Netlas data can significantly enhance threat intelligence feed providers and cybersecurity analysts’ algorithms for detecting suspicious hosts.
Score IP reputation based on IP scan results
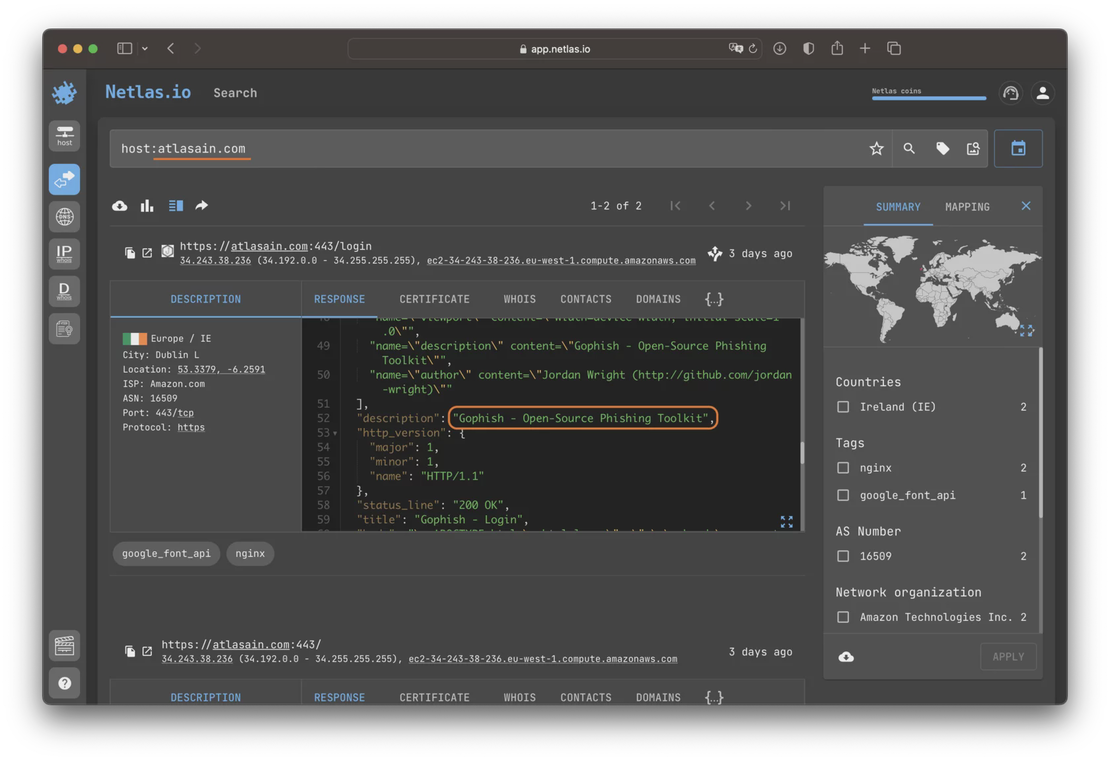
You can rely on Internet scanning data when deciding whether a host is suspicious or not. Netlas can reveal a wide range of information, such as exposed ports, running services, known vulnerabilities, or unexpected behaviors that deviate from what is considered normal or safe. It is possible to identify number of IoCs using scan results. These indicators can include evidence of malware, phishing, spamming activities, or connections to known bad domains. Each IoC contributes to the reputation score of an IP address.
For example, hosts containing numerous vulnerabilities are more likely to be compromised and may host malicious agents or proxy services (e.g., web shells) through which adversaries can carry out attacks. During Internet scanning, Netlas tags vulnerabilities that the scanned applications may be susceptible to if the software version is determined. You can also assess the reputation of a host, for example, based on how frequently the software is updated. To do this, you can compare Netlas scanning results taken at different time intervals.
