About 83% of data breaches involved external actors, with vulnerability exploit as the top attack vector, as shown in Verizon Data Breach Investigations Report 2023.
CVE Filters
Netlas utilizes a passive vulnerability detection method, which means that vulnerabilities are assumed based on the software version alone. This approach is especially useful for penetration testers, bug bounty hunters, and other offensive cybersecurity professionals who use Netlas to identify potentially vulnerable devices within networks of interest. To aid in this, the Responses Search Tool offers a variety of fielters related to vulnerabilities:
cve.base_score
cve.description
cve.exploit_links
cve.has_exploit
cve.name
cve.severity
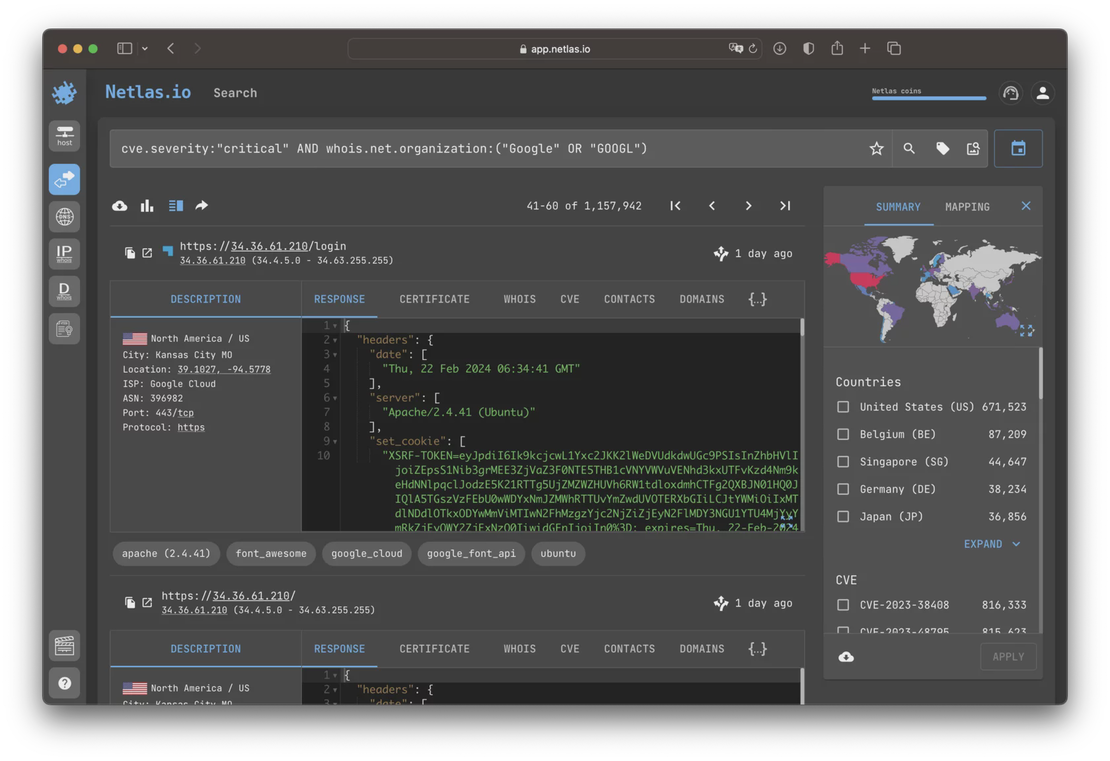
These fields enable users to search for services based on specific vulnerabilities, criticality, or even the availability of published exploits. For instance, the following search will return services hosted on Google networks that are likely susceptible to critical vulnerabilities:
However, it is important to be aware of two significant limitations of this method:
Product Coverage: Netlas labels vulnerabilities only when the product and its version are identified from the response content. Consequently, when using filters from the “cve” group, you will only be able to find vulnerabilities for a limited number of products.
Scanning Frequency: Vulnerability labels are applied during the Internet scanning process. The frequency with which each IP address is scanned varies. Therefore, when using filters from the “cve” group for the most recent vulnerabilities, you will only find devices that have been scanned since the vulnerability was published. Many other devices may still be vulnerable, but they haven’t been scanned since the disclosure of the vulnerability.
Despite these limitations, this method often brings excellent results. The video below demonstrates how an independent bug bounty researcher uses a CVE search in Netlas, combined with open-source tools, to discover and exploit an RCE vulnerability CVE‑2024‑4577 in the Apache web server.
