Today, a significant amount of research in the field of cybersecurity is dedicated to the security of the Internet of Things (IoT) and ensuring the security of critical infrastructure objects. This trend is due to many reasons. Partly because the protection of critical infrastructure objects falls under the close attention of state/national security authorities. Partly because there are some well-known cases of successful attacks where smart devices served as entry points in an organization’s network. And so on.
By using Netlas, you can identify some of the critical infrastructure objects as well as many types of IoT devices. If these devices are accessible via the internet, there is a high likelihood that Netlas has already scanned them. This makes Netlas a valuable tool that can be successfully used in conducting research on the security of critical infrastructure objects and the Internet of Things.
Let’s consider a general algorithm for investigating the security of critical infrastructure objects.
Search for critical infrastructure enterprises
The first approach is to move from general to specific. The algorithm would be as follows:
- Using publicly available information directories, the researcher compiles a list of enterprises of interest in the region.
- Utilizing the Netlas attack surface discovery tool, the researcher identifies the network perimeters of the enterprises of interest. These are often named network ranges, occasionally autonomous systems, and less frequently individual IP addresses.
- The researcher analyzes the results of the scanning conducted in the second step, focusing on the attack surfaces identified. At this stage, filtering based on ports, protocols, or specific protocol fields may be applied to highlight objects whose security will be further assessed.
- The researcher conducts a more detailed examination of the objects identified in the previous step. By using the scanning results, it is often possible to determine the software version, search for known vulnerabilities, assess the validity of authentication procedures, evaluate the cryptographic algorithms used, and assess the reliability of the management protocols. As a result, conclusions can be drawn about the risks of exposing these objects to the Internet.
- Results are summarized and compiled into a report.
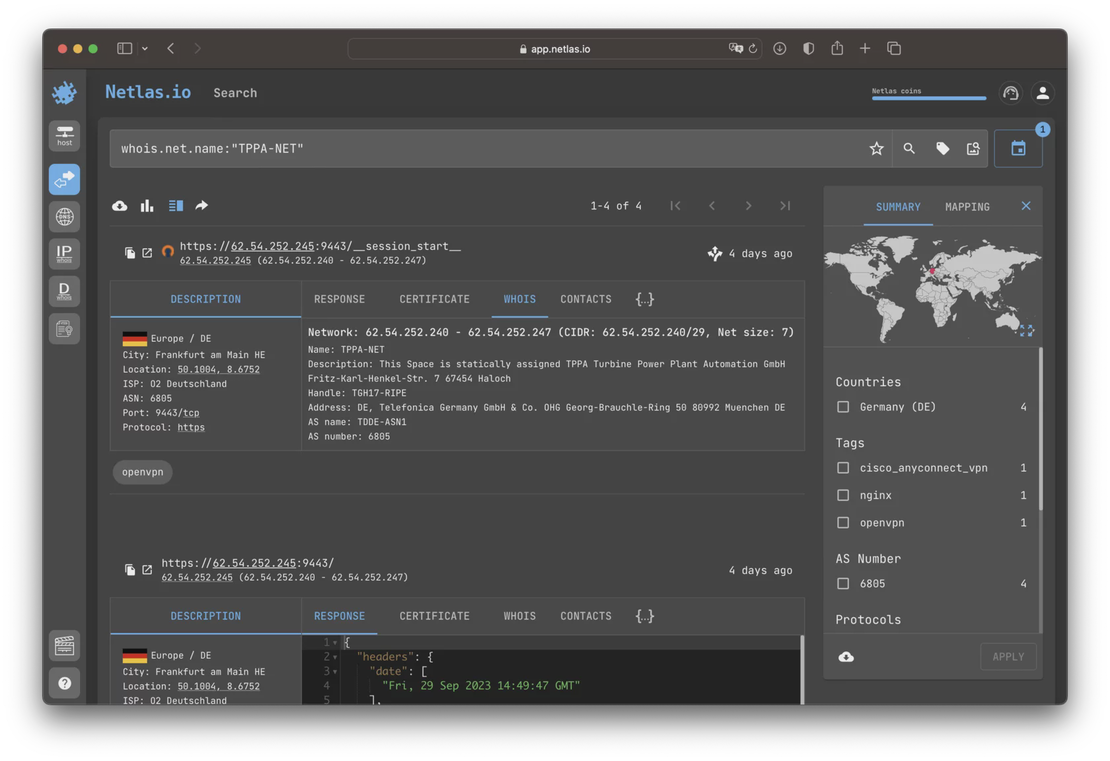
Here is an example query to Netlas that returns the scanning results of one of the critical infrastructure enterprises in Germany:
At the time of writing, Netlas finds two networks with the same name. In the “description” field of both networks, the following information is provided:
This Space is statically assigned TPPA Turbine Power Plant Automation GmbH
An OpenVPN service and a couple of devices for remote access made by Synology were published on the TPPA-NET attack surface.
