FEATURES / EASM TOOLS
Netlas Private Scanner
Fast, On-Demand Network Scanning
Private Scanner enables precise and fast scanning of any digital assets. Easily analyze services, exposed ports, and vulnerabilities to uncover potential risks within your attack surface.
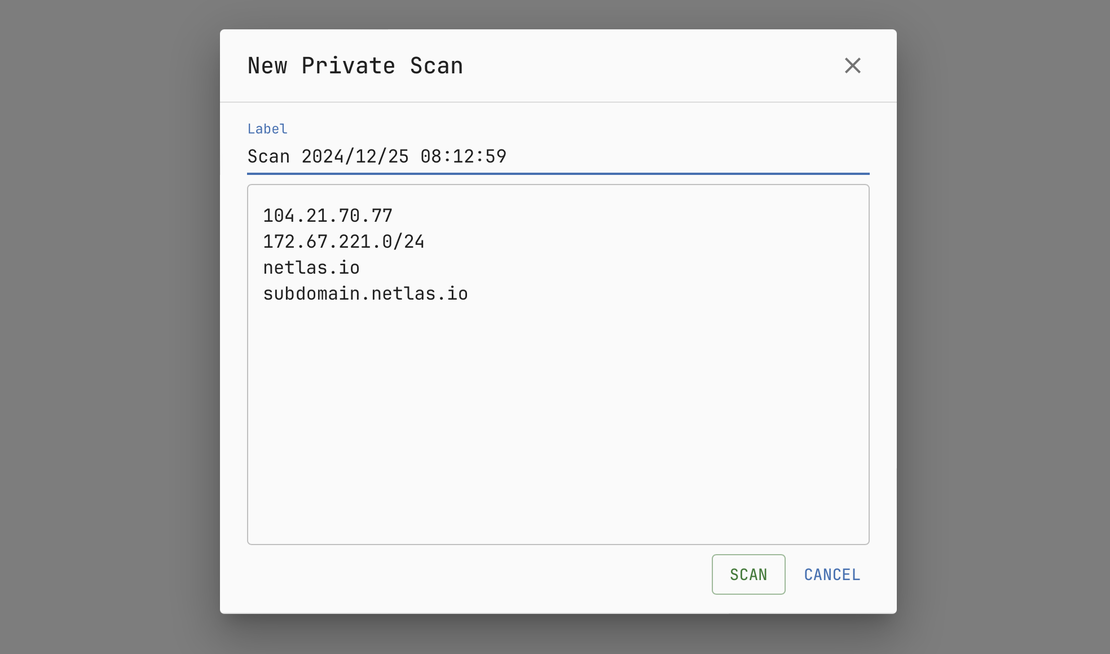
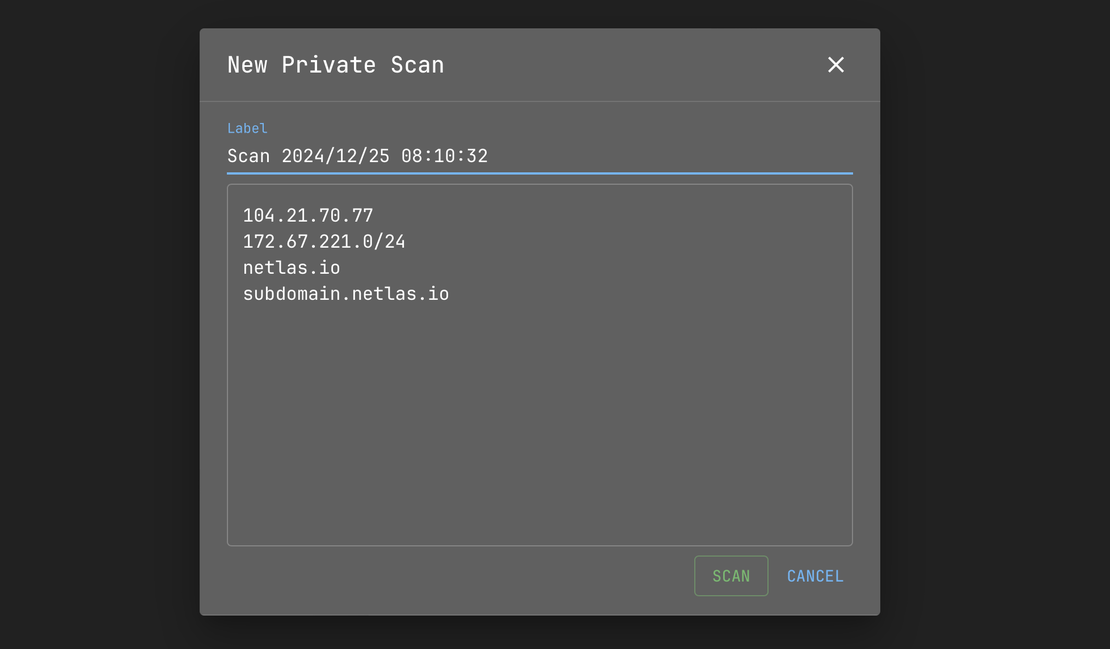
Scan Any Target
From a Single IP to an Entire /16 Network
Netlas Private Scanner enables in-depth analysis of individual IP addresses, domains, and CIDR-notated IP ranges, supporting up to 65,536 targets per scan. Whether you’re examining a single asset or an entire network segment, the tool delivers reliable and detailed insights to help you make well-informed security decisions.
