What often stays out of the scope of traditional attack surface management? The answer: shadow IT and phishing resources.
The term “shadow IT” generally refers to those parts of the attack surface that are not accounted for by the security division. These elements can be risky, as attacks on them may go unnoticed initially. Similarly, phishing resources, such as fake websites and malicious email domains, exploit human vulnerabilities to deceive individuals into revealing sensitive information or installing malicious software.
Let’s see how you can use Netlas to reveal shadow IT and phishing resources. What should you search for, and how should you analyze the results?
Search for Domains in Other Zones
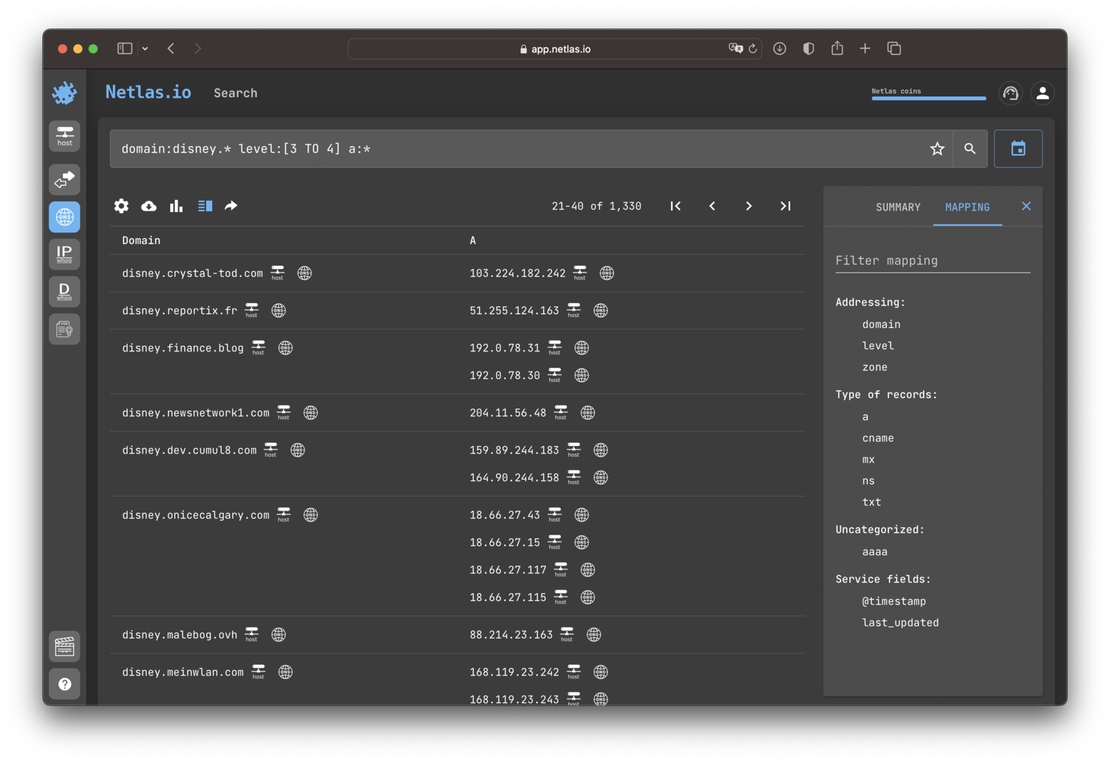
Similar domains, such as netlas.io and netlas.am, may arise in different situations, such as the opening of a regional branch of a company or some experiments. Attackers can also register domains in neighboring zones in order to mislead someone, for example, using email. Using the search syntax features of the Netlas search engine, you can find such domains and determine whether they belong to a known part of the infrastructure or fall under Shadow IT.
