When Patches Fail: An Analysis of Patch Bypass and Incomplete Security
October 17, 2025
14 min read
Introduction
A worrying pattern around incomplete security fixes has been observed: patches that vendors release as fixes often fail to remove the underlying weakness, and attackers are able to bypass those fixes within weeks or months.
The traditional vulnerability management paradigm assumes that vendor-issued security patches provide comprehensive remediation for disclosed vulnerabilities. However, recent researches demonstrates a concerning pattern: 15.5% of security patches require subsequent fixes, with 8.05% classified as incomplete and 4.15% fundamentally incorrect. This phenomenon extends beyond isolated incidents, representing a systematic challenge that undermines the foundational assumptions of modern cybersecurity practices.
A recent comprehensive study analyzing 8100 security patches reveals that 84.6% of unreliable patches are not publicly disclosed as incomplete, creating invisible security gaps that leave organizations vulnerable despite apparent compliance with patching requirements.
This blog will examine that pattern by digging into few high-impact case studies, measuring the operational effects of NVD processing delays, reviewing pre-disclosure intelligence dynamics, and evaluating how AI tools are changing the speed and scale of exploit development. Through comprehensive analysis of recent vulnerability research and threat intelligence reports, we trace the practical root causes that let these bypasses occur and offer pragmatic mitigation advice for vulnerability researchers and security teams.
Case Studies: Critical Patch-Bypass Instances
In the first section of this article, we’ll look at examples of how quickly patches were bypassed in the wild. Six vulnerabilities disclosed this year will serve as examples.
Microsoft SharePoint ToolShell Bypass
Original CVEs: CVE-2025-49704 (CVSS 8.8) and CVE-2025-49706 (CVSS 6.5)
Bypass CVEs: CVE-2025-53770 (CVSS 9.8) and CVE-2025-53771 (CVSS 6.5)
Timeline:
- May 16, 2025: Original ToolShell exploit chain demonstrated at Pwn2Own Berlin
- July 8, 2025: Microsoft patched CVE-2025-49704 and CVE-2025-49706
- July 18, 2025: Active exploitation observed using bypass variants
- July 19-20, 2025: Microsoft assigned new CVE IDs and CISA added CVE-2025-53770 to KEV catalog
Details: CVE-2025-53770 bypassed the deserialization fix for CVE-2025-49704, while CVE-2025-53771 bypassed the authentication fix for CVE-2025-49706. The bypasses exploited the same core logic through alternative paths, enabling unauthenticated remote code execution.
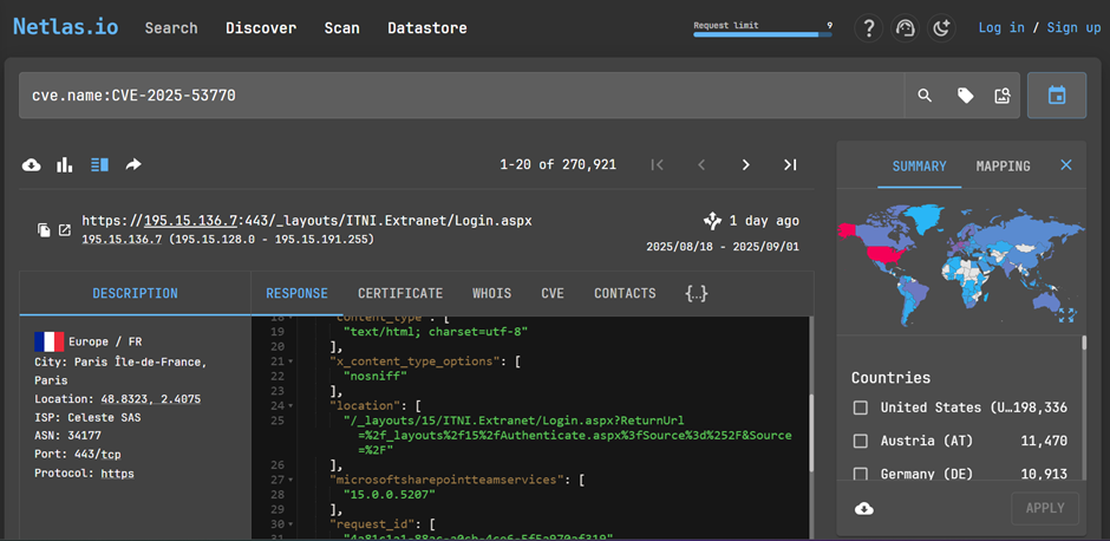
Internet Exposure Assessment: Using Netlas.io search query cve.name:CVE-2025-53770 revealed approximately 270,921 internet-facing SharePoint instances, with the highest concentrations in the United States (198,336 hosts), Austria (11,470 hosts), and Germany (10,913 hosts), demonstrating the massive attack surface available to threat actors exploiting this bypass vulnerability.