Extensive Port Coverage
Scans 65,536 Ports and Identifies 20+ Protocols
Netlas Private Scanner covers a wide range of ports, including all 65,536 TCP ports and key UDP ports such as 53/DNS, 137/NetBIOS, and 161/SNMP, among others. Detect services running on standard and nonstandard ports, and uncover vulnerabilities across 20+ protocols to gain a comprehensive understanding of your attack surface.
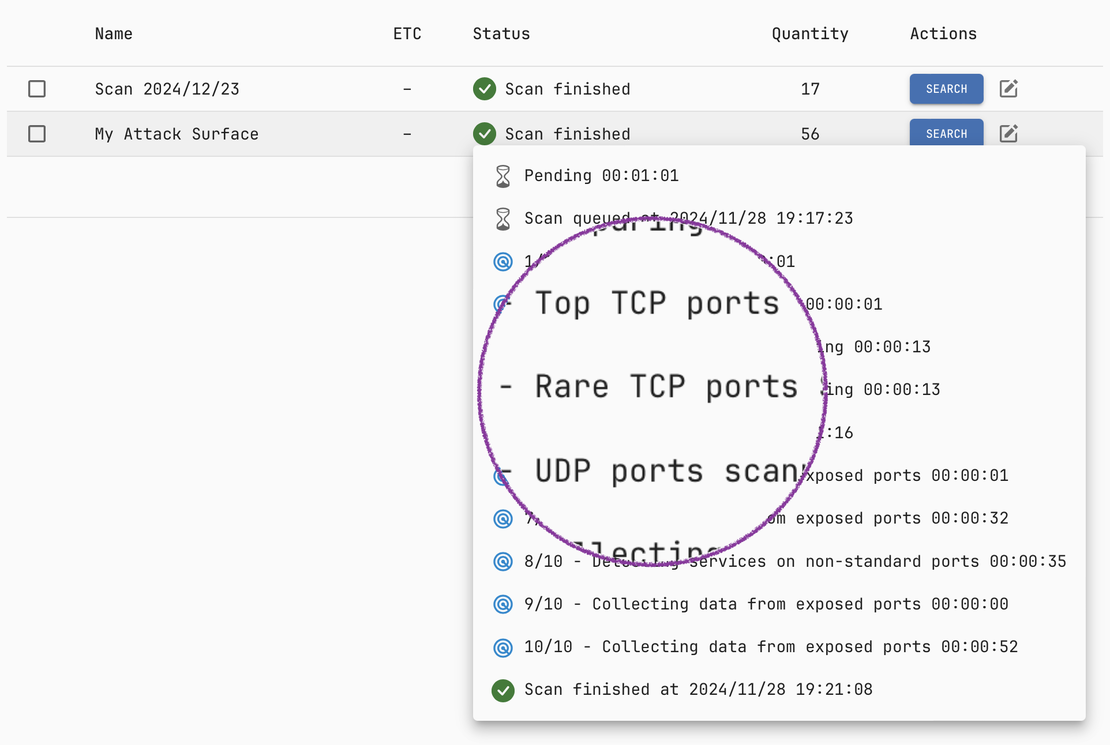
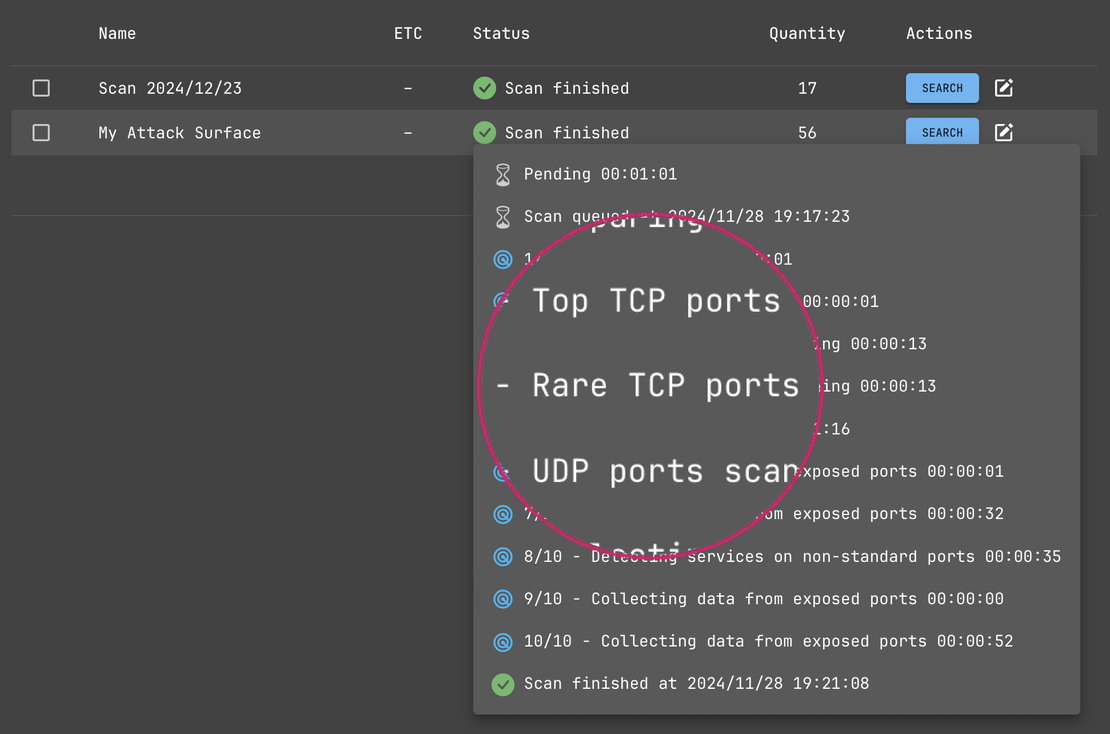