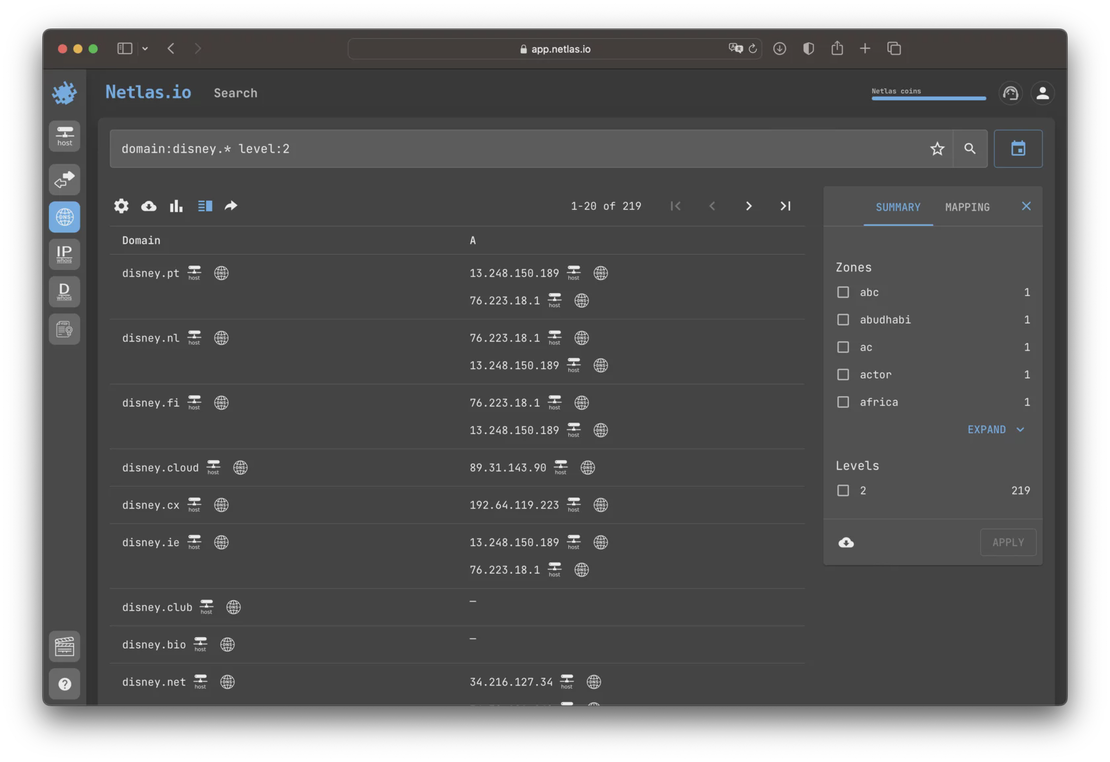
Search for Third-Level Domains
Search for third-level domains can help identify services used by company employees. Cloud services such as CRM, collaborative organization services, and others often create a workspace for their clients using third-level domains. For example, netlas.cloud-service.com. Using Netlas DNS search tool is an effective way to identify such cases.
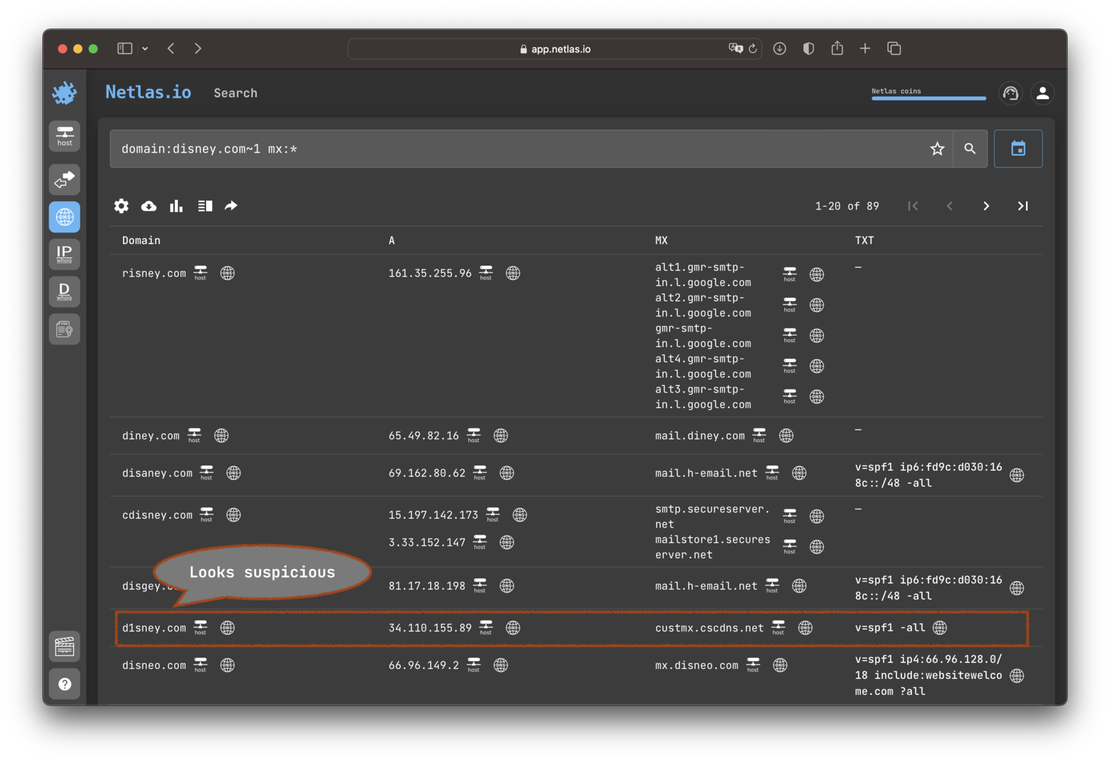
Search for Similar Domains
Phishing resources are oftenly hosted using similar spelling domain names. You can uncover such resources using Netlas fuzzy search feature. Use ~1 or ~2 operator to query domains that differ by 1 or 2 characters, respectively.