Searching for Vulnerable Devices
Considering the disadvantages of using “cve” filters described above, many of our users take a different approach to search for vulnerabilities using Netlas. Typically, the workflow looks as follows:
- The researcher monitors various sources of vulnerability information. These sources may include developer bulletins, websites aggregating vulnerability data (such as NIST NVD), social networks, and more. Selection criteria vary depending on hacking specialization.
- Upon discovering an interesting vulnerability, researcher creates a search query for devices or software in Netlas, perform a search, and download the results along with contact information to be able to reach out to the system owner.
- Depending on how the query is crafted, an additional step may be required. Often, it is necessary to identify specific software versions that are vulnerable. If the search query created on the previous step filters specific version, then the result is already achieved. However, sometimes it is impossible to determine the version from the information returned by the device. In such cases, the researcher needs to create an additional script to determine the software version. Netlas significantly helps narrow down the scope here. The researcher can run a verification script on the already-filtered list of IP addresses.
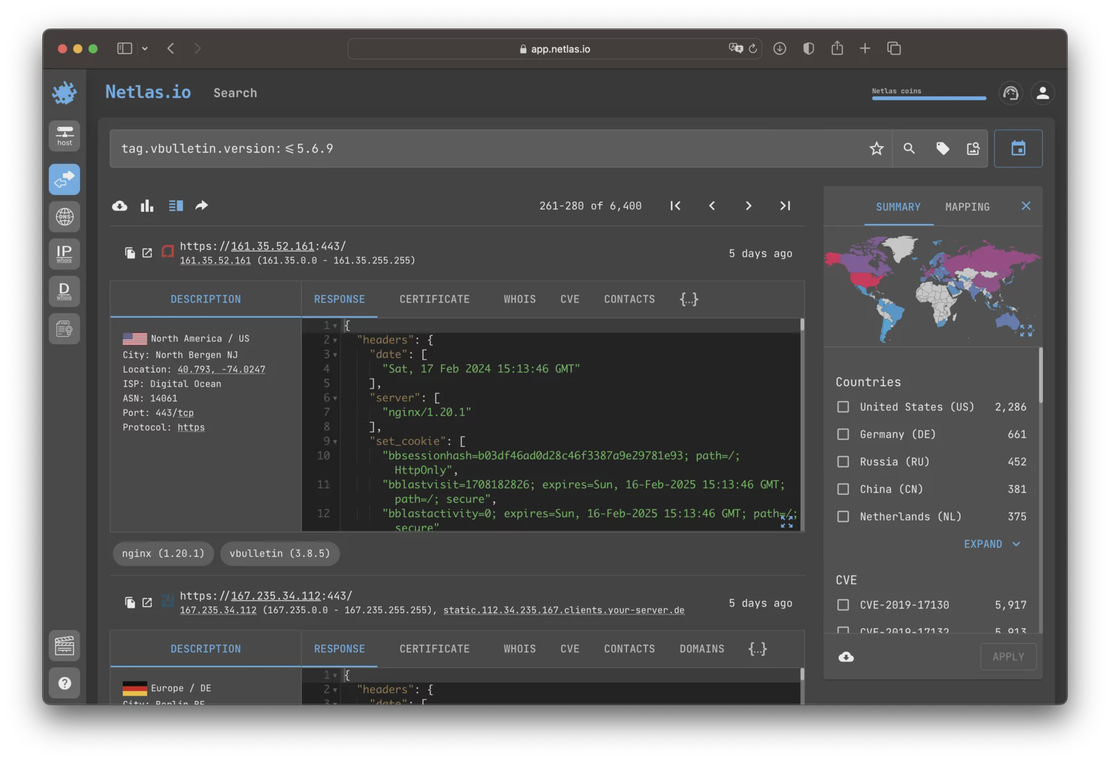
For example, let’s consider CVE‑2023‑25135. The product affected by this vulnerability is vBulletin of certain versions. The Netlas search would look like this:
This search takes into account the version, so there is no need for the development of additional tools.
Below is an example of a search that does not consider the version:
Netlas tags MS Exchange servers but does not determine the software version. In this case, the researcher have use third party tools to detect versions. For MS Exchange, there are several scripts available on GitHub from different developers that address this issue in various ways.
Search Queries for the Most Critical Vulnerabilities
To assist our users, the Netlas team periodically publishes ready-made search queries for the most critical vulnerabilities on social networks. By joining us on one of your chosen social networks, you can significantly save time on developing a search query.