Search for SCADA and other types industrial devices
The second option is to move from the specific to the general. It involves searching for published SCADA and other industrial devices based on frequently used equipment. The algorithm in this case will be as follows:
- The researcher compiles a list of devices whose security needs to be investigated.
- Search queries are created and a search is conducted in the area of interest.
- If possible, using the WHOIS data provided by Netlas, the researcher identifies the owners of the critical infrastructure objects found.
- The researcher conducts a more detailed examination of the identified critical infrastructure objects, drawing conclusions about the risks of exposing these objects on the Internet.
- Results are summarized and compiled into a report.
Similarly, you can search for IoT devices and other types of devices. Devices with web interfaces are particularly well-suited for this approach. The “http.title” field may contain information such as the device model, manufacturer’s name, software title, and more. However, many industrial devices can be discovered in scanning results using specialized protocols such as Modbus or S7.
Here are a few examples of search queries for finding industrial devices:
modbus.mei_response.objects.product_code:BMX
# Schneider Electric BMX series controllers
http.title:"WinCC"
# Siemens WinCC Series WebUI
\*.banner:Siemens
# Siemens Equipment by any protocolIndeed, one of the challenges in conducting such research is determining device ownership. Often, using WHOIS data, you can only identify the internet service provider rather than the ultimate owner of the device. However, in some cases, even this problem can be addressed.
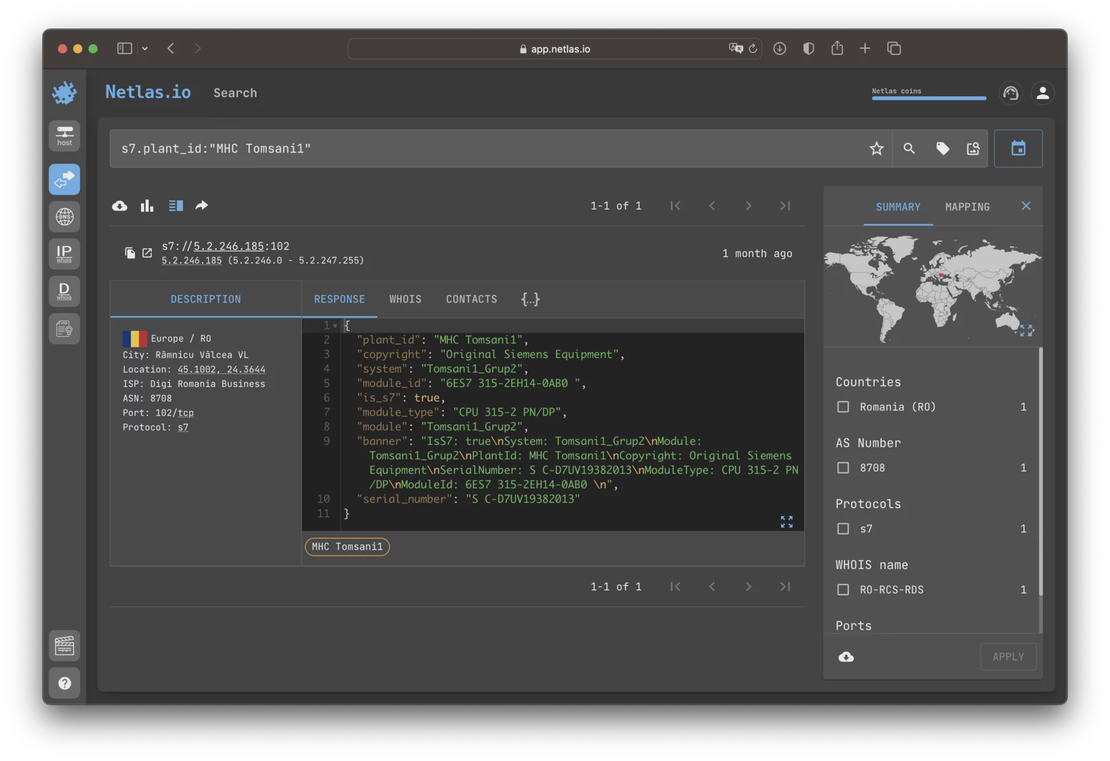
As an example, here is a response from one of the Siemens Advanced S7-300 series controllers collected using the S7 protocol somewhere in Romania:
If you google the value of the “plant_id” field, you will find a web page dedicated to a hydroelectric power station called Tomsani1 on the website of the Institute of Hydroenergy Studies And Projects (ISPH S.A.).