SAP NetWeaver Visual Composer Bypass Chain
Original CVE: CVE-2025-31324 (CVSS 10.0)
Residual Risk CVE: CVE-2025-42999 (CVSS 9.1)
Timeline:
- March 2025: Active exploitation begins against Visual Composer endpoints.
- April 24, 2025: SAP published emergency patch for CVE-2025-31324 (authorization bypass only)
- May 13, 2025: Onapsis Research Labs identified that the initial patch was incomplete; SAP released CVE-2025-42999 patch addressing the underlying deserialization vulnerability
- August 15, 2025: Public exploit chaining both vulnerabilities released.
Details: CVE-2025-31324 was initially patched as a missing authorization check in SAP NetWeaver’s Visual Composer /developmentserver/metadatauploader endpoint. However, SAP’s April patch was incomplete—it only added authentication controls without addressing the underlying insecure deserialization vulnerability in the same component.
CVE-2025-42999 represents what Onapsis Research Labs called the “residual risk that remained after patching CVE-2025-31324.” The initial fix stopped unauthorized uploads but left the deserialization flaw that processes uploaded content intact.
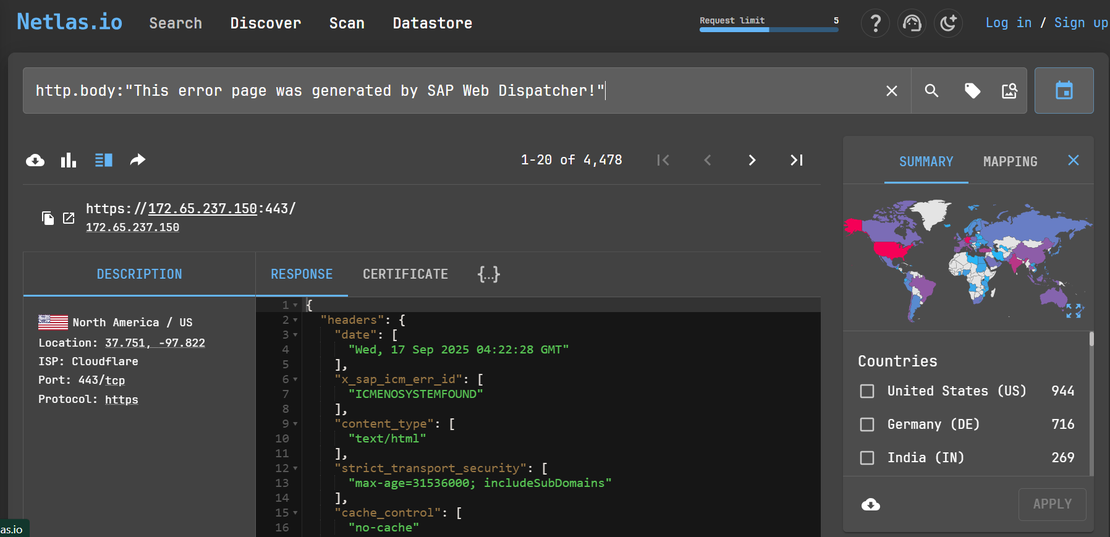
Internet Exposure Assessment: Netlas.io search query http.body:"This error page was generated by SAP Web Dispatcher!" reveals approximately 4,478 internet-facing SAP NetWeaver systems globally vulnerable to the CVE-2025-31324 and CVE-2025-42999 attack chain. The geographic distribution shows significant concentrations in the United States (944 hosts), Germany (716 hosts), and India (269 hosts), indicating substantial enterprise exposure across major business regions where these critical SAP systems typically host mission-critical applications and sensitive corporate data.