Search for malicious hosts using IoCs
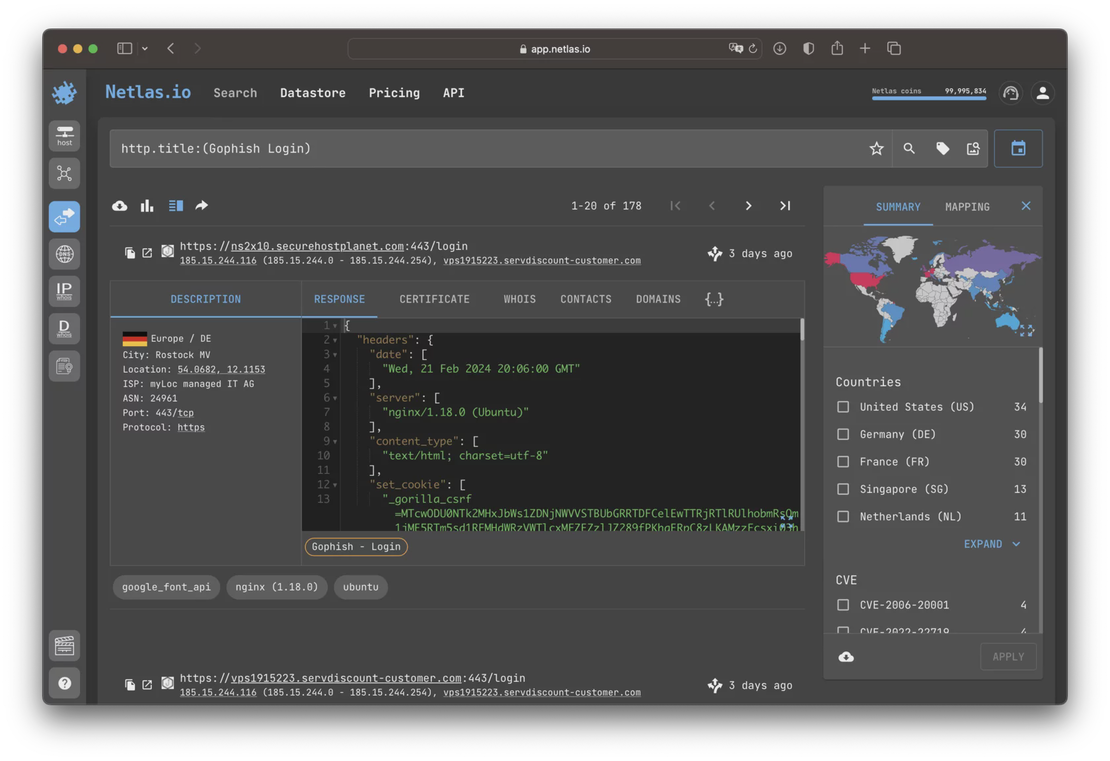
There are numerous reputation scoring algorithms based on the comparison of devices or services. Using available threat intelligence data, you can query Netlas for the scan results of malicious devices, identify distinctive features (create IoCs), and search for similar nodes in the Netlas database. This way, other instances of malicious services or previously unidentified parts of the attackers’ infrastructure can be discovered.
Reputation of networks and ISP
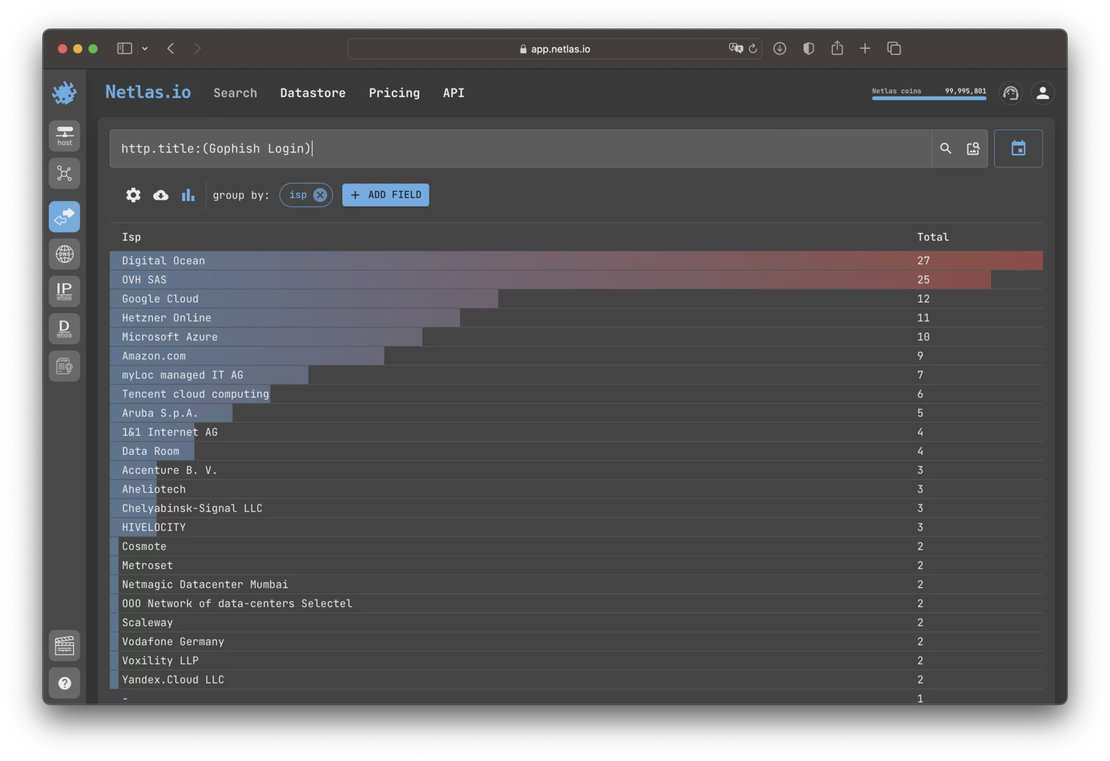
There are also reputation scoring algorithms based on the idea that the reputation of a whole should be defined by the reputations of its parts. In other words, the more malicious hosts there are in a certain network segment, the worse the reputation of that segment should be.
Data on malicious nodes should be obtained from third-party sources, such as threat intelligence feeds. WHOIS and DNS data libraries, which Netlas constantly collects and publishes for its users, become useful in this case. Having data on the relationship between domains and IP addresses, as well as data about the relationship of IP addresses to domain zones, countries, providers, networks, autonomous systems, etc., allows you to score the reputation of these entities.
For example, you can assign reputation levels to countries depending on the concentration of malicious hosts or assign ratings to ISP based on the number of malicious hosts they serve.