Netlas.io is a non-intrusive scanner. This means that during the scanning process, Netlas.io does not attempt actions beyond what the system is designed for. In other words, there are no attempts at authorization, password guessing, or any non-standard requests. Netlas.io sends requests only to publicly accessible services and saves the responses.
The main advantage of this approach is complete safety. The key benefit of non-intrusive scanning is the ability to scan the entire Internet. Any resource discovered by Netlas.io is already exposed to the public, meaning anyone can access it. Thus, it would be fair to say that Netlas.io is an open-source intelligence platform.
Passive Vulnerability Detection Method
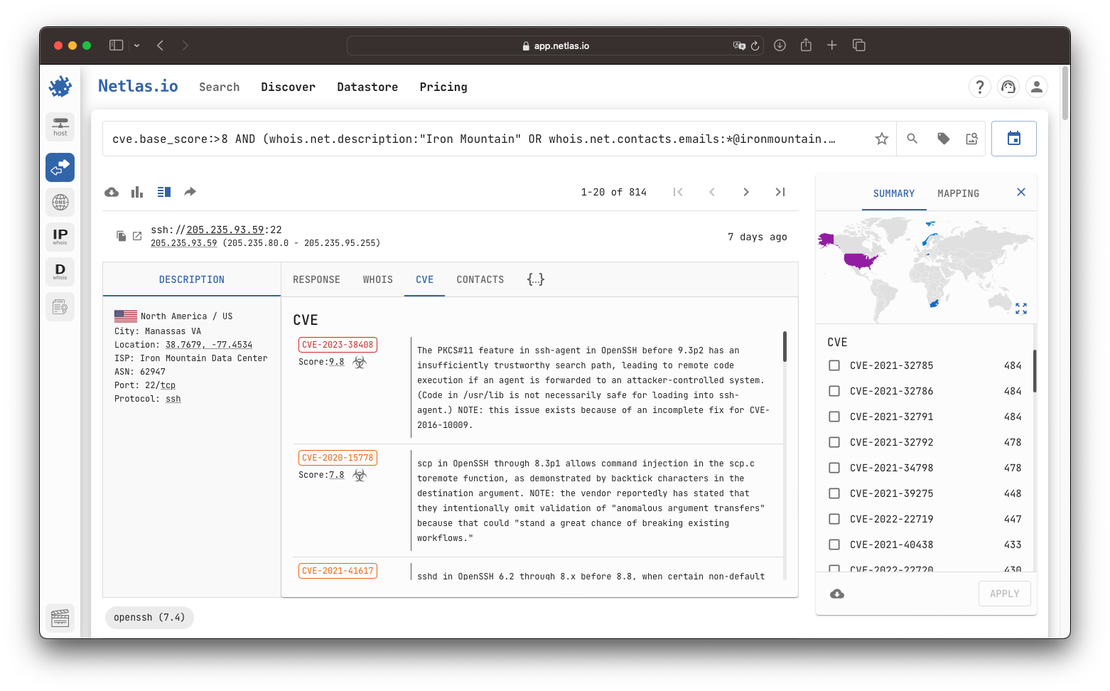
Netlas employs a passive vulnerability detection method, which identifies potential vulnerabilities based on software versions alone. This process begins with response parsing, where Netlas analyzes the responses received from publicly accessible services to detect software and its versions. By examining headers, banners, and other response elements, Netlas accurately determines the software running on the system, achieving this in about two out of three cases. The inability to detect software in 100% of cases often stems from servers obscuring or omitting version information, or using custom headers that do not reveal sufficient details.
Once the software and its version are identified, Netlas maps these details to known vulnerabilities using the comprehensive NIST vulnerability database. By cross-referencing the detected software versions with documented vulnerabilities, Netlas can highlight potential security risks without performing intrusive actions, ensuring both safety and efficiency in its assessments.
Security Assessment by Non-Intrusive Scanning
Therefore, by using Netlas, you can perform security analysis on any information system. The beauty of it is that you do not even need permission since you are not interacting directly with the object of analysis; you are only utilizing the already-gathered data.
For example, you can conduct additional security checks on potential business partners before sharing confidential company data with them. To do this, you can discover the attack surface of the business partner and perform a security analysis: ensuring the absence of critical vulnerabilities, verifying that the software is updated regularly, and confirming adherence to the principle of minimizing the attack surface—meaning critical services and unnecessary information are not exposed publicly.