Request Your Free 14-Day Trial
Submit a request to try Netlas free for 14 days with full access to all features.
Microsoft NTLM Credential Leakage Bypass
Original CVE: CVE-2025-24054 (CVSS 6.5)
Bypass CVE: CVE-2025-50154 (CVSS 7.5)
Timeline:
- Original vulnerability discovery: 2018 (John Page / hyp3rlinx)
- Microsoft initial response: 2018 - “risk is not severe enough to justify immediate servicing”
- CVE-2025-24054 NVD publication: March 11, 2025
- First active exploitation observed: March 19, 2025 (8 days after patch release)
- Bypass discovery & disclosure: August 12, 2025 (Cymulate Research)
- Bypass CVE assignment: August 12, 2025
Details: The original patch blocked UNC-path icon retrieval from malicious .library-ms files but failed to address Windows Explorer’s automatic icon extraction from remote executables’ embedded .rsrc sections. When a shortcut points to a remote executable (instead of using a remote icon), Explorer automatically downloads the entire binary to extract its icon data, triggering NTLM authentication without user interaction. A comprehensive patch that blocked all automatic remote resource loading from untrusted locations would have prevented this bypass.
Grafana Path Traversal Bypass
Original CVE: CVE-2025-4123 (CVSS 7.6)
Bypass CVE: CVE-2025-6023 (CVSS 7.6)
Timeline:
- Original vulnerability (CVE-2025-4123) disclosure: May 2025
- Initial Grafana patch: May 2025 (versions 12.0.0+security01, 11.6.1+security01)
- Bypass discovery: June 11, 2025 (Hoa X. Nguyen, OPSWAT)
- Bypass patch release: July 17, 2025
Details: The original CVE-2025-4123 patch addressed open redirect vulnerabilities but only implemented basic Content Security Policy (CSP) enhancements without covering client-side path traversal in scripted dashboards. The bypass exploited residual path traversal combined with the open redirect to achieve XSS execution. A comprehensive fix implementing strict CSP with connect-src directives and thorough path validation would have prevented the chained attack vector.
Node.js Windows Path Traversal
Original CVE: CVE-2025-23084 (CVSS 5.6)
Bypass CVE: CVE-2025-27210 (CVSS 7.5)
Timeline:
- NVD publication (original): January, 2025
- NVD publication (bypass): July, 2025
Details: The initial patch normalized file paths to prevent ../ sequences but did not account for Windows reserved device names (e.g., CON, AUX). Attackers used requests like /api/CON/../../secrets to bypass path sanitization and access sensitive files. A comprehensive fix validating against all Windows device names and enforcing absolute path constraints would have prevented this bypass.
These incidents share a clear pattern: each patch addressed a specific symptom but left other avenues unprotected, which attackers quickly found. To understand why this happens, we now examine the underlying causes of patch failures.
Root-Cause Analysis: Why Patches Get Bypassed
The phenomenon of patch bypasses represents one of cybersecurity’s most persistent challenges. Despite vendors releasing security updates, attackers consistently find ways to circumvent these fixes, creating a dangerous cycle where organizations believe they’re protected while remaining vulnerable. Below we will examine the main root causes of the “revival” of seemingly defeated vulnerabilities.
Incomplete Scenario Coverage. Patches frequently address only the specific attack vector reported, leaving alternative exploitation paths untested and unprotected. Academic research reveals that 15.5% of vulnerabilities persist for extended periods before being “actually” fixed, with development teams focusing on demonstrated exploits rather than analyzing broader attack surfaces. For example, in CVE-2025-53770, initial patches secured specific web-part endpoints while leaving alternative SOAP interfaces vulnerable. A large-scale empirical study of over 4,000 security patches found that “security fixes are poorly timed with public disclosures, allowing attackers who monitor open-source repositories to get a jump of weeks to months on targeting not-yet-patched systems”.
Flawed Implementation Logic. Even when developers understand what needs to be fixed, they often implement the solution incorrectly, creating new ways for attackers to bypass the security controls. It’s like installing a new lock but using the wrong type of key or putting it on the wrong door. Studies show that 4.15% of patches are incorrect, often due to “missed edge or exception cases, incorrect conditioning, and implementation errors”. These problems occur when developers focus on fixing the specific reported attack rather than understanding the broader vulnerability class, leading to solutions that work against known exploits but fail against variations.