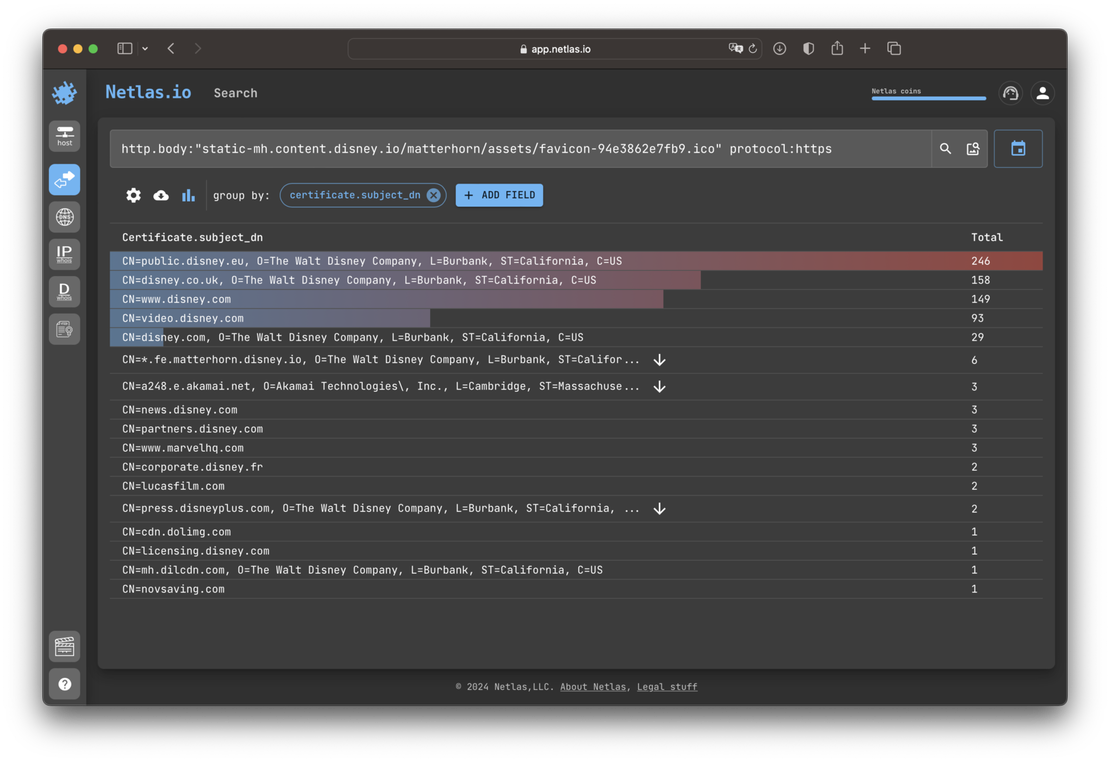
Content Analysis
The content of a website sometimes refers to the branding content of another resource rather than being stored directly. For example, this could be the company’s logo. Netlas responses search tool allows for the detection of such references. You can filter or group responses to find suspicious content usage.
Search for Phishing Web Resources
These same heuristics can be utilized in the search for phishing sites. The challenge lies in the fact that it is quite difficult to distinguish resources falling into the category of Shadow IT from phishing resources without human intervention. Technically, the data of a phishing website often duplicates the data of one of the legitimate sites of a company.
There are numerous other methods for finding phishing sites and Shadow IT using Netlas.io. You can employ fuzzy searching, identifying domain names similar to a specified one, or verify certificates if they suspect a site is mimicking an original resource. Sometimes, positive results are achieved through searching for similar favicons.