalize the relationship; they introduced Starshield. It’s a separate, secured satellite network for government entities built by SpaceX. This hybrid model, however, creates a targeting paradox. The civilian Starlink and military Starshield networks are fundamentally connected.
It’s like putting a military command center inside a public hospital. An attacker now faces an impossible choice: to attack the military target, they risk spillover attacks that could cripple the civilian network. This effectively turns the global civilian network into a ‘human shield’ for the military’s assets.
China’s Learnings from Russia’s Mistakes
China sees space as a key to winning modern conflicts. But for years, it had a problem: how to get its space, cyber, and ground forces to work together.
Then, in 2022, they witnessed the unsuccessful start of the military conflict between Russia and Ukraine. So in 2024, China did something stunning: it completely dissolved its own high-tech military force (the PLASSF). They immediately rebuilt, creating three new, hyper-focused arms:
- The Aerospace Force: For all the space operations
- The Cyberspace Force: For all the cyber warfare
- The Information Support Force: to run the networks that tie them all together
The War We Can’t See: Code and AI
The most likely and most immediate form of space warfare won’t be a missile. It will be a line of code.
The Functional Kill
This achieves the same results as a missile, disabling a satellite, but without the debris. The 2022 Viasat hack was the blueprint.
The attackers did not target the satellite in orbit. They targeted the ground segment.
AI Driven Warfare
The new mega constellations are creating a data flood. There is simply too much data out there and not enough analysts to sift through it. AI is the only solution.
The DoD’s project Maven, for example, uses AI to automatically scan satellite imagery to find targets, and according to indirect evidence, it is already being used to support forces in Ukraine. But the scariest step is moving AI from analysis on the ground to operation on the satellite itself. In a high-speed space battle, humans are just too slow. You can’t dodge a laser travelling at the speed of light. So new satellites are being built with onboard AI to execute defensive maneuvers without waiting for a command from Earth. This creates a risk of accidental “Flash War”.
Let’s say an autonomous U.S. satellite detects an autonomous Chinese satellite nearby. The U.S. AI, on the machine, decides the move is hostile and executes a defensive maneuver. The Chinese AI, then, interprets this defensive move as an offensive strike and responds in kind. The entire war could be fought and concluded before a single human operator on the ground even knows it has begun.
Securing The Space Frontier
So, space is a huge and expanding target. How does someone even begin to defend something that is orbiting 500 kilometers above you, moving at 17,000 miles per hour?
You can’t just unplug it or send out a technician. This is the fundamental challenge of space cybersecurity. And to solve this, experts are building a defense-in-depth strategy. Think of it as a series of layers, like an onion.
The first big problem is what’s already up there. For decades, we built satellites assuming that because they were so high up and inaccessible, they were safe.
Because of this, many were launched with dated technologies and without any real security. They often lack modern encryption and have no way to be patched remotely. This means an old satellite is a persistent vulnerability, an unfixable weak spot that attackers can target again and again.
New networks like Starlink are built with better security, but they have the opposite problem. Because they are deeply connected to the cloud and use Ground Station as a Service providers, they can be vulnerable to the same IT world problems, like misconfigurations and supply chain attacks.
Now, let us see the layers to protect the satellites.
Layer 1: Securing the communication links
This is the most basic layer. The most important link is called the Telemetry, Tracking, and Command (TT&C). This is the brain of the satellite. If a hacker can get control of this, they own the satellite. They can shut it down, point it in the wrong direction, or even destroy it.
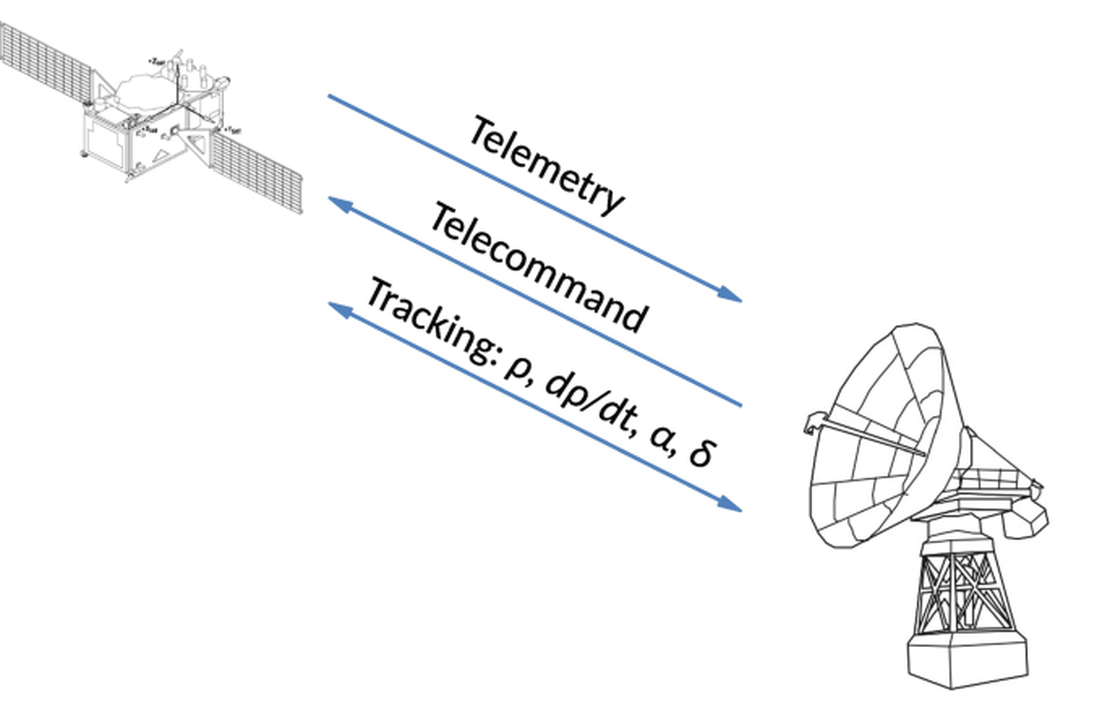
To protect it, you need two basic things:
- Authentication: The satellite must be able to reject fake commands and verify that the operator is really who they say they are.
- Encryption: The command must be scrambled so an attacker cannot eavesdrop on it.
But here is the real challenge: key management. Many of the old satellites were launched with a single master key. If an attacker ever steals that one key, the satellite is permanently insecure. Modern systems are now being designed with a new protocol that can heal itself by generating new keys, so that even if an attacker steals one, the system becomes secure again.
The GPS network is a perfect example of this.
- The Civilian Signal is unencrypted and public. This makes it trivial for an attacker to recreate and broadcast a fake signal.
- The Military Signal on the other hand is encrypted and changes 10.23 million times per second, and doesnt repeat for a week.
Layer 2: The Ticking Quantum Clock
There is a futuristic threat that has security experts worrying today: quantum computers. A powerful computer will one day be able to break all the encryption we use to protect our data. This is called “Q-Day”.
The immediate threat is called “Harvest Now, Decrypt Later (HNDL)”. Adversaries are recording today’s encrypted, secret data and saving it. They can’t read it now, but they are betting that they will be able to decrypt it all in 5-10 years when their quantum computer is built.
To fight this, experts are in a race to build two different solutions.
Path 1: Quantum Key Distribution - This is the perfect security path. It’s not new encryption but a physical way to share keys using the laws of quantum mechanics.
So, how it works is basically the keys are sent on single photons (particles of light). If an eavesdropper tries to intercept and read the photon, the act of measuring it irreversibly disturbs it, which makes the system tamper-evident.
In 2016, China launched its Micius satellite, the world’s first quantum satellite. It acts like a space postman, creating an unhackable, quantum-secured key between two ground stations 1120 km apart. The West is now racing to catch up.
Path 2: Post-Quantum Cryptography (PQC): This is the pragmatic path. It’s not a new, crazy physics experiment. It is just a new family of classical encryption algorithms based on math problems that are believed to be hard for both classical and quantum computers to solve. The U.S. is leading the effort to standardize these algorithms so they can be a drop-in software or firmware replacement.
Recommended Reading
Post-Quantum Now: From AES & RSA to ML-KEM Hybrids
But here is the thing, The Path 1 is perfect but impractical, it offers perfect physics-based security but requires a multi-billion-dollar, entirely new infrastructure of satellites. And the Path 2 is pragmatic but imperfect; it can be deployed today as a software or a firmware update, making it the only viable defense against the HNDL threat.
For the future, the two will likely be used together for broader protection and ultra-secure backbones.
Layer 3: Zero Trust Architecture
The old way of security is broken; once an attacker got inside, they were trusted and could move laterally through the network to steal all the data.
ZTA eliminates implicit trust. It operates on the principle: “never trust, always verify”. This means:
- Verify Explicitly: Every single access request is authenticated, every single time.
- Least Privilege Access: Users are given only the minimum access necessary to do their job.
- Assume Breach: The entire system is designed with the assumption that an attacker is already on the network.
The U.S. Space Force is aggressively implementing ZTA. It’s recognized as the best defense against the #1 cybersecurity threat: insider threats, and the #2 threat: third-party exposure.
Layer 4: AI
This is the smarter threat detection layer. The problem is that satellites and ground stations produce a vast amount of telemetry and network data. It is impossible for human operators to sift through all in real time to find a malicious signal.
So we’re building AI-powered sentries.
- On board Anomaly Detection: This AI trains on the satellite’s normal pattern of life and then flag previously unseen anomalies. It is an active defense that can detect, mitigate, and adapt to threats in real time, without human intervention.
- Autonomous Evasion: AI is also being developed for physical defense against satellite chasers. Researchers are developing highly robust evader policies by training your satellite to escape multiple AIs that are all trained to use different hunting strategies (like one that collides and one that blocks).
Recommended Reading
When AI Turns Criminal: Deepfakes, Voice-Cloning & LLM Malware
Layer 5: The Ultimate Defense
The final layer of security is an architectural one. It’s the principle of resilience. It assumes all other layers can fail. If an attacker does manage to reach this layer, the architecture itself must be able to absorb the loss without failing.
This is the entire philosophy behind the U.S. military’s new Proliferated Warfighter Space Architecture (PWSA).

The main concept is Proliferation. Instead of a few big targets, the PWSA is a herd of thousands of low-cost satellites. This new model is designed to make attacking space economically stupid. The goal is to make the bullet now cost more than the satellite.
This herd defense only works because of one key technology: Optical Inter Satellite Links (OISLs), or lasers. These lasers connect each satellite to its neighbors, creating a dynamic mesh network in space.
If a satellite node is destroyed, or if its ground station is compromised or jammed, the network autonomously reroutes the data.
The Role of International Cooperation
After reading all of this, you might be thinking that everyone is just building their own digital fortresses and preparing for a fight. But there is another, more hopeful side to the story.
Space is a global commons. It doesn’t belong to any one country. The satellites, the data, and the threats all cross national borders.
Because of this, no single nation can secure space on its own. The only way to create a safe and stable space environment is through international cooperation. This is happening in two main ways: first, between governments, and second, between governments and private companies.
Countries Trying to Make Rules
The main forum for international cooperation is the United Nations, specifically the Committee on the Peaceful Uses of Outer Space (UN COPUOS). This is where the world came together in 1967 to write the Outer Space Treaty. The problem, as we have seen, is that the 1967 treaty is outdated. It doesn’t cover cyber attacks or most modern space weapons.
Nations are trying to establish new norms, rules, and principles of responsible behaviors to reduce threats in space. It’s a slow and painful process because all the geopolitical tension on Earth spills over into these discussions, making agreement almost impossible.
Public Private Partnerships
This is where the real progress is happening. The new space race is not just driven by governments; it’s run by private companies like SpaceX, OneWeb, and Amazon.
This has led to the rise of Public-Private Partnerships. Security experts now see these as the most effective way to deal with cyber threats.
The best example of this is the Space ISAC (Information Sharing and Analysis Center)
The Space ISAC is an all-threat security information source for the entire global space industry. It is a central hub where commercial companies, civil agencies like NASA, military branches like the Space Force, and even international partners can all come together in a trusted network.
Their job is to share critical, real-time intelligence. If a member company sees a new, strange attack on its satellites, it can anonymously share the signature of that attack with the ISAC. The ISAC’s analysts can then verify it and push out an alert to all the other members, so that they can patch their systems before they get hit.
Why Cooperation is Still So Hard
While all this sounds great, getting everyone to work together is really difficult. There are a few major roadblocks:
- Geopolitics: Just like at the UN, national interests get in the way. Countries are often hesitant to share their sensitive threat data for fear of revealing their own weaknesses.
- Over Classification: This is a huge problem. Within the U.S. government, for example, many security guides are so outdated that they make it legally impossible to share critical classified information even with close allies.
- Incompatible Systems: It is hard to share data when your allies use completely different systems.
Ultimately, while every nation is building its own defenses, there’s a growing understanding that space security is a team sport.
Conclusion
So, what’s the takeaway from all this?
For most of our lives, space was just… up there. It was for astronauts and sci-fi movies. But now, it’s where we live our digital lives. Your GPS, your bank transaction, your weather report, it all depends on a web of satellites.
And as we have seen, that web is in trouble.
We are still relying on old, dated satellites that can’t ever be patched. At the same time, our new networks are vulnerable to the same cyberattacks we face on Earth.
This isn’t a problem for the future; it is happening right now, above our heads. The race is on to protect the space.
We are building new defenses to do it. We’re designing autonomous cyber defense agents that can fight back on their own and training evader AIs to win a high-speed cat and mouse game against satellite chasers.
It’s a huge, complex challenge. We have to figure out how to keep this vital part of our lives secure, without dragging our earthly conflicts up into the stars.

I can show you how deep the Internet really goes
Discover exposed assets, infrastructure links, and threat surfaces across the global Internet.
Related Posts

August 15, 2025
From Chaos to Control: Kanvas Incident Management Tool

July 25, 2025
The Pyramid of Pain: Beyond the Basics

December 15, 2025
LLM Vulnerabilities: Why AI Models Are the Next Big Attack Surface

October 31, 2025
When AI Turns Criminal: Deepfakes, Voice-Cloning & LLM Malware

October 17, 2025
When Patches Fail: An Analysis of Patch Bypass and Incomplete Security

September 5, 2025
Mapping Dark Web Infrastructure


