Surface-Level Symptom Fixes. Organizations frequently address symptoms rather than root causes, creating an illusion of security while fundamental vulnerabilities remain exploitable through different means. Research shows 8.05% of patches are incomplete and 3.87% exhibit both incomplete and regressive characteristics, often because fixes target visible symptoms rather than architectural weaknesses. Root cause analysis studies indicate that “deeper systemic issues beyond the immediate incident” are consistently overlooked, leading to “similar incidents across other systems”.
Inadequate Testing and Validation. Insufficient testing environments consistently fail to catch bypass opportunities that attackers readily discover, representing a critical gap between security theory and practice. Organizations typically take 30-60 days to stabilize patches with a 15-day target for critical ones, but this timeline “often fails to keep pace with rapid scanning and exploitation activities”.
In addition, testing and development-process failures are important causes:
- Limited attack scenario coverage. Testing only against the original exploit method.
- Time Pressure and Resource Constraints. Pressure for rapid patch release consistently results in incomplete solutions that address immediate threats but create new attack vectors. Research shows “instantaneous probability of releasing the patch rising by nearly two and a half times” after public disclosure, but this acceleration often compromises thoroughness. Organizations face competing priorities and limited staff for adequate patch management, while technical debt in legacy systems requires architectural changes exceeding available resources. The “legal obligation to provide timely security patching” creates additional pressure for rapid but potentially incomplete solutions.
- Insufficient edge case validation. Missing Windows-specific attack vectors in cross-platform software.
- Limited Disclosure and Secret Patching. Vendors sometimes provide minimal vulnerability details, hampering proper testing and validation by security teams. This opacity creates information asymmetry favoring attackers who can reverse-engineer fixes while defenders lack validation context. OWASP warns that private disclosures “at the discretion of the organization” can keep critical information hidden, preventing security teams from developing thorough test cases. Disclosure pressure significantly influences patch quality, with reduced transparency about fix scope creating conditions for bypass scenarios. When vendors implement “stealth patches” without adequate technical disclosure, organizations cannot develop comprehensive test cases to identify potential bypasses.
- Inadequate integration testing: Patches work in isolation but fail in complex system interactions.
In addition to these development-related issues, attackers also gain other advantages before patches ever land. In the next section, we examine how early intelligence leaks give them a head start.
Pre-Disclosure Intelligence
Attackers are also working before defenders even know a patch is coming. Research indicates 32.1% of known exploited vulnerabilities were exploited on or before their CVE disclosure day, representing an 8.5% increase from 2024. This acceleration suggests:
- Pre-Disclosure Intelligence: Sophisticated actors obtaining vulnerability information before public release through MAPP leaks or other channels.
- Rapid Weaponization: Enhanced capabilities for converting disclosed vulnerabilities to working exploits.
- Patch Analysis Automation: Systematic reverse engineering of security patches to identify bypass opportunities.
Microsoft’s Active Protections Program (MAPP)
MAPP is a Microsoft-led early vulnerability-sharing initiative providing trusted partners pre-release access to vulnerability info and exploit code with strict NDAs to accelerate patching and defense. However, MAPP has faced abuse concerns:
- The July 2025 SharePoint vulnerability leak triggered on sharing PoC exploit code with Chinese firms.
- Historical violations include the 2012 Hangzhou DPTech NDA breach and suspected 2021 MAPP partner leaks fueling the Hafnium campaign.
- Microsoft now limits early access by geography and enhances compliance monitoring.
While programs like MAPP aim to improve security, their effectiveness depends on strict controls to prevent data leakage that adversaries exploit as pre-disclosure intelligence.
Early Signals from Public Intelligence Channels
Open-source intelligence (OSINT) and social-media intelligence (SOCMINT) analysis often expose vulnerability details before official database entries, providing critical early warnings:
- Studies show 17% of CVEs on Twitter and 51% on Reddit appear before NVD disclosure.
- Social-media discussions can precede official entries by an average of 87 days.
- Exploit confirmations have been tweeted ahead of patches, including major flaws like Heartbleed.