Powered by Netlas’ Proven Scanners
Advanced Scanning Technology Used for Internet Scans
Netlas Private Scanner leverages the same advanced scanning technology used for Netlas’s extensive public internet scans. This means all the benefits of these proven scanners—such as robust technology detection, vulnerability identification, and extended HTTP protocol support—are available for private scans.
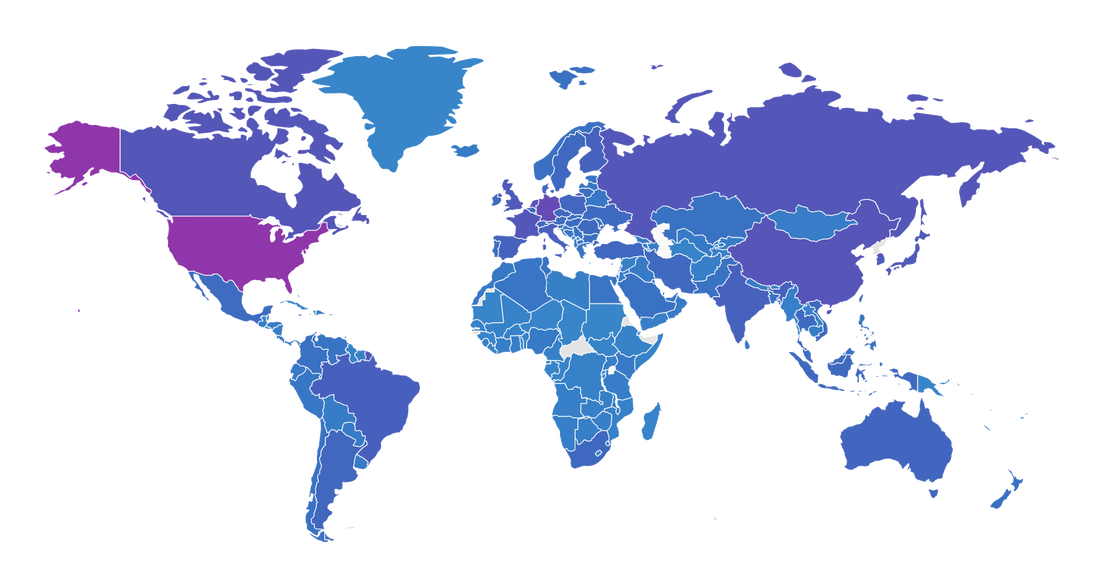
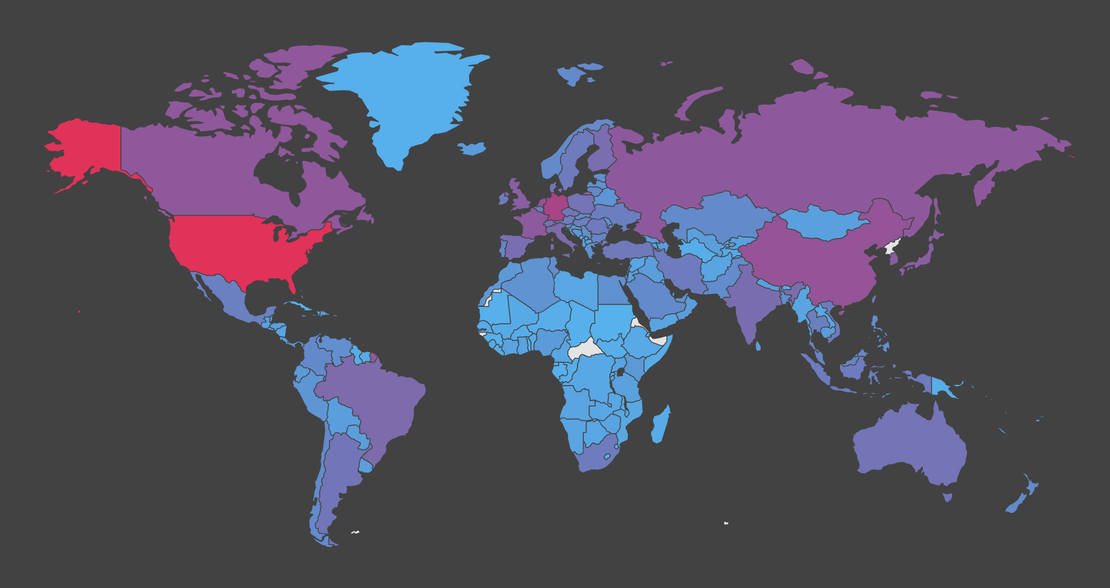
Perfect for External Attack Surface Management
Fast, flexible, and scalable scanning
Netlas Private Scanner is the ideal solution for managing your external attack surface. Thanks to its passive nature, any target can be scanned without disrupting systems. With fast scanning capabilities, even large attack surfaces can be scheduled for daily scans to ensure continuous monitoring. Higher-tier plans offer dedicated scanning agents with fixed IP addresses, making it easy to comply with strict access policies and streamline operations.