These channels compress the window for defenders, compelling integrated social and repository monitoring as essential for proactive vulnerability research. Even with leaks and OSINT, defenders still rely on official feeds that are slowing down. Next, we examine how NVD processing bottlenecks amplify patch bypass risks.
NVD Processing Delays: Amplifying the Patch-Bypass Problem
Even after a vulnerability is known, defenders depend on data feeds like the National Vulnerability Database (NVD). Unfortunately, NVD has experienced unprecedented operational challenges that have significantly degraded its capacity to process and enrich Common Vulnerabilities and Exposures (CVEs). This deterioration has profound implications for cybersecurity operations, particularly in the detection and mitigation of patch bypass vulnerabilities—sophisticated attack techniques that circumvent security patches and exploit gaps in vulnerability management processes.
Current State of NVD Operations
Since February 2024, the National Vulnerability Database’s capacity to process and enrich CVEs has collapsed, fueling the patch bypass epidemic:
- Backlog explosion: Over 20,000 CVEs await analysis as of November 2024.
- Processing shortfall: 111.9 CVEs processed per day vs. 217 needed to clear the backlog.
- Submission surge: 32% increase in CVE reports in 2024 strained manual workflows.
- Budget cuts: A 12% reduction in NIST funding in 2024 curtailed analytical capacity.
These delays leave CVSS scores, CPE mappings and CWE classifications unavailable for extended periods, crippling automated detection and prioritization.
How NVD Delays Amplify Patch Bypass
The deterioration of NVD processing capabilities has created critical gaps in vulnerability intelligence that attackers can exploit. On average, it takes 44 days from vulnerability disclosure to exploitation in the wild. With NVD processing delays, security teams operate with outdated information and cannot assess and mitigate risks promptly.
By denying timely, enriched intelligence, NVD delays magnify patch bypass threats:
- Extended attack windows: 26.9% of CISA’s Known Exploited Vulnerabilities in H1 2025 remained unanalyzed, giving adversaries a head start.
- Hidden bypass patterns: Missing linkage between original and bypass CVEs obscures systemic patch failures.
- Undermined prioritization: 82% of CVEs with published exploits lack analysis, preventing effective risk ranking.
Many organizations have been forced to implement alternative vulnerability intelligence sources and develop custom risk assessment methodologies. However, these approaches often lack the standardization and comprehensive coverage that the NVD traditionally provided, creating inconsistencies in vulnerability management across the cybersecurity community.
The deterioration of NVD processing capabilities represents a critical weakness in global cybersecurity infrastructure that directly benefits malicious actors seeking to exploit patch bypass vulnerabilities. Without immediate and substantial improvements to processing capacity, the gap between vulnerability disclosure and effective mitigation will continue to widen, creating increasingly dangerous conditions for organizations worldwide.
On top of that, AI is making new exploits nearly instantaneous. In the next section, we explore how AI tools accelerate attacks from discovery to deployment.
AI-Accelerated Exploitation of New CVEs & Zero-Days

Attackers are also getting an AI boost. The cybersecurity landscape has witnessed a dramatic evolution in AI-powered exploitation capabilities, with major developments demonstrating how AI now plays a critical role in accelerating vulnerability exploitation from discovery to mass deployment.
Breakthrough AI Exploitation Frameworks
- CVE-GENIE: Automated CVE-to-Exploit Pipeline
Boston University, UC Santa Barbara, UNSW Sydney et al, researchers developed CVE-GENIE, demonstrating industrial-scale vulnerability reproduction. The framework successfully exploited 51% of 841 tested CVEs at $2.77 per exploit, using four specialized LLM agents for environment reconstruction and exploit generation. This breakthrough proves vulnerability weaponization can be fully automated at unprecedented cost efficiency, transforming cybersecurity economics.
- Villager: AI-Native Penetration Testing
The Villager framework achieved over 10,000 downloads within two months of its July 2025 PyPI release. Combining Kali Linux with DeepSeek AI models, it features 4,201 AI system prompts for automated exploit generation, 24-hour self-destructing containers for evidence elimination, and Model Context Protocol architecture enabling distributed attack coordination. Security researchers describe Villager as “Cobalt Strike’s AI successor,” warning of its potential trajectory from legitimate red-team tool to widespread criminal adoption.
- HexStrike AI: Industrial-Scale Exploitation
Check Point Research documented HexStrike AI’s capability to exploit CVE-2025-7775 (Citrix NetScaler) within 12 hours of disclosure. The platform orchestrates 150+ security tools through autonomous AI agents, compressing tasks that previously required weeks into under 10 minutes of automated execution. Its four-phase automation—reconnaissance, exploitation, persistence, and exfiltration—enables simultaneous attacks against thousands of targets with AI-generated exploit variations.
AI-Enhanced Criminal Operations
Ransomware-as-a-Service Evolution: Anthropic’s threat intelligence revealed sophisticated AI integration across criminal enterprises. A single UK-based operator used Claude to automate complete extortion pipelines affecting 17 organizations, with ransom demands exceeding $500,000 based on AI-driven financial analysis of exfiltrated data. Chinese state-aligned actors integrated Claude across 12 of 14 MITRE ATT&CK tactics during multi-month campaigns against Vietnamese critical infrastructure.
Taken together, these developments mean adversaries can discover, analyze, and weaponize new vulnerabilities in minutes. Defenders need equally advanced tools and processes. The next section outlines enhanced defensive strategies for this AI-driven era.
Enhanced Defensive Recommendations for Security Operations

Modern patch bypass vulnerabilities demand sophisticated defensive strategies that integrate artificial intelligence, threat intelligence, and operational excellence. Based on analysis of recent bypass campaigns and emerging AI-powered exploitation tools, security teams require fundamentally enhanced approaches to vulnerability management and patch validation.
AI-Enhanced Patch Validation Frameworks
Traditional patch testing approaches have proven inadequate against sophisticated bypass techniques demonstrated in cases like Mongoose’s nested query injection and Microsoft SharePoint’s alternative deserialization paths. Advanced validation frameworks now integrate multiple AI-driven analysis layers to identify potential bypass scenarios before production deployment.
Automated Rule Generation and Testing
Research shows that LLM-powered frameworks can automatically create diverse test cases covering expected behaviors, edge cases, and boundary conditions that human testers often miss. Meta’s TestGen-LLM and similar tools demonstrate how natural language processing transforms vulnerability descriptions into executable test scripts, achieving enhanced coverage through mutation-guided test generation that explores alternative exploitation paths.
Academic studies validate this approach: LLMPatch, using multiple AI models including GPT-4, Gemini, Claude3, and Llama3, successfully fixed vulnerabilities in 45-57% of 306 real-world test cases, nearly doubling the 21-35% success rate of traditional automated patching methods. The system’s strength lies in having multiple AI models independently review each patch, catching errors that single-model approaches might miss and providing more reliable validation than any individual AI system working alone.
CVE-GENIE’s four-agent architecture— Processor, Builder, Exploiter, and CTF Verifier — demonstrates comprehensive validation coverage from environment reconstruction through exploit verification. The framework successfully reproduced 51% of 841 tested CVEs at $2.77 per exploit, proving that automated exploit generation can systematically test patch completeness at scale.
Modern validation leverages tools like Autogrep, which automatically generates security rules from vulnerability patches using large language models. The system processes vulnerability patches to create 645 high-quality Semgrep rules across 20 programming languages, achieving effective coverage while filtering out 71.15% of overly specific patterns.
Static analysis tools like CodeQL and Semgrep can explore alternative exploitation paths through data-flow and control-flow analysis. CodeQL’s path queries trace tainted input from sources to sinks, surfacing nested routes that bypass surface-level patches. When combined with comprehensive fuzzing using AFL++ and libFuzzer, these approaches identify residual vulnerabilities that single-layer validation misses. When Mongoose patched CVE-2024-53900, comprehensive validation using recursive query structure testing would have immediately identified the nested
$oroperator bypass scenario.
Recommended Reading
AI-Driven Attack Surface Discovery
Threat Intelligence & Early-Disclosure Monitoring
Intelligence-driven vulnerability management has become essential as exploitation timelines compress and AI tools accelerate threat actor capabilities. Organizations must integrate multiple intelligence sources to detect potential exploits before widespread deployment.
Academic research demonstrates that social media platforms frequently surface vulnerability details before official disclosure. Studies show 17% of CVEs on Twitter and 51% on Reddit appear before NVD publication, with discussions preceding official entries by an average of 87 days.
Organizations implementing automated monitoring of GitHub Gists through platforms like Vulnerability-Lookup can identify proof-of-concept scripts and leaked credentials that correlate with active vulnerability campaigns.
Blue Team Operational Strategies for Patch Bypass Prevention
Effective patch bypass prevention requires risk-based prioritization, comprehensive testing protocols, and integrated security orchestration that accounts for accelerated exploitation timelines.
- Risk-Based Prioritization with Verified Intelligence
Organizations must implement tiered vulnerability management approaches that leverage multiple intelligence sources. Industry data confirms that KEV-listed vulnerabilities are remediated 3.5 times faster than non-KEV vulnerabilities, with median times of 174 days versus 621 days respectively. This dramatic difference demonstrates the effectiveness of centralized vulnerability cataloging and mandatory compliance deadlines.
- EPSS Integration for Predictive Prioritization
The JetBrains TeamCity CVE-2023-42793 case demonstrates the value of Exploit Prediction Scoring System (EPSS) integration. The vulnerability achieved a 94.58% EPSS score weeks before Russian nation-state exploitation, enabling proactive patching for organizations monitoring EPSS feeds. Conversely, Fortinet CVE-2024-21762 maintained near-zero EPSS scores despite active exploitation and CISA KEV listing, highlighting the need for comprehensive intelligence correlation beyond automated scoring systems.
- Asset Classification and Tiered Response
During critical vulnerability campaigns like SharePoint CVE-2025-53770, response effectiveness directly correlates with asset classification maturity. The vulnerability enabled unauthenticated remote code execution through deserialization flaws, with Microsoft confirming active exploitation beginning July 18, 2025. Organizations with pre-established Tier 1 classification for internet-facing SharePoint systems could implement emergency mitigations more rapidly than those requiring real-time asset discovery and impact assessment.
- Orchestration and Real-Time Detection
Automate detection of bypass attempts by correlating SIEM alerts with threat-intel indicators — look for unusual payloads deployments or malformed Referer headers in SharePoint logs. Integrate MISP for IOC sharing and configure Splunk Enterprise Security or IBM QRadar to trigger tickets when post-patch anomalies occur. This ensures defenders catch bypass exploitation as quickly as it emerges.
- Containment via Segmentation and Virtual Patching
When patching must be delayed, immediate containment becomes the priority. Start by tightening network boundaries: micro-segment critical workloads or containers so any exploit stays confined to its original host and cannot pivot laterally across the environment. Complement this with temporary virtual patches at the edge — deploy Web Application Firewall rules that block the specific request patterns tied to the new vulnerability until a production fix can be safely rolled out. Continuous monitoring of these controls ensures they remain effective as threat actors adapt.
By prioritizing high-risk vulnerabilities, rigorously validating patches, and enforcing network and virtual controls, blue teams can reduce “incomplete security” gaps and stay ahead of AI-and script-driven bypass tactics.
Conclusion
The evidence is clear: today’s patch-and-pray model is broken. Security updates still leave exploitable gaps, most bypasses are never disclosed, and AI tools now turn a fresh CVE into a working exploit in minutes while the NVD labors through a months-long backlog. Case studies — from SharePoint’s 270,000 exposed servers to SAP’s residual deserialization flawsn — show how “fixed” bugs quietly reopen as high-impact breaches. To survive this new reality, security programs must pivot from blind trust in vendor patches to an intelligence-driven, AI-assisted approach: monitor early-warning chatter on social code and social media, validate every hotfix with multilayer testing (LLM-generated fuzzing, CodeQL, dynamic analysis), and prioritize remediation using risk signals like KEV and EPSS. Patch once, test twice, watch always — and treat every update as the start of scrutiny, not the end of the job.
Related Posts

July 25, 2025
The Pyramid of Pain: Beyond the Basics

June 25, 2025
Modern Cybercrime: Who’s Behind It and Who’s Stopping It

October 3, 2025
Post-Quantum Now: From AES & RSA to ML-KEM Hybrids

September 12, 2025
Bug Bounty 101: Top 10 Reconnaissance Tools

September 5, 2025
Mapping Dark Web Infrastructure

August 15, 2025
From Chaos to Control: Kanvas Incident Management Tool