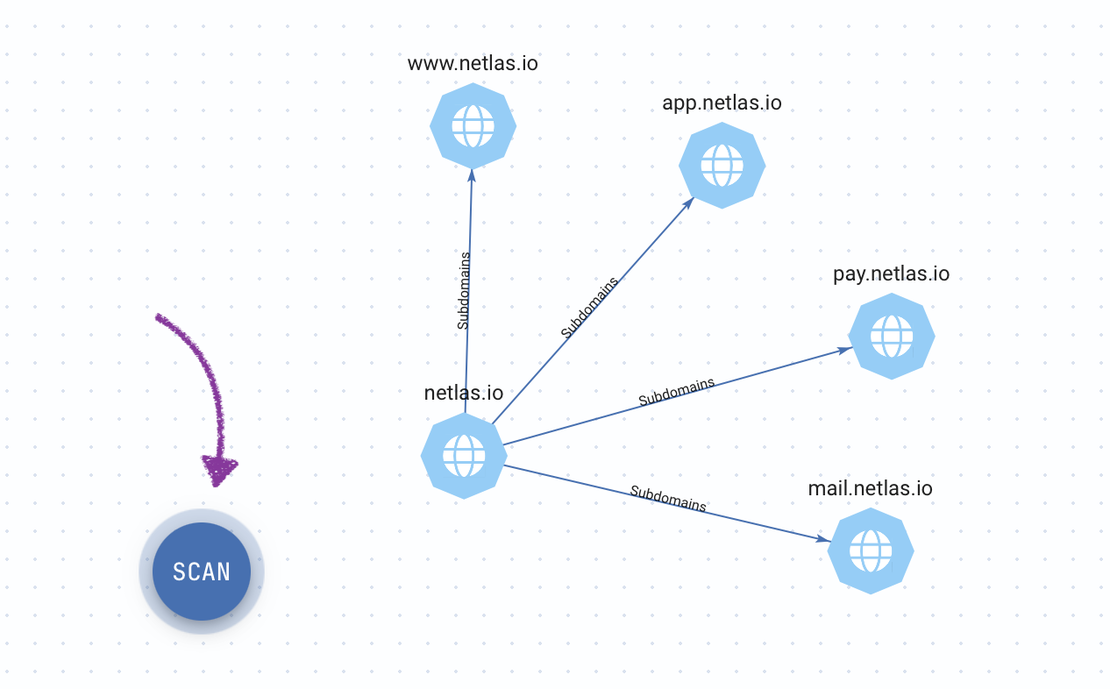
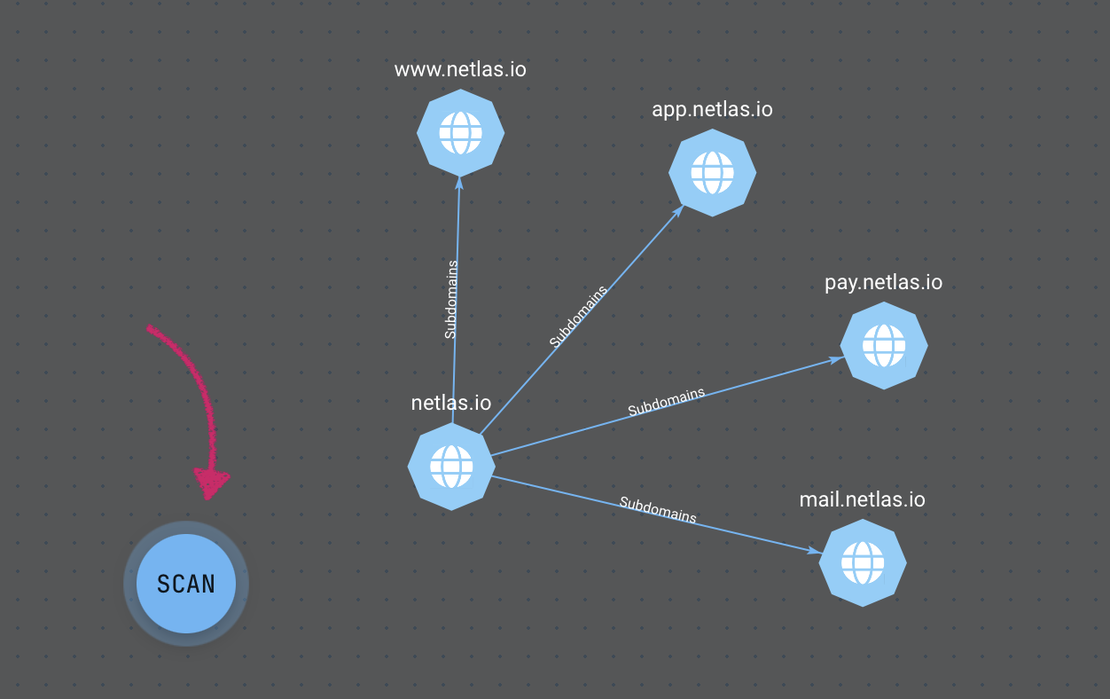
Team Collaboration Features
Work together efficiently
With Netlas Team Access, you can securely share scan results and collaborate seamlessly with your colleagues. Team members can view scan data in read-only mode. Share insights, address vulnerabilities, and work together efficiently on projects to enhance your organization’s